|
|
市場調査レポート
商品コード
1769079
産業用制御システム(ICS)セキュリティの世界市場:オファリング別、ソリューション別、サービス別、セキュリティタイプ別、業界別、地域別 - 2030年までの予測Industrial Control System (ICS) Security Market by Offering (Solutions, Services), Solution (Encryption, SIEM, Firewall, IAM, DDoS Mitigation, Antivirus), Security Type (Network, Endpoint, Database), Vertical, and Region - Global Forecast to 2030 |
||||||
カスタマイズ可能
|
|||||||
| 産業用制御システム(ICS)セキュリティの世界市場:オファリング別、ソリューション別、サービス別、セキュリティタイプ別、業界別、地域別 - 2030年までの予測 |
|
出版日: 2025年06月26日
発行: MarketsandMarkets
ページ情報: 英文 446 Pages
納期: 即納可能
|
全表示
- 概要
- 図表
- 目次
産業用制御システム(ICS)セキュリティの市場規模は、2025年の153億5,000万米ドルから2030年には328億9,000万米ドルへと、予測期間中のCAGR16.5%で拡大すると予測されています。
産業組織は、ネットワーク内であってもユーザーやデバイスを自動的に信用しないゼロ・トラスト・アーキテクチャを採用し、ICS環境の安全性を高めています。ゼロ・トラスト・アーキテクチャは、厳格なアクセス・ルール、アイデンティティ・チェック、ネットワーク・セグメンテーションを使用して、脅威の拡散を阻止します。リモートアクセスやサードパーティツールが産業用システムに接続されるようになるにつれ、このアプローチは不可欠になっています。
| 調査範囲 | |
|---|---|
| 調査対象年 | 2019年~2030年 |
| 基準年 | 2024年 |
| 予測期間 | 2025年~2030年 |
| 検討単位 | (100万米ドル/10億米ドル) |
| セグメント | オファリング別、ソリューション別、サービス別、セキュリティタイプ別、業界別、地域別 |
| 対象地域 | 北米、欧州、アジア太平洋、中東・アフリカ、ラテンアメリカ |
ICSセキュリティファイアウォールソリューションは、ITとOT環境間のネットワークトラフィックを監視・制御し、セグメンテーションを実施し、リアルタイムのオペレーションを中断することなく不正アクセスをブロックすることで、産業用制御システムを保護することを目的として構築されています。これらのファイアウォールは、ModbusやDNP3のような産業用プロトコルをサポートし、ディープパケットインスペクションを提供し、制御ネットワーク内の異常の検出と封じ込めを支援します。重要なインフラを標的とするサイバー脅威の増加、規制圧力の高まり(NERC CIP、IEC 62443など)、運用技術とデジタル技術の融合が進んでいることから、ファイアウォールの採用が拡大しています。産業界がIIoT、リモートアクセス、クラウドベースのシステムを取り入れる中、弾力性がありプロトコルを意識したファイアウォールの必要性は、ICSセキュリティ戦略の中核的な要素になりつつあります。
アジア太平洋におけるICSセキュリティの状況は、各国がサイバー脅威の増大、デジタル変革、重要インフラリスクに対応する中で激化しています。日本では、JPCERT/CCが560人以上の参加者を集めて開催した「2025 ICSセキュリティ会議」に見られるように、業界の参加者の増加に支えられ、特にエネルギーや製造業においてOT-IT環境の安全確保に向けた強い機運が高まっています。インドは脅威の急増に直面しており、2024年第1四半期にはサイバー攻撃が261%増加し、83%の組織が前年にインシデントを報告しています。このため、全国的に危機感が高まり、CERT-Inは6時間以内のサイバーインシデント報告を義務付け、電力や運輸などの分野でのセキュリティ対策を加速させています。一方、中国は「メイド・イン・チャイナ2025」政策の下、ICS防衛を強化し、CNITSECが監督する厳格なサイバーセキュリティ法を制定し、脅威検知のためのAIや産業用IoTの利用を増やしています。地域全体としては、官民間の協力関係の拡大、ゼロトラストアーキテクチャの幅広い展開、接続が進む産業システムを保護するためのAI搭載ツールへの投資の拡大が見られます。
当レポートでは、世界の産業用制御システム(ICS)セキュリティ市場について調査し、オファリング別、ソリューション別、サービス別、セキュリティタイプ別、業界別、地域別動向、および市場に参入する企業のプロファイルなどをまとめています。
目次
第1章 イントロダクション
第2章 調査手法
第3章 エグゼクティブサマリー
第4章 重要考察
第5章 市場概要と業界動向
- イントロダクション
- 市場力学
- ユースケース
- バリューチェーン分析
- エコシステム分析
- 特許分析
- ポーターのファイブフォース分析
- 価格分析
- 技術分析
- 生成AIが産業用制御システム(ICS)セキュリティ市場に与える影響
- 顧客のビジネスに影響を与える動向と混乱
- 主要な利害関係者と購入基準
- 関税と規制状況
- 2025年の主な会議とイベント
- 投資と資金調達のシナリオ
- 貿易分析
- 2025年の米国関税の影響- 概要
第6章 ICSセキュリティ市場(オファリング別)
- イントロダクション
- ソリューション
- サービス
第7章 ICSセキュリティ市場(ソリューション別)
- イントロダクション
- マルウェア対策/ウイルス対策
- DDoS緩和
- 暗号化
- ファイアウォール
- アイデンティティとアクセス管理
- 侵入検知・防止システム
- セキュリティと脆弱性管理
- セキュリティ構成管理
- セキュリティ情報とイベント管理
- ホワイトリスト
- その他
第8章 ICSセキュリティ市場(サービス別)
- イントロダクション
- 専門サービス
- マネージドセキュリティサービス
第9章 ICSセキュリティ市場(セキュリティタイプ別)
- イントロダクション
- ネットワークセキュリティ
- エンドポイントセキュリティ
- アプリケーションセキュリティ
- データベースセキュリティ
第10章 ICSセキュリティ市場(業界別)
- イントロダクション
- 電力
- エネルギー・公益事業
- 輸送
- 製造
- その他
第11章 ICSセキュリティ市場(地域別)
- イントロダクション
- 北米
- 北米:マクロ経済見通し
- 北米:ICSセキュリティ市場促進要因
- 米国
- カナダ
- 欧州
- 欧州:マクロ経済見通し
- 欧州:ICSセキュリティ市場促進要因
- 英国
- ドイツ
- イタリア
- その他
- アジア太平洋
- アジア太平洋:マクロ経済見通し
- アジア太平洋:ICSセキュリティ市場促進要因
- 中国
- 日本
- インド
- その他
- 中東・アフリカ
- 中東・アフリカ:マクロ経済見通し
- 中東・アフリカ:ICSセキュリティ市場促進要因
- GCC諸国
- 南アフリカ
- その他
- ラテンアメリカ
- ラテンアメリカ:マクロ経済見通し
- ラテンアメリカ:ICSセキュリティ市場促進要因
- メキシコ
- ブラジル
- その他
第12章 競合情勢
- 主要参入企業の戦略/強み、2022年~2024年
- 収益分析、2020年~2024年
- 市場シェア分析、2024年
- ブランド比較
- 企業評価と財務指標
- 企業評価マトリックス:主要参入企業
- 企業評価マトリックス:スタートアップ企業/中小企業
- 競合シナリオ
第13章 企業プロファイル
- 主要参入企業
- CISCO
- FORTINET
- PALO ALTO NETWORKS
- TENABLE
- HONEYWELL
- CHECK POINT
- ABB
- CYBERARK
- BELDEN
- KASPERSKY
- LOCKHEED MARTIN
- BAE SYSTEMS
- RTX
- TRELLIX
- DARKTRACE
- SOPHOS
- NOZOMI NETWORKS
- CYBERBIT
- FORESCOUT
- その他の企業
- CLAROTY
- DRAGOS
- RADIFLOW
- VERVE INDUSTRIAL PROTECTION
- XAGE SECURITY
- POSITIVE TECHNOLOGY
第14章 隣接市場
第15章 付録
List of Tables
- TABLE 1 USD EXCHANGE RATES, 2020-2024
- TABLE 2 FACTOR ANALYSIS
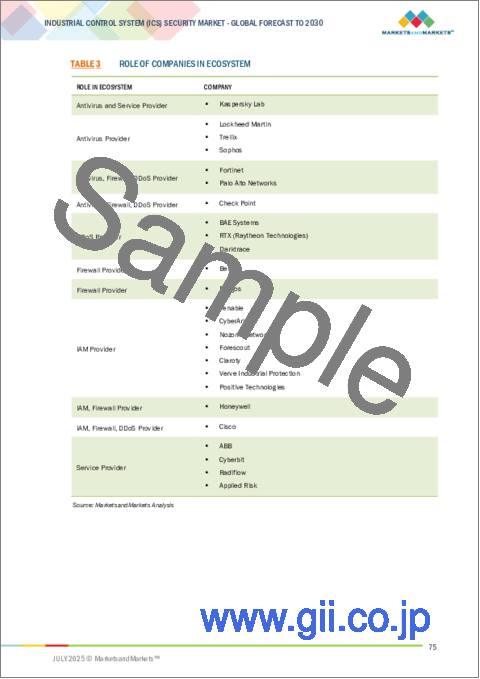
- TABLE 3 ROLE OF COMPANIES IN ECOSYSTEM
- TABLE 4 IMPACT OF PORTER'S FIVE FORCES ON INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY MARKET
- TABLE 5 AVERAGE SELLING PRICE OF SOLUTION, BY KEY PLAYERS, 2024
- TABLE 6 ICS SECURITY MARKET: INDICATIVE PRICING MODEL, BY KEY PLAYER, 2024
- TABLE 7 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS
- TABLE 8 KEY BUYING CRITERIA FOR TOP THREE VERTICALS
- TABLE 9 TARIFF RELATED TO ICS SECURITY SOLUTIONS, 2024
- TABLE 10 NORTH AMERICA: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 11 EUROPE: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 12 ASIA PACIFIC: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 13 MIDDLE EAST & AFRICA: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 14 LATIN AMERICA: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 15 INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY MARKET: DETAILED LIST OF CONFERENCES & EVENTS
- TABLE 16 TABLE 1: US-ADJUSTED RECIPROCAL TARIFF RATES
- TABLE 17 KEY PRODUCT-RELATED TARIFF EFFECTIVE FOR INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY HARDWARE
- TABLE 18 EXPECTED CHANGE IN PRICES AND LIKELY IMPACT ON END-USE MARKET DUE TO TARIFF IMPACT
- TABLE 19 ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 20 ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 21 SOLUTIONS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 22 SOLUTIONS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 23 SERVICES: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 24 SERVICES: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 25 ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 26 ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 27 ANTIMALWARE/ANTIVIRUS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 28 ANTIMALWARE/ANTIVIRUS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 29 DDOS MITIGATION: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 30 DDOS MITIGATION: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 31 ENCRYPTION: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 32 ENCRYPTION: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 33 FIREWALL: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 34 FIREWALL: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 35 IDENTITY & ACCESS MANAGEMENT: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 36 IDENTITY & ACCESS MANAGEMENT: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 37 INTRUSION DETECTION & PREVENTION SYSTEM: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 38 INTRUSION DETECTION & PREVENTION SYSTEM: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 39 SECURITY & VULNERABILITY MANAGEMENT: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 40 SECURITY & VULNERABILITY MANAGEMENT: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 41 SECURITY CONFIGURATION MANAGEMENT: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 42 SECURITY CONFIGURATION MANAGEMENT: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 43 EVENT LOGS AND DESCRIPTIONS
- TABLE 44 SECURITY INFORMATION & EVENT MANAGEMENT: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 45 SECURITY INFORMATION & EVENT MANAGEMENT: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 46 WHITELISTING: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 47 WHITELISTING: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 48 OTHER SOLUTIONS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 49 OTHER SOLUTIONS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 50 ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 51 ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 52 ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 53 ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 54 PROFESSIONAL SERVICES: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 55 PROFESSIONAL SERVICES: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 56 CONSULTING & INTEGRATION SERVICES: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 57 CONSULTING & INTEGRATION SERVICES: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 58 SUPPORT & MAINTENANCE SERVICES: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 59 SUPPORT & MAINTENANCE SERVICES: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 60 TRAINING & DEVELOPMENT SERVICES: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 61 TRAINING & DEVELOPMENT SERVICES: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 62 INCIDENT RESPONSE SERVICES: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 63 INCIDENT RESPONSE SERVICES: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 64 MANAGED SECURITY SERVICES: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 65 MANAGED SECURITY SERVICES: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 66 ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 67 ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 68 NETWORK SECURITY: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 69 NETWORK SECURITY: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 70 ENDPOINT SECURITY: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 71 ENDPOINT SECURITY: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 72 APPLICATION SECURITY: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 73 APPLICATION SECURITY: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 74 DATABASE SECURITY: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 75 DATABASE SECURITY: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 76 ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 77 ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 78 ICS SECURITY MARKET, BY POWER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 79 ICS SECURITY MARKET, BY POWER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 80 POWER: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 81 POWER: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 82 NUCLEAR POWER PLANTS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 83 NUCLEAR POWER PLANTS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 84 THERMAL AND HYDROPOWER PLANTS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 85 THERMAL AND HYDROPOWER PLANTS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 86 RENEWABLE ENERGY POWER PLANTS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 87 RENEWABLE ENERGY POWER PLANTS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 88 POWER GRID: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
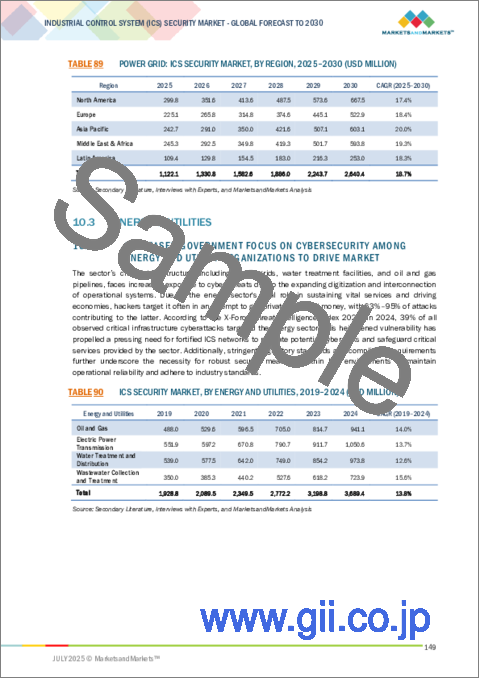
- TABLE 89 POWER GRID: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 90 ICS SECURITY MARKET, BY ENERGY AND UTILITIES, 2019-2024 (USD MILLION)
- TABLE 91 ICS SECURITY MARKET, ENERGY AND UTILITIES, 2025-2030 (USD MILLION)
- TABLE 92 ENERGY & UTILITIES: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 93 ENERGY & UTILITIES: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 94 OIL & GAS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 95 OIL & GAS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 96 ELECTRIC POWER TRANSMISSION: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 97 ELECTRIC POWER TRANSMISSION: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 98 WATER TREATMENT & DISTRIBUTION: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 99 WATER TREATMENT & DISTRIBUTION: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 100 WASTEWATER COLLECTION & TREATMENT: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 101 WASTEWATER COLLECTION & TREATMENT: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 102 ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 103 ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 104 TRANSPORTATION: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 105 TRANSPORTATION: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 106 AIRPORTS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 107 AIRPORTS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 108 SEAPORTS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 109 SEAPORTS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 110 RAILWAYS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 111 RAILWAYS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 112 OTHER TRANSPORTATION APPLICATIONS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 113 OTHER TRANSPORTATION APPLICATIONS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 114 ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 115 ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 116 MANUFACTURING: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 117 MANUFACTURING: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 118 CHEMICAL & MATERIALS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 119 CHEMICAL & MATERIALS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 120 AUTOMOTIVE: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 121 AUTOMOTIVE: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 122 MINING UNITS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 123 MINING UNITS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 124 PAPER & PULP: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 125 PAPER & PULP: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 126 OTHER MANUFACTURING APPLICATIONS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 127 OTHER MANUFACTURING APPLICATIONS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 128 ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 129 ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 130 OTHER VERTICALS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 131 OTHER VERTICALS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 132 COMMERCIAL BUILDINGS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 133 COMMERCIAL BUILDINGS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 134 COMMUNICATION SYSTEMS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 135 COMMUNICATION SYSTEMS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 136 HEALTHCARE: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 137 HEALTHCARE: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 138 OTHER APPLICATIONS: ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 139 OTHER APPLICATIONS: ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 140 ICS SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 141 ICS SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 142 NORTH AMERICA: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 143 NORTH AMERICA: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 144 NORTH AMERICA: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 145 NORTH AMERICA: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 146 NORTH AMERICA: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 147 NORTH AMERICA: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 148 NORTH AMERICA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 149 NORTH AMERICA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 150 NORTH AMERICA: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 151 NORTH AMERICA: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 152 NORTH AMERICA: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 153 NORTH AMERICA: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 154 NORTH AMERICA: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 155 NORTH AMERICA: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 156 NORTH AMERICA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 157 NORTH AMERICA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 158 NORTH AMERICA: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 159 NORTH AMERICA: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 160 NORTH AMERICA: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 161 NORTH AMERICA: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 162 NORTH AMERICA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 163 NORTH AMERICA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 164 NORTH AMERICA: ICS SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 165 NORTH AMERICA: ICS SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 166 US: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 167 US: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 168 US: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 169 US: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 170 US: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 171 US: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 172 US: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 173 US: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 174 US: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 175 US: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 176 US: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 177 US: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 178 US: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 179 US: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 180 US: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 181 US: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 182 US: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 183 US: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 184 US: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 185 US: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 186 US: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 187 US: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 188 CANADA: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 189 CANADA: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 190 CANADA: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 191 CANADA: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 192 CANADA: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 193 CANADA: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 194 CANADA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 195 CANADA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 196 CANADA: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 197 CANADA: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 198 CANADA: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 199 CANADA: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 200 CANADA: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 201 CANADA: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 202 CANADA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 203 CANADA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 204 CANADA: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 205 CANADA: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 206 CANADA: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 207 CANADA: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 208 CANADA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 209 CANADA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 210 EUROPE: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 211 EUROPE: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 212 EUROPE: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 213 EUROPE: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 214 EUROPE: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 215 EUROPE: ICS SECURITY SERVICES MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 216 EUROPE: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 217 EUROPE: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 218 EUROPE: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 219 EUROPE: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 220 EUROPE: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 221 EUROPE: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 222 EUROPE: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 223 EUROPE: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 224 EUROPE: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 225 EUROPE: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 226 EUROPE: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 227 EUROPE: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 228 EUROPE: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 229 EUROPE: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 230 EUROPE: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 231 EUROPE: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 232 EUROPE: ICS SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 233 EUROPE: ICS SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 234 UK: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 235 UK: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 236 UK: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 237 UK: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 238 UK: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 239 UK: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 240 UK: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 241 UK: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 242 UK: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 243 UK: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 244 UK: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 245 UK: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 246 UK: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 247 UK: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 248 UK: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 249 UK: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 250 UK: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 251 UK: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 252 UK: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 253 UK: ICS SECURITY, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 254 UK: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 255 UK: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 256 GERMANY: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 257 GERMANY: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 258 GERMANY: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 259 GERMANY: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 260 GERMANY: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 261 GERMANY: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 262 GERMANY: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 263 GERMANY: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 264 GERMANY: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 265 GERMANY: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 266 GERMANY: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 267 GERMANY: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 268 GERMANY: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 269 GERMANY: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 270 GERMANY: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 271 GERMANY: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 272 GERMANY: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 273 GERMANY: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 274 GERMANY: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 275 GERMANY: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 276 GERMANY: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 277 GERMANY: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 278 ITALY: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 279 ITALY: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 280 ITALY: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 281 ITALY: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 282 ITALY: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 283 ITALY: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 284 ITALY: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 285 ITALY: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 286 ITALY: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 287 ITALY: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 288 ITALY: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 289 ITALY: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 290 ITALY: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 291 ITALY: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 292 ITALY: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 293 ITALY: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 294 ITALY: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 295 ITALY: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 296 ITALY: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 297 ITALY: ICS SECURITY MARKET , BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 298 ITALY: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 299 ITALY: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 300 REST OF EUROPE: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 301 REST OF EUROPE: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 302 REST OF EUROPE: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 303 REST OF EUROPE: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 304 REST OF EUROPE: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 305 REST OF EUROPE: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 306 REST OF EUROPE: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 307 REST OF EUROPE: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 308 REST OF EUROPE: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 309 REST OF EUROPE: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 310 REST OF EUROPE: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 311 REST OF EUROPE: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 312 REST OF EUROPE: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 313 REST OF EUROPE: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 314 REST OF EUROPE: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 315 REST OF EUROPE: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 316 REST OF EUROPE: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 317 REST OF EUROPE: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 318 REST OF EUROPE: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 319 REST OF EUROPE: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 320 REST OF EUROPE: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 321 REST OF EUROPE: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 322 ASIA PACIFIC: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 323 ASIA PACIFIC: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 324 ASIA PACIFIC: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 325 ASIA PACIFIC: ICS SECURITY SOLUTIONS MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 326 ASIA PACIFIC: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 327 ASIA PACIFIC: ICS SECURITY SERVICES MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 328 ASIA PACIFIC: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 329 ASIA PACIFIC: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 330 ASIA PACIFIC: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 331 ASIA PACIFIC: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 332 ASIA PACIFIC: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 333 ASIA PACIFIC: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 334 ASIA PACIFIC: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 335 ASIA PACIFIC: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 336 ASIA PACIFIC: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 337 ASIA PACIFIC: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 338 ASIA PACIFIC: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 339 ASIA PACIFIC: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 340 ASIA PACIFIC: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 341 ASIA PACIFIC: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 342 ASIA PACIFIC: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 343 ASIA PACIFIC: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 344 ASIA PACIFIC: ICS SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 345 ASIA PACIFIC: ICS SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 346 CHINA: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 347 CHINA: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 348 CHINA: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 349 CHINA: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 350 CHINA: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 351 CHINA: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 352 CHINA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 353 CHINA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 354 CHINA: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 355 CHINA: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 356 CHINA: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 357 CHINA: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 358 CHINA: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 359 CHINA: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 360 CHINA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 361 CHINA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 362 CHINA: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 363 CHINA: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 364 CHINA: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 365 CHINA: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 366 CHINA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 367 CHINA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 368 JAPAN: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 369 JAPAN: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 370 JAPAN: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 371 JAPAN: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 372 JAPAN: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 373 JAPAN: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 374 JAPAN: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 375 JAPAN: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 376 JAPAN: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 377 JAPAN: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 378 JAPAN: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 379 JAPAN: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 380 JAPAN: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 381 JAPAN: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 382 JAPAN: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 383 JAPAN: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 384 JAPAN: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 385 JAPAN: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 386 JAPAN: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 387 JAPAN: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 388 JAPAN: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 389 JAPAN: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 390 INDIA: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 391 INDIA: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 392 INDIA: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 393 INDIA: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 394 INDIA: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 395 INDIA: ICS SECURITY SERVICES MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 396 INDIA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 397 INDIA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 398 INDIA: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 399 INDIA: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 400 INDIA: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 401 INDIA: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 402 INDIA: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 403 INDIA: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 404 INDIA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 405 INDIA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 406 INDIA: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 407 INDIA: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 408 INDIA: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 409 INDIA: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 410 INDIA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 411 INDIA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 412 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 413 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 414 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 415 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 416 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 417 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 418 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 419 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 420 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 421 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 422 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 423 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 424 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 425 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 426 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 427 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 428 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 429 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 430 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 431 REST OF ASIA PACIFIC: ICS SECURITY MARKET , BY MANUFACTURING, BY APPLICATION, 2025-2030 (USD MILLION)
- TABLE 432 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 433 REST OF ASIA PACIFIC: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 434 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 435 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 436 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 437 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 438 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 439 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 440 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 441 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 442 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 443 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 444 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 445 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 446 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 447 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 448 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 449 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 450 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 451 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 452 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 453 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 454 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 455 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 456 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 457 MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 458 GCC COUNTRIES: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 459 GCC COUNTRIES: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 460 GCC COUNTRIES: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 461 GCC COUNTRIES: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 462 GCC COUNTRIES: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 463 GCC COUNTRIES: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 464 GCC COUNTRIES: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 465 GCC COUNTRIES: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 466 GCC COUNTRIES: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 467 GCC COUNTRIES: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 468 GCC COUNTRIES: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 469 GCC COUNTRIES: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 470 GCC COUNTRIES: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 471 GCC COUNTRIES: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 472 GCC COUNTRIES: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 473 GCC COUNTRIES: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 474 GCC COUNTRIES: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 475 GCC COUNTRIES: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 476 GCC COUNTRIES: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 477 GCC COUNTRIES: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 478 GCC COUNTRIES: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 479 GCC COUNTRIES: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 480 GCC COUNTRIES: ICS SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 481 GCC COUNTRIES: ICS SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 482 KSA: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 483 KSA: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 484 KSA: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 485 KSA: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 486 KSA: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 487 KSA: ICS SECURITY SERVICES MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 488 KSA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 489 KSA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 490 KSA: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 491 KSA: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 492 KSA: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 493 KSA: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 494 KSA: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 495 KSA: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 496 KSA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 497 KSA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 498 KSA: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 499 KSA: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 500 KSA: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 501 KSA: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 502 KSA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 503 KSA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 504 UAE: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 505 UAE: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 506 UAE: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 507 UAE: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 508 UAE: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 509 UAE: ICS SECURITY SERVICES MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 510 UAE: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 511 UAE: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 512 UAE: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 513 UAE: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 514 UAE: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 515 UAE: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 516 UAE: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 517 UAE: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 518 UAE: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 519 UAE: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 520 UAE: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 521 UAE: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 522 UAE: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 523 UAE: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 524 UAE: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 525 UAE: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 526 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 527 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 528 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 529 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 530 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 531 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 532 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 533 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 534 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 535 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 536 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 537 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 538 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 539 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 540 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 541 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY ENERGY & UTILITIES VERTICALS, 2025-2030 (USD MILLION)
- TABLE 542 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 543 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 544 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 545 REST OF GCC COUNTRIES: ICS SECURITY MARKET, , BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 546 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 547 REST OF GCC COUNTRIES: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 548 SOUTH AFRICA: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 549 SOUTH AFRICA: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 550 SOUTH AFRICA: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 551 SOUTH AFRICA: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 552 SOUTH AFRICA: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 553 SOUTH AFRICA: ICS SECURITY SERVICES MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 554 SOUTH AFRICA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 555 SOUTH AFRICA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 556 SOUTH AFRICA: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 557 SOUTH AFRICA: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 558 SOUTH AFRICA: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 559 SOUTH AFRICA: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 560 SOUTH AFRICA: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 561 SOUTH AFRICA: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 562 SOUTH AFRICA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 563 SOUTH AFRICA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 564 SOUTH AFRICA: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 565 SOUTH AFRICA: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 566 SOUTH AFRICA: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 567 SOUTH AFRICA: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 568 SOUTH AFRICA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 569 SOUTH AFRICA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 570 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 571 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 572 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 573 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 574 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 575 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 576 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 577 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 578 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 579 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 580 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 581 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 582 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 583 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 584 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 585 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 586 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 587 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 588 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 589 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY MANUFACTURING VERTICAL, 2025-2030 (USD MILLION)
- TABLE 590 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 591 REST OF MIDDLE EAST & AFRICA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 592 LATIN AMERICA: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 593 LATIN AMERICA: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 594 LATIN AMERICA: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 595 LATIN AMERICA: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 596 LATIN AMERICA: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 597 LATIN AMERICA: ICS SECURITY SERVICES MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 598 LATIN AMERICA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 599 LATIN AMERICA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 600 LATIN AMERICA: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 601 LATIN AMERICA: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 602 LATIN AMERICA: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 603 LATIN AMERICA: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 604 LATIN AMERICA: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 605 LATIN AMERICA: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 606 LATIN AMERICA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 607 LATIN AMERICA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 608 LATIN AMERICA: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 609 LATIN AMERICA: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 610 LATIN AMERICA: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 611 LATIN AMERICA: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 612 LATIN AMERICA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 613 LATIN AMERICA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 614 LATIN AMERICA: ICS SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 615 LATIN AMERICA: ICS SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 616 MEXICO: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 617 MEXICO: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 618 MEXICO: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 619 MEXICO: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 620 MEXICO: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 621 MEXICO: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 622 MEXICO: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 623 MEXICO: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 624 MEXICO: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 625 MEXICO: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 626 MEXICO: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 627 MEXICO: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 628 MEXICO: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 629 MEXICO: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 630 MEXICO: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 631 MEXICO: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 632 MEXICO: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 633 MEXICO: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 634 MEXICO: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 635 MEXICO: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 636 MEXICO: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 637 MEXICO: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 638 BRAZIL: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 639 BRAZIL: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 640 BRAZIL: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 641 BRAZIL: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 642 BRAZIL: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 643 BRAZIL: ICS SECURITY SERVICES MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 644 BRAZIL: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 645 BRAZIL: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 646 BRAZIL: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 647 BRAZIL: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 648 BRAZIL: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 649 BRAZIL: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 650 BRAZIL: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 651 BRAZIL: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 652 BRAZIL: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 653 BRAZIL: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 654 BRAZIL: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 655 BRAZIL: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 656 BRAZIL: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 657 BRAZIL: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 658 BRAZIL: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 659 BRAZIL: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 660 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 661 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 662 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 663 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 664 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 665 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 666 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 667 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 668 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 669 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 670 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 671 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 672 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY POWER, 2019-2024 (USD MILLION)
- TABLE 673 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY POWER, 2025-2030 (USD MILLION)
- TABLE 674 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2019-2024 (USD MILLION)
- TABLE 675 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY ENERGY & UTILITIES, 2025-2030 (USD MILLION)
- TABLE 676 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY TRANSPORTATION, 2019-2024 (USD MILLION)
- TABLE 677 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY TRANSPORTATION, 2025-2030 (USD MILLION)
- TABLE 678 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY MANUFACTURING, 2019-2024 (USD MILLION)
- TABLE 679 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY MANUFACTURING, 2025-2030 (USD MILLION)
- TABLE 680 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2019-2024 (USD MILLION)
- TABLE 681 REST OF LATIN AMERICA: ICS SECURITY MARKET, BY OTHER VERTICAL, 2025-2030 (USD MILLION)
- TABLE 682 OVERVIEW OF STRATEGIES ADOPTED BY KEY ICS SECURITY VENDORS, 2022-2024
- TABLE 683 ICS SECURITY MARKET: DEGREE OF COMPETITION
- TABLE 684 ICS SECURITY MARKET: REGIONAL FOOTPRINT
- TABLE 685 ICS SECURITY MARKET: OFFERING FOOTPRINT
- TABLE 686 ICS SECURITY MARKET: SECURITY TYPE FOOTPRINT
- TABLE 687 ICS SECURITY MARKET: VERTICAL FOOTPRINT
- TABLE 688 ICS SECURITY MARKET: KEY STARTUPS/SMES
- TABLE 689 COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES, BY OFFERING
- TABLE 690 COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES, BY SECURITY TYPE
- TABLE 691 COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES, BY VERTICAL
- TABLE 692 COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES, BY REGION
- TABLE 693 ICS SECURITY MARKET: PRODUCT LAUNCHES & ENHANCEMENTS, JANUARY 2022-OCTOBER 2024
- TABLE 694 ICS SECURITY MARKET: DEALS, AUGUST 2022-MAY 2025
- TABLE 695 CISCO: COMPANY OVERVIEW
- TABLE 696 CISCO: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 697 CISCO: PRODUCT LAUNCHES
- TABLE 698 CISCO: DEALS
- TABLE 699 FORTINET: COMPANY OVERVIEW
- TABLE 700 FORTINET: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 701 FORTINET: PRODUCT LAUNCHES
- TABLE 702 FORTINET: DEALS
- TABLE 703 PALO ALTO NETWORKS: COMPANY OVERVIEW
- TABLE 704 PALO ALTO NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 705 PALO ALTO NETWORKS: PRODUCT LAUNCHES
- TABLE 706 PALO ALTO NETWORKS: DEALS
- TABLE 707 TENABLE: COMPANY OVERVIEW
- TABLE 708 TENABLE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 709 TENABLE: PRODUCT LAUNCHES
- TABLE 710 TENABLE: DEALS
- TABLE 711 HONEYWELL: COMPANY OVERVIEW
- TABLE 712 HONEYWELL: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 713 HONEYWELL: PRODUCT LAUNCHES
- TABLE 714 HONEYWELL: DEALS
- TABLE 715 CHECK POINT: COMPANY OVERVIEW
- TABLE 716 CHECK POINT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 717 ABB: COMPANY OVERVIEW
- TABLE 718 ABB: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 719 ABB: PRODUCT LAUNCHES
- TABLE 720 CYBERARK: COMPANY OVERVIEW
- TABLE 721 CYBERARK: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 722 CYBERARK: DEALS
- TABLE 723 BELDEN: COMPANY OVERVIEW
- TABLE 724 BELDEN: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 725 KASPERSKY: COMPANY OVERVIEW
- TABLE 726 KASPERSKY: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 727 KASPERSKY: DEALS
- TABLE 728 LOCKHEED MARTIN: COMPANY OVERVIEW
- TABLE 729 LOCKHEED MARTIN: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 730 LOCKHEED MARTIN: DEALS
- TABLE 731 BAE SYSTEMS: COMPANY OVERVIEW
- TABLE 732 BAE SYSTEMS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 733 RTX: COMPANY OVERVIEW
- TABLE 734 RTX: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 735 RTX: DEALS
- TABLE 736 TRELLIX: COMPANY OVERVIEW
- TABLE 737 TRELLIX: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 738 TRELLIX: PRODUCT LAUNCHES
- TABLE 739 ADJACENT MARKETS AND FORECASTS
- TABLE 740 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY OFFERING, 2018-2023 (USD MILLION)
- TABLE 741 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY OFFERING, 2024-2029 (USD MILLION)
- TABLE 742 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SOLUTION, 2018-2023 (USD MILLION)
- TABLE 743 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SOLUTION, 2024-2029 (USD MILLION)
- TABLE 744 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY HARDWARE, 2018-2023 (USD MILLION)
- TABLE 745 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY HARDWARE, 2024-2029 (USD MILLION)
- TABLE 746 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SERVICE, 2018-2023 (USD MILLION)
- TABLE 747 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SERVICE, 2024-2029 (USD MILLION)
- TABLE 748 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SECURITY TYPE, 2018-2023 (USD MILLION)
- TABLE 749 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SECURITY TYPE, 2024-2029 (USD MILLION)
- TABLE 750 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY VERTICAL, 2018-2023 (USD MILLION)
- TABLE 751 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY VERTICAL, 2024-2029 (USD MILLION)
- TABLE 752 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY REGION, 2018-2023 (USD BILLION)
- TABLE 753 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY REGION, 2024-2029 (USD BILLION)
- TABLE 754 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 755 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 756 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 757 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 758 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 759 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 760 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 761 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 762 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 763 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
List of Figures
- FIGURE 1 INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY MARKET: RESEARCH DESIGN
- FIGURE 2 BREAKDOWN OF PRIMARY INTERVIEWS, BY COMPANY TYPE, DESIGNATION, AND REGION
- FIGURE 3 INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY MARKET: DATA TRIANGULATION
- FIGURE 4 INDUSTRIAL CONTROL SYSTEMS (ICS) SECURITY MARKET ESTIMATION: RESEARCH FLOW
- FIGURE 5 APPROACH 1 (SUPPLY SIDE): REVENUE FROM SOLUTION/SERVICES OF ICS SECURITY VENDORS
- FIGURE 6 APPROACH 2 (SUPPLY-SIDE ANALYSIS)
- FIGURE 7 MARKET SIZE ESTIMATION METHODOLOGY (APPROACH 2): BOTTOM-UP (DEMAND SIDE) - SOLUTIONS/SERVICES
- FIGURE 8 GLOBAL INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY MARKET SIZE AND Y-O-Y GROWTH RATE
- FIGURE 9 SEGMENTS WITH SIGNIFICANT MARKET SHARE AND GROWTH RATE
- FIGURE 10 NORTH AMERICA TO ACCOUNT FOR LARGEST SHARE IN 2025
- FIGURE 11 GROWING INSTANCES OF CYBER ATTACKS ON CRITICAL INFRASTRUCTURE AND STRINGENT REGULATIONS TO DRIVE ICS SECURITY MARKET
- FIGURE 12 INDUSTRIAL CONTROL SYSTEM (ICS) SOLUTIONS TO BE LARGER MARKET DURING FORECAST PERIOD
- FIGURE 13 ENCRYPTION SEGMENT TO ACCOUNT FOR FASTEST MARKET GROWTH DURING FORECAST PERIOD
- FIGURE 14 ENDPOINT SECURITY TO ACCOUNT FOR FASTEST MARKET GROWTH DURING FORECAST PERIOD
- FIGURE 15 ENERGY & UTILITIES TO ACCOUNT FOR LARGEST MARKET SIZE DURING FORECAST PERIOD
- FIGURE 16 ASIA PACIFIC TO EMERGE AS FRUITFUL MARKET FOR INVESTMENTS IN NEXT FIVE YEARS
- FIGURE 17 INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY MARKET: DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES
- FIGURE 18 VALUE CHAIN ANALYSIS
- FIGURE 19 INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY MARKET: ECOSYSTEM ANALYSIS
- FIGURE 20 NUMBER OF PATENTS GRANTED FOR INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY MARKET, 2015-2025
- FIGURE 21 INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY MARKET: REGIONAL ANALYSIS OF PATENTS GRANTED
- FIGURE 22 PORTER'S FIVE FORCES ANALYSIS
- FIGURE 23 AVERAGE SELLING PRICE OF SOLUTION, BY KEY PLAYERS, 2024
- FIGURE 24 MARKET POTENTIAL OF GENERATIVE AI IN ENHANCING INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY MARKET ACROSS INDUSTRIES
- FIGURE 25 IMPACT OF GEN AI ON INTERCONNECTED AND ADJACENT ECOSYSTEMS
- FIGURE 26 INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY MARKET: TRENDS AND DISRUPTIONS IMPACTING CUSTOMERS' BUSINESSES
- FIGURE 27 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS
- FIGURE 28 KEY BUYING CRITERIA FOR TOP THREE VERTICALS
- FIGURE 29 INVESTMENTS & FUNDING IN INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY MARKET, 2020-2025
- FIGURE 30 INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY HARDWARE IMPORT, BY KEY COUNTRY, 2024-2024 (USD MILLION)
- FIGURE 31 INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY HARDWARE EXPORT, BY KEY COUNTRY, 2020-2024 (USD MILLION)
- FIGURE 32 SERVICES SEGMENT TO GROW AT HIGHER CAGR DURING FORECAST PERIOD
- FIGURE 33 IAM SEGMENT TO GROW AT HIGHEST RATE DURING FORECAST PERIOD
- FIGURE 34 PROFESSIONAL SERVICES SEGMENT TO ACCOUNT FOR LARGEST MARKET BY 2030
- FIGURE 35 NETWORK SECURITY SEGMENT TO ACCOUNT FOR LARGEST MARKET DURING FORECAST PERIOD
- FIGURE 36 ENERGY & UTILITIES SEGMENT TO ACCOUNT FOR LARGEST MARKET DURING FORECAST PERIOD
- FIGURE 37 NORTH AMERICA TO BE LARGEST MARKET DURING FORECAST PERIOD
- FIGURE 38 NORTH AMERICA: MARKET SNAPSHOT
- FIGURE 39 ASIA PACIFIC: MARKET SNAPSHOT
- FIGURE 40 SEGMENTAL REVENUE ANALYSIS OF TOP FIVE MARKET PLAYERS, 2020-2024 (USD MILLION)
- FIGURE 41 SHARE OF LEADING COMPANIES IN ICS SECURITY MARKET, 2024
- FIGURE 42 ICS SECURITY MARKET: COMPARISON OF VENDOR BRANDS
- FIGURE 43 COMPANY VALUATION OF KEY VENDORS, 2024 (USD BILLION)
- FIGURE 44 EV/EBIDTA, 2025
- FIGURE 45 ICS SECURITY MARKET: COMPANY EVALUATION MATRIX (KEY PLAYERS), 2024
- FIGURE 46 ICS SECURITY MARKET: COMPANY FOOTPRINT
- FIGURE 47 ICS SECURITY MARKET: COMPANY EVALUATION MATRIX (STARTUPS/SMES), 2024
- FIGURE 48 CISCO: COMPANY SNAPSHOT
- FIGURE 49 FORTINET: COMPANY SNAPSHOT
- FIGURE 50 PALO ALTO NETWORKS: COMPANY SNAPSHOT
- FIGURE 51 TENABLE: COMPANY SNAPSHOT
- FIGURE 52 HONEYWELL: COMPANY SNAPSHOT
- FIGURE 53 CHECK POINT: COMPANY SNAPSHOT
- FIGURE 54 ABB: COMPANY SNAPSHOT
- FIGURE 55 CYBERARK: COMPANY SNAPSHOT
- FIGURE 56 BELDEN: COMPANY SNAPSHOT
- FIGURE 57 KASPERSKY: COMPANY SNAPSHOT
- FIGURE 58 LOCKHEED MARTIN: COMPANY SNAPSHOT
- FIGURE 59 BAE SYSTEMS: COMPANY SNAPSHOT
- FIGURE 60 RTX: COMPANY SNAPSHOT
The industrial control system (ICS) security market size is projected to grow from USD 15.35 billion in 2025 to USD 32.89 billion by 2030 at a compound annual growth rate (CAGR) of 16.5% during the forecast period. Industrial organizations are turning to Zero Trust Architecture to better secure their ICS environments by not automatically trusting any user or device, even inside the network. It uses strict access rules, identity checks, and network segmentation to stop threats from spreading. This approach is becoming essential as more remote access and third-party tools get connected to industrial systems.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | (USD Million/USD Billion) |
| Segments | Offering, solutions, service, security type, vertical, and region |
| Regions covered | North America, Europe, Asia Pacific, Middle East & Africa, and Latin America |
"By solution, the firewall segment is estimated to account for the largest market share during the forecast period."
ICS security firewall solutions are purpose-built to safeguard industrial control systems by monitoring and controlling network traffic between IT and OT environments, enforcing segmentation, and blocking unauthorized access without disrupting real-time operations. These firewalls support industrial protocols like Modbus and DNP3, offer deep packet inspection, and help detect and contain anomalies within control networks. Their adoption is growing due to rising cyber threats targeting critical infrastructure, increased regulatory pressure (e.g., NERC CIP, IEC 62443), and the growing convergence of operational and digital technologies. As industries embrace IIoT, remote access, and cloud-based systems, the need for resilient, protocol-aware firewalls is becoming a core component of ICS security strategies.
"By region, the Asia Pacific market is projected to record the highest growth rate during the forecast period."
The ICS security landscape in Asia Pacific is intensifying as nations respond to rising cyber threats, digital transformation, and critical infrastructure risks. In Japan, there is strong momentum toward securing OT-IT environments, especially in energy and manufacturing, supported by growing industry participation as seen in JPCERT/CC's 2025 ICS Security Conference, with over 560 attendees. India faces a surge in threats, with a 261% increase in cyberattacks in Q1 2024, and 83% of organizations reported incidents the previous year. This has created a sense of urgency nationwide, leading CERT-In to require cyber incident reports within six hours, which speeds up security measures across sectors like power and transportation. Meanwhile, China is strengthening its ICS defenses under the "Made in China 2025" policy, enacting strict cybersecurity laws, supervised by CNITSEC, and increasing the use of AI and industrial IoT for threat detection. The region as a whole is seeing expanded collaboration between public and private players, wider deployment of Zero Trust architectures, and growing investment in AI-powered tools to protect increasingly connected industrial systems.
Breakdown of Primaries
The study contains insights from various industry experts, from component suppliers to Tier 1 companies and OEMs. The break-up of the primaries is as follows:
- By Company Type: Tier 1 - 55%, Tier 2 - 20%, and Tier 3 - 25%
- By Designation: C-level - 60%, Directors - 15%, and Managers - 25%
- By Region: North America - 35%, Europe - 25%, Asia Pacific - 20%, RoW - 20%
The key players in the industrial control system (ICS) security market include Cisco (US), ABB (Switzerland), Lockheed Martin (US), Fortinet (US), Honeywell (US), Palo Alto Networks (US), BAE Systems (UK), RTX (US), Trellix (US), Check Point (Israel), Darktrace (UK), Kaspersky Lab (Russia), Tenable (US), Belden (US), Sophos (UK), CyberArk (US), Claroty (US), Dragos (US), Nozomi Networks (US), Cyberbit (US), Forescout (US), Radiflow (Israel), Verve Industrial Protection (US), Xage Security (US), Positive Technology (US), and others.
The study includes an in-depth competitive analysis of the key players in the industrial control system (ICS) security market, their company profiles, recent developments, and key market strategies.
Research Coverage
The report segments the ICS security market and forecasts its size by Offering (Solution, Services), Solution (Antimalware/ Antivirus, DDOS Mitigation, Encryption, Firewall, Identity & Access Management, Intrusion Detection & Prevention System, Security & Vulnerability Management, Security Configuration Management, Security Information & Event Management (SIEM), Whitelisting, Other Solutions (Honeypots/Deception Technology Platforms and Web Filtering)), Service (Professional Services (Consulting & Integration Services, Support & Maintenance Services, Training & Development Services, Incident Response Services), Managed Services), Security Type (Network Security, Endpoint Security, Application Security, Database Security), Vertical (Power, Energy and Utilities, Transportation, Manufacturing, Others Verticals), and Region (North America, Europe, Asia Pacific, Middle East & Africa, and Latin America).
The study also includes an in-depth competitive analysis of the market's key players, their company profiles, key observations related to product and business offerings, recent developments, and key market strategies.
Key Benefits of Buying the Report
The report will help the market leaders/new entrants with information on the closest approximations of the revenue numbers for the overall industrial control system (ICS) security market and the subsegments. This report will help stakeholders understand the competitive landscape and gain more insights to position their businesses better and plan suitable go-to-market strategies. The report also helps stakeholders understand the market pulse and provides information on key market drivers, restraints, challenges, and opportunities.
The report provides insights on the following pointers:
- Analysis of key drivers (Confluence of digital technologies and industrial systems integration, Government initiatives and regulations in critical infrastructure protection drive adoption of ICS security solutions, Integration of IT and OT systems driving expansion in ICS security solutions), restraints (Elevated acquisition expenses for ICS security solutions, Legacy infrastructure vulnerabilities), opportunities (Escalating demand for professional and managed security services in small and medium-sized enterprises (SMEs), Government and Enterprises R& D investments for robust advancements in ICS security solutions) and challenges (Shortage of skilled analysts for analyzing critical ICT systems, Limited awareness about ICS security techniques)
- Product Development/Innovation: Detailed insights on upcoming technologies, research & development activities, and new product & service launches in the industrial control system (ICS) security market.
- Market Development: Comprehensive information about lucrative markets - the report analyses the industrial control system (ICS) security market across varied regions.
- Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the industrial control system (ICS) security market.
- Competitive Assessment: In-depth assessment of market shares, growth strategies, and service offerings of leading players, such as Cisco (US), ABB (Switzerland), Lockheed Martin (US), Fortinet (US), Honeywell (US), Palo Alto Networks (US), BAE Systems (UK), RTX (US), Trellix (US), Check Point (Israel), Darktrace (UK), Kaspersky Lab (Russia), Tenable (US), Belden (US), Sophos (UK), CyberArk (US), Claroty (US), Dragos (US), Nozomi Networks (US), Cyberbit (US), Forescout (US), Radiflow (Israel), Verve Industrial Protection (US), Xage Security (US), and Positive Technology (US), among others, in the industrial control system (ICS) security market strategies.
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.2.1 INCLUSIONS AND EXCLUSIONS
- 1.3 STUDY SCOPE
- 1.3.1 MARKET SEGMENTATION
- 1.3.2 YEARS CONSIDERED
- 1.4 CURRENCY CONSIDERED
- 1.5 STAKEHOLDERS
2 RESEARCH METHODOLOGY
- 2.1 RESEARCH DATA
- 2.1.1 SECONDARY DATA
- 2.1.2 PRIMARY DATA
- 2.1.2.1 Breakup of primaries
- 2.1.2.2 Key industry insights
- 2.2 MARKET BREAKUP AND DATA TRIANGULATION
- 2.3 MARKET SIZE ESTIMATION
- 2.3.1 TOP-DOWN APPROACH
- 2.3.2 BOTTOM-UP APPROACH
- 2.4 MARKET FORECAST
- 2.5 RESEARCH ASSUMPTIONS
- 2.6 LIMITATIONS AND RISK ASSESSMENT
3 EXECUTIVE SUMMARY
4 PREMIUM INSIGHTS
- 4.1 ATTRACTIVE OPPORTUNITIES FOR KEY MARKET PLAYERS
- 4.2 INDUSTRIAL CONTROL SYSTEM (ICS) MARKET, BY OFFERING, 2025
- 4.3 INDUSTRIAL CONTROL SYSTEM (ICS) MARKET, BY SOLUTION, 2025
- 4.4 INDUSTRIAL CONTROL SYSTEM (ICS) MARKET, BY SECURITY TYPE, 2025
- 4.5 INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY MARKET, BY VERTICAL, 2025-2030
- 4.6 MARKET INVESTMENT SCENARIO
5 MARKET OVERVIEW AND INDUSTRY TRENDS
- 5.1 INTRODUCTION
- 5.2 MARKET DYNAMICS
- 5.2.1 DRIVERS
- 5.2.1.1 Confluence of digital technologies and industrial system integration
- 5.2.1.2 Government initiatives and regulations in critical infrastructure protection
- 5.2.1.3 Integration of IT and OT systems
- 5.2.2 RESTRAINTS
- 5.2.2.1 Elevated acquisition expenses for ICS security solutions
- 5.2.2.2 Legacy system vulnerabilities
- 5.2.3 OPPORTUNITIES
- 5.2.3.1 Escalating demand for professional and managed security services in small and medium-sized enterprises
- 5.2.3.2 Government R&D investment initiatives for robust advancements in ICS security solutions
- 5.2.4 CHALLENGES
- 5.2.4.1 Shortage of analysts
- 5.2.4.2 Limited awareness about ICS security techniques
- 5.2.1 DRIVERS
- 5.3 USE CASES
- 5.3.1 USE CASE 1: PALO ALTO NETWORKS HELPED WARREN ROGERS ASSOCIATES WITH ICS SECURITY
- 5.3.2 USE CASE 2: CAPULA HELPED MAJOR POWER PROVIDER IMPROVE EXISTING ROBUST CYBERSECURITY PROGRAM
- 5.3.3 USE CASE 3: MULTINATIONAL GAS AND ELECTRICAL DISTRIBUTION COMPANY DEPLOYED INDUSTRIAL DEFENDER CENTRAL MANAGER TO MONITOR ITS CRITICAL ASSETS
- 5.3.4 USE CASE 4: NOZOMI NETWORKS HELPED VERMONT ELECTRIC COOPERATIVE ENHANCE CYBERSECURITY AND OPERATIONAL EFFICIENCY
- 5.4 VALUE CHAIN ANALYSIS
- 5.5 ECOSYSTEM ANALYSIS
- 5.6 PATENT ANALYSIS
- 5.6.1 LIST OF TOP PATENTS IN INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY MARKET, 2023-2025
- 5.7 PORTER'S FIVE FORCES ANALYSIS
- 5.7.1 THREAT OF NEW ENTRANTS
- 5.7.2 THREAT OF SUBSTITUTES
- 5.7.3 BARGAINING POWER OF SUPPLIERS
- 5.7.4 BARGAINING POWER OF BUYERS
- 5.7.5 INTENSITY OF COMPETITIVE RIVALRY
- 5.8 PRICING ANALYSIS
- 5.8.1 AVERAGE SELLING PRICE OF SOLUTION, BY KEY PLAYERS, 2024
- 5.8.2 INDICATIVE PRICING OF PRODUCT, BY KEY PLAYERS, 2024
- 5.9 TECHNOLOGY ANALYSIS
- 5.9.1 KEY TECHNOLOGIES
- 5.9.1.1 AI/ML
- 5.9.1.2 Anomaly Detection & Behavior Analytics
- 5.9.1.3 IoT
- 5.9.2 COMPLEMENTARY TECHNOLOGIES
- 5.9.2.1 Blockchain
- 5.9.2.2 Patch Management
- 5.9.3 ADJACENT TECHNOLOGIES
- 5.9.3.1 Cloud-based Security
- 5.9.3.2 Zero Trust Architecture (ZTA)
- 5.9.1 KEY TECHNOLOGIES
- 5.10 IMPACT OF GENERATIVE AI ON INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY MARKET
- 5.10.1 TOP USE CASES & MARKET POTENTIAL
- 5.10.2 IMPACT OF GEN AI ON INTERCONNECTED AND ADJACENT ECOSYSTEMS
- 5.10.2.1 Identity and Access Management (IAM)
- 5.10.2.2 SIEM (Security Information and Event Management) Market
- 5.10.2.3 Network Monitoring and Detection Market
- 5.10.2.4 Security Orchestration, Automation, and Response (SOAR) Market
- 5.11 TRENDS AND DISRUPTIONS IMPACTING CUSTOMERS' BUSINESSES
- 5.12 KEY STAKEHOLDERS AND BUYING CRITERIA
- 5.12.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 5.12.2 BUYING CRITERIA
- 5.13 TARIFF AND REGULATORY LANDSCAPE
- 5.13.1 TARIFF RELATED TO INDUSTRIAL CONTROL SYSTEM (ICS) SECURITY SOLUTIONS
- 5.13.2 REGULATORY LANDSCAPE
- 5.13.2.1 Regulatory bodies, government agencies, and other organizations
- 5.13.3 REGULATIONS
- 5.13.3.1 General Data Protection Regulation (GDPR)
- 5.13.3.2 Sarbanes-Oxley (SOX) Act
- 5.13.3.3 SOC 2
- 5.13.3.4 ISO 27001
- 5.14 KEY CONFERENCES & EVENTS IN 2025
- 5.15 INVESTMENT AND FUNDING SCENARIO
- 5.16 TRADE ANALYSIS
- 5.17 IMPACT OF 2025 US TARIFF - OVERVIEW
- 5.17.1 INTRODUCTION
- 5.17.2 KEY TARIFF RATES
- 5.17.3 PRICE IMPACT ANALYSIS
- 5.17.4 IMPACT ON COUNTRY/REGION
- 5.17.4.1 North america
- 5.17.4.2 Europe
- 5.17.4.3 Asia Pacific
- 5.17.5 MARKET CHALLENGES:
- 5.17.6 MITIGATION MEASURES:
- 5.17.7 INDUSTRIES
6 ICS SECURITY MARKET, BY OFFERING
- 6.1 INTRODUCTION
- 6.1.1 OFFERING: ICS SECURITY MARKET DRIVERS
- 6.2 SOLUTIONS
- 6.2.1 FOCUS ON PROTECTING INDUSTRIAL CONTROL SYSTEMS FROM ATTACKS TO DRIVE MARKET
- 6.3 SERVICES
- 6.3.1 NEED FOR INTEGRATING AND MANAGING SOLUTIONS ACROSS BUSINESS OPERATIONS TO SPUR GROWTH
7 ICS SECURITY MARKET, BY SOLUTION
- 7.1 INTRODUCTION
- 7.1.1 SOLUTIONS: ICS SECURITY MARKET DRIVERS
- 7.2 ANTIMALWARE/ANTIVIRUS
- 7.2.1 ANTIMALWARE AND ANTIVIRUS SOFTWARE SOLUTIONS SAFEGUARD INDUSTRIAL CONTROL SYSTEMS AGAINST EXTERNAL THREATS
- 7.3 DDOS MITIGATION
- 7.3.1 RISE IN IOT-FOCUSED DDOS THREATS, INCREASING SOPHISTICATION OF ATTACKS, AND HIGHLY REGULATED INDUSTRY VERTICALS TO BOOST GROWTH
- 7.4 ENCRYPTION
- 7.4.1 ENCRYPTION SOFTWARE PROVIDES COMPREHENSIVE WAY TO MITIGATE RISKS OF ACCIDENTAL AND INTENTIONAL DATA BREACHES
- 7.5 FIREWALL
- 7.5.1 RISING NEED TO MAINTAIN ICS NETWORK INTEGRITY TO DRIVE USE OF FIREWALLS
- 7.6 IDENTITY & ACCESS MANAGEMENT
- 7.6.1 IDENTITY & ACCESS MANAGEMENT SOLUTIONS PROVIDE ROBUST FRAMEWORK FOR ENFORCING SECURITY POLICIES AND MULTI-FACTOR AUTHENTICATION MECHANISMS
- 7.7 INTRUSION DETECTION & PREVENTION SYSTEM
- 7.7.1 INTRUSION DETECTION & PREVENTION SYSTEM SECURES ORGANIZATIONS' BUSINESS-CRITICAL INFRASTRUCTURE FROM ADVANCED CYBERATTACKS
- 7.8 SECURITY & VULNERABILITY MANAGEMENT
- 7.8.1 INCREASING COMPLEXITY AND INTERCONNECTIVITY OF INDUSTRIAL ENVIRONMENTS TO BOOST ADOPTION OF SECURITY & VULNERABILITY MANAGEMENT SOLUTIONS
- 7.9 SECURITY CONFIGURATION MANAGEMENT
- 7.9.1 SECURITY CONFIGURATION MANAGEMENT TO PLAY VITAL ROLE IN INTEGRATING IT AND OT SECURITY AND CONFIGURATION
- 7.10 SECURITY INFORMATION & EVENT MANAGEMENT
- 7.10.1 DEMAND FOR SYSTEM THAT CONSOLIDATES, ANALYZES, AND COMPLIES WITH EVENT DATA TO DRIVE MARKET
- 7.11 WHITELISTING
- 7.11.1 WHITELISTING TO MITIGATE TECHNOLOGY INTEROPERABILITY ISSUES AND DEPLOY MOST RELIABLE SOLUTIONS IN ICS SECURITY
- 7.12 OTHER SOLUTIONS
8 ICS SECURITY MARKET, BY SERVICE
- 8.1 INTRODUCTION
- 8.1.1 SERVICES: ICS SECURITY MARKET DRIVERS
- 8.2 PROFESSIONAL SERVICES
- 8.2.1 SHORTAGE OF SECURITY SKILLS AMONG INTERNAL SECURITY PROFESSIONALS TO DRIVE DEMAND FOR PROFESSIONAL SERVICES
- 8.2.2 CONSULTING & INTEGRATION
- 8.2.3 SUPPORT & MAINTENANCE SERVICES
- 8.2.4 TRAINING & DEVELOPMENT SERVICES
- 8.2.5 INCIDENT RESPONSE SERVICES
- 8.3 MANAGED SECURITY SERVICES
- 8.3.1 MANAGED SECURITY SERVICES ALLOW ORGANIZATIONS TO SPEND MORE TIME TO FOCUS ON BUSINESSES
9 ICS SECURITY MARKET, BY SECURITY TYPE
- 9.1 INTRODUCTION
- 9.1.1 SECURITY TYPE: ICS SECURITY MARKET DRIVERS
- 9.2 NETWORK SECURITY
- 9.2.1 NETWORK SECURITY SAFEGUARDS NETWORKS FROM ADVANCED THREATS
- 9.3 ENDPOINT SECURITY
- 9.3.1 ENDPOINT SECURITY TO SERVE AS DOORWAY FOR CYBERCRIMINALS TO GAIN ACCESS TO ICS NETWORKS
- 9.4 APPLICATION SECURITY
- 9.4.1 FOCUS ON IDENTIFYING AND ADDRESSING SECURITY GAPS IN WEB AND MOBILE APPLICATIONS TO BOOST GROWTH
- 9.5 DATABASE SECURITY
- 9.5.1 STRINGENT GOVERNMENT REGULATIONS FOR DATABASE PROTECTION TO BOOST MARKET
10 ICS SECURITY MARKET, BY VERTICAL
- 10.1 INTRODUCTION
- 10.1.1 VERTICAL: ICS SECURITY MARKET DRIVERS
- 10.2 POWER
- 10.2.1 CHALLENGES CONCERNING AGING GRID INFRASTRUCTURES TO DRIVE ADOPTION OF ICS SECURITY SYSTEMS IN POWER SECTOR
- 10.2.2 NUCLEAR POWER PLANTS
- 10.2.3 THERMAL AND HYDROPOWER PLANTS
- 10.2.4 RENEWABLE ENERGY POWER PLANTS
- 10.2.5 POWER GRID
- 10.3 ENERGY & UTILITIES
- 10.3.1 INCREASED GOVERNMENT FOCUS ON CYBERSECURITY AMONG ENERGY AND UTILITY ORGANIZATIONS TO DRIVE MARKET
- 10.3.2 OIL & GAS
- 10.3.3 ELECTRIC POWER TRANSMISSION
- 10.3.4 WATER TREATMENT & DISTRIBUTION
- 10.3.5 WASTEWATER COLLECTION & TREATMENT
- 10.4 TRANSPORTATION
- 10.4.1 RISING COMPLEXITY IN HANDLING TRANSPORTATION SYSTEMS TO BOOST MARKET FOR ICS SECURITY SYSTEMS
- 10.4.2 AIRPORTS
- 10.4.3 SEAPORTS
- 10.4.4 RAILWAYS
- 10.4.5 OTHER TRANSPORTATION APPLICATIONS
- 10.5 MANUFACTURING
- 10.5.1 RISING ATTACKS ON MANUFACTURING SECTOR TO SPUR DEMAND FOR ICS SECURITY SYSTEMS
- 10.5.2 CHEMICAL & MATERIALS
- 10.5.3 AUTOMOTIVE
- 10.5.4 MINING UNITS
- 10.5.5 PAPER & PULP
- 10.5.6 OTHER MANUFACTURING APPLICATIONS
- 10.6 OTHER VERTICALS
- 10.6.1 COMMERCIAL BUILDINGS
- 10.6.2 COMMUNICATION SYSTEMS
- 10.6.3 HEALTHCARE
- 10.6.4 OTHER APPLICATIONS
11 ICS SECURITY MARKET, BY REGION
- 11.1 INTRODUCTION
- 11.2 NORTH AMERICA
- 11.2.1 NORTH AMERICA: MACROECONOMIC OUTLOOK
- 11.2.2 NORTH AMERICA: ICS SECURITY MARKET DRIVERS
- 11.2.3 US
- 11.2.3.1 Securing ICS: Legislation and shielding infrastructure resilience
- 11.2.4 CANADA
- 11.2.4.1 Government initiatives implemented against cybercrimes
- 11.3 EUROPE
- 11.3.1 EUROPE: MACROECONOMIC OUTLOOK
- 11.3.2 EUROPE: ICS SECURITY MARKET DRIVERS
- 11.3.3 UK
- 11.3.3.1 Strategic initiatives and investments by UK government
- 11.3.4 GERMANY
- 11.3.4.1 Revision of IT Security Act
- 11.3.5 ITALY
- 11.3.5.1 Collaborations among prominent players to strengthen security in Italy's critical infrastructures
- 11.3.6 REST OF EUROPE
- 11.4 ASIA PACIFIC
- 11.4.1 ASIA PACIFIC: MACROECONOMIC OUTLOOK
- 11.4.2 ASIA PACIFIC: ICS SECURITY MARKET DRIVERS
- 11.4.3 CHINA
- 11.4.3.1 State-backed platforms introduced for reporting vulnerabilities for data protection
- 11.4.4 JAPAN
- 11.4.4.1 Increasing awareness through training programs and collaborations
- 11.4.5 INDIA
- 11.4.5.1 India's fortified cyber defenses with ICSSTB
- 11.4.6 REST OF ASIA PACIFIC
- 11.5 MIDDLE EAST & AFRICA
- 11.5.1 MIDDLE EAST & AFRICA: MACROECONOMIC OUTLOOK
- 11.5.2 MIDDLE EAST & AFRICA: ICS SECURITY MARKET DRIVERS
- 11.5.3 GCC COUNTRIES
- 11.5.3.1 Increasing cyber threats and government initiatives footprint driving market
- 11.5.3.2 KSA
- 11.5.3.3 UAE
- 11.5.3.4 Rest of GCC countries
- 11.5.4 SOUTH AFRICA
- 11.5.4.1 Growth in interlinked industrial infrastructure and cybersecurity in Africa
- 11.5.5 REST OF MIDDLE EAST & AFRICA
- 11.6 LATIN AMERICA
- 11.6.1 LATIN AMERICA: MACROECONOMIC OUTLOOK
- 11.6.2 LATIN AMERICA: ICS SECURITY MARKET DRIVERS
- 11.6.3 MEXICO
- 11.6.3.1 Escalating cyber threats in Mexico prompt need for immediate security measures
- 11.6.4 BRAZIL
- 11.6.4.1 Establishment of cyberattack response network
- 11.6.5 REST OF LATIN AMERICA
12 COMPETITIVE LANDSCAPE
- 12.1 KEY PLAYER STRATEGIES/RIGHT TO WIN, 2022-2024
- 12.2 REVENUE ANALYSIS, 2020-2024
- 12.3 MARKET SHARE ANALYSIS, 2024
- 12.4 BRAND COMPARISON
- 12.4.1 CISCO
- 12.4.2 FORTINET
- 12.4.3 PALO ALTO NETWORKS
- 12.4.4 TENABLE
- 12.4.5 HONEYWELL
- 12.5 COMPANY VALUATION AND FINANCIAL METRICS
- 12.5.1 COMPANY VALUATION, 2024
- 12.5.2 FINANCIAL METRICS USING EV/EBIDTA
- 12.6 COMPANY EVALUATION MATRIX: KEY PLAYERS
- 12.6.1 STARS
- 12.6.2 EMERGING LEADERS
- 12.6.3 PERVASIVE PLAYERS
- 12.6.4 PARTICIPANTS
- 12.6.5 COMPANY FOOTPRINT: KEY PLAYERS, 2024
- 12.6.5.1 Company footprint
- 12.6.5.2 Region footprint
- 12.6.5.3 Offering footprint
- 12.6.5.4 Vertical footprint
- 12.7 COMPANY EVALUATION MATRIX: STARTUPS/SMES
- 12.7.1 PROGRESSIVE COMPANIES
- 12.7.2 RESPONSIVE COMPANIES
- 12.7.3 DYNAMIC COMPANIES
- 12.7.4 STARTING BLOCKS
- 12.7.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
- 12.7.5.1 Detailed list of key startups/SMEs
- 12.7.5.2 Offering Footprint
- 12.7.5.3 Vertical Footprint
- 12.7.5.4 Vertical Footprint
- 12.7.5.5 Region Footprint
- 12.8 COMPETITIVE SCENARIO
- 12.8.1 PRODUCT LAUNCHES & ENHANCEMENTS
- 12.8.2 DEALS
13 COMPANY PROFILES
- 13.1 KEY PLAYERS
- 13.1.1 CISCO
- 13.1.1.1 Business overview
- 13.1.1.2 Products/Solutions/Services offered
- 13.1.1.3 Recent developments
- 13.1.1.4 MnM view
- 13.1.1.4.1 Right to win
- 13.1.1.4.2 Strategic choices
- 13.1.1.4.3 Weaknesses and competitive threats
- 13.1.2 FORTINET
- 13.1.2.1 Business overview
- 13.1.2.2 Products/Solutions/Services offered
- 13.1.2.3 Recent developments
- 13.1.2.4 MnM view
- 13.1.2.4.1 Right to win
- 13.1.2.4.2 Strategic choices
- 13.1.2.4.3 Weaknesses and competitive threats
- 13.1.3 PALO ALTO NETWORKS
- 13.1.3.1 Business overview
- 13.1.3.2 Products/Solutions/Services offered
- 13.1.3.3 Recent developments
- 13.1.3.4 MnM view
- 13.1.3.4.1 Right to win
- 13.1.3.4.2 Strategic choices
- 13.1.3.4.3 Weaknesses and competitive threats
- 13.1.4 TENABLE
- 13.1.4.1 Business overview
- 13.1.4.2 Products/Solutions/Services offered
- 13.1.4.3 Recent developments
- 13.1.4.4 MnM view
- 13.1.4.4.1 Right to win
- 13.1.4.4.2 Strategic choices
- 13.1.4.4.3 Weaknesses and competitive threats
- 13.1.5 HONEYWELL
- 13.1.5.1 Business overview
- 13.1.5.2 Products/Solutions/Services offered
- 13.1.5.3 Recent developments
- 13.1.5.4 MnM view
- 13.1.5.4.1 Right to win
- 13.1.5.4.2 Strategic choices
- 13.1.5.4.3 Weaknesses and competitive threats
- 13.1.6 CHECK POINT
- 13.1.6.1 Business overview
- 13.1.6.2 Products/Solutions/Services offered
- 13.1.7 ABB
- 13.1.7.1 Business overview
- 13.1.7.2 Products/Solutions/Services offered
- 13.1.7.3 Recent developments
- 13.1.8 CYBERARK
- 13.1.8.1 Business overview
- 13.1.8.2 Products/Solutions/Services offered
- 13.1.8.3 Recent developments
- 13.1.9 BELDEN
- 13.1.9.1 Business overview
- 13.1.9.2 Products/Solutions/Services offered
- 13.1.10 KASPERSKY
- 13.1.10.1 Business overview
- 13.1.10.2 Products/Solutions/Services offered
- 13.1.10.3 Recent developments
- 13.1.11 LOCKHEED MARTIN
- 13.1.11.1 Business overview
- 13.1.11.2 Products/Solutions/Services offered
- 13.1.11.3 Recent developments
- 13.1.12 BAE SYSTEMS
- 13.1.12.1 Business overview
- 13.1.12.2 Products/Solutions/Services offered
- 13.1.13 RTX
- 13.1.13.1 Business overview
- 13.1.13.2 Products/Solutions/Services offered
- 13.1.13.3 Recent developments
- 13.1.14 TRELLIX
- 13.1.14.1 Business overview
- 13.1.14.2 Products/Solutions/Services offered
- 13.1.14.3 Recent developments
- 13.1.15 DARKTRACE
- 13.1.16 SOPHOS
- 13.1.17 NOZOMI NETWORKS
- 13.1.18 CYBERBIT
- 13.1.19 FORESCOUT
- 13.1.1 CISCO
- 13.2 OTHER KEY PLAYERS
- 13.2.1 CLAROTY
- 13.2.2 DRAGOS
- 13.2.3 RADIFLOW
- 13.2.4 VERVE INDUSTRIAL PROTECTION
- 13.2.5 XAGE SECURITY
- 13.2.6 POSITIVE TECHNOLOGY
14 ADJACENT MARKETS
- 14.1 INTRODUCTION TO ADJACENT MARKETS
- 14.2 LIMITATIONS
- 14.3 ADJACENT MARKETS
- 14.4 CRITICAL INFRASTRUCTURE PROTECTION MARKET
- 14.4.1 OPERATIONAL TECHNOLOGY (OT) MARKET
15 APPENDIX
- 15.1 DISCUSSION GUIDE
- 15.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 15.3 CUSTOMIZATION OPTIONS
- 15.4 RELATED REPORTS
- 15.5 AUTHOR DETAILS