
|
市場調査レポート
商品コード
1687854
セキュリティオーケストレーション- 市場シェア分析、産業動向・統計、成長予測(2025年~2030年)Security Orchestration - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
カスタマイズ可能
適宜更新あり
|
|||||||
| セキュリティオーケストレーション- 市場シェア分析、産業動向・統計、成長予測(2025年~2030年) |
|
出版日: 2025年03月18日
発行: Mordor Intelligence
ページ情報: 英文 100 Pages
納期: 2~3営業日
|
全表示
- 概要
- 目次
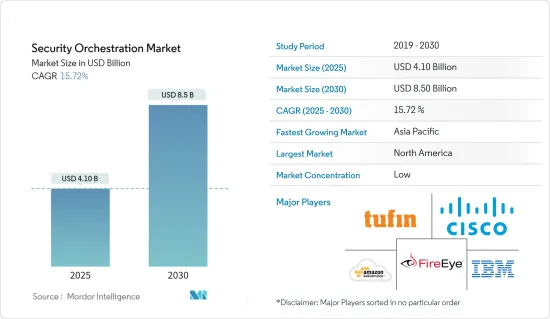
セキュリティオーケストレーション市場規模は、2025年に41億米ドルと推定され、予測期間(2025~2030年)のCAGRは15.72%で、2030年には85億米ドルに達すると予測されます。
さまざまな組織にセキュリティオーケストレーションを導入することで、セキュリティアラートを管理し、深刻なサイバー攻撃を防ぐことができます。サイバー攻撃の高度化に伴い、セキュリティベンダーは、重要なビジネスアプリケーションを処理するためのプロアクティブで総合的なセキュリティアーキテクチャを提供するため、より優れたオーケストレーションプラットフォームを開発しようとしています。
主要ハイライト
- 中小企業に影響を及ぼしているBYOD動向の劇的な増加や、クラウドベースのソリューションの急速な展開と開発により、セキュリティ侵害やセキュリティ事象が増加しており、さまざまな組織でセキュリティオーケストレーションの適用に拍車がかかっています。
- コンピュータネットワークトラフィックをモニタリング・管理するためにセキュリティオーケストレーションプラットフォームを採用する企業が増えているため、ネットワークフォレンジックの応用が増加し、市場の需要を促進すると予想されます。
- コネクテッドデバイスの普及に伴い、さまざまなITサービスやソリューションの採用が増加しているため、日々生成されるデータ量がさらに増加し、その結果、効果的な管理と封じ込めが必要な潜在的脆弱性の範囲が膨大になっています。
- これらのソリューションの導入により、ITIL、PCI、HIPAA(Health Insurance Portability and Accountability Act:医療保険の相互運用性と説明責任に関する法律)、SOX法(Sarbanes-Oxley Act:サーベンス・オクスリー法)、グラム・リーチ・ブライリー法(Gramm-Leach-Bliley Act:グラム・リーチ・ブライリー法)といった監査コンプライアンス要件への準拠も容易になり、積極的な施策の実施や監査コンプライアンス・レポートの作成が可能になりました。こうした要因が市場の成長を後押ししています。
セキュリティオーケストレーション市場の動向
IT・通信セグメントが大幅な成長を記録する見込み
- IT・通信産業は、何百万もの顧客をつなぐ世界と国内の幅広いサービスを提供しています。この多様なエコシステムは、あらゆる業務を遂行する上でインフラ、ネットワーク、データベースに大きく依存しているため、サイバー攻撃を頻繁に受けやすいです。
- 電気通信事業者は通常、氏名、住所、財務データなどの顧客の個人情報を保存しています。情報に敏感なデータは、内部関係者やサイバー犯罪者にとって、金銭を盗んだり、顧客を恐喝したり、さらなる攻撃を仕掛けたりするための格好の標的となります。そのため、この産業では、最新のソリューション、適切なツール、先進的訓練を受けた人材、脅威に即座に対応する能力により重点を置くことが求められています。
- SOARツールは、ITチームが組織のインシデント対応活動を定義、標準化、自動化するのを支援します。ほとんどのIT組織は、これらのツールを使用して、セキュリティ運用とプロセスの自動化、インシデントへの対応、脆弱性と脅威の管理を行っています。さらに、セキュリティオーケストレーションは、エンタープライズセキュリティに携わるIT専門家の脅威対応と解決に要する時間を短縮します。
- クラウドやIoTによるデータ接続の増大がITセグメントの中心的な課題となっており、セキュリティは、データ侵害から身を守るために、産業のすべての組織にとって最優先事項となっています。さらに、COVID-19の大流行により、情報通信技術企業はビジネスプロセスを再考し、通信ネットワークの需要が倍増している場合には特に、大流行を通じて顧客に信頼性の高いサービスを提供するためにネットワーク性能を向上させる必要に迫られています。そのため、企業はこうしたセキュリティオーケストレーションソリューションを採用し、市場成長率を押し上げています。
北米が最大の市場シェアを占める
- 北米は、IBM Corporation、DXC Technology Company、Cisco System Inc.、FireEye Inc.など、この地域の多くの著名なセキュリティオーケストレーション・ベンダーのおかげで、セキュリティオーケストレーション市場を独占しています。エンドユーザー産業の成長、重要インフラに対する政府支出、確立されたR&Dセンター、先進的セキュリティ技術に対する需要などの要因が、この地域の市場成長を促進すると予想されます。
- 同地域におけるサイバー攻撃の増加は、さらに市場成長に寄与しています。2021年、米国国家安全保障局(NSA)、サイバーセキュリティインフラセキュリティ局(CISA)、連邦捜査局(FBI)は、米国における16の重要インフラ部門のうち、国防産業基盤、緊急サービス、食品・農業、政府施設、情報技術部門を含む14部門に対してランサムウェアが関与する事象を確認したと報告しています。
- また、さまざまな組織が、ネットワークの複雑性が過去数年間で増大し、今後5年間も増大し続けることを認めています。そのため、ハッキングやサイバー攻撃による産業プロセスの安全確保を阻止するためのネットワークセキュリティの必要性が高まっており、そこでセキュリティオーケストレーションがその役割を果たしています。
- さらに、この地域では、ハイブリッドとマルチクラウド環境に採用される新しいクラウドツールが爆発的に増加しており、同時に、既存のクラウドプラットフォームは、新しいハイブリッドの現実に適合するように方向転換しています。
セキュリティオーケストレーション産業概要
セキュリティオーケストレーション市場は競争が激しく、複数の大手企業が参入しています。市場シェアでは、現在、少数の大手企業が市場を独占しています。さらに、クラウドネットワークセグメントの出現により、ほとんどの企業がSOAR市場でのプレゼンスを高め、後続市場全体の顧客を獲得しています。さらに、各社は協業やソリューションの立ち上げなど、さまざまな戦略を選択し、市場成長率に貢献しています。例えば
- 2023年3月-IBMとCohesityは、ハイブリッドクラウド環境におけるデータセキュリティと信頼性の向上という組織の本質的なニーズに応えるため、新たなパートナーシップを結びました。IBM Storage Defenderは、ランサムウェア、ヒューマンエラー、攻撃などの脅威から組織のデータレイヤーを保護するために、1つのウィンドウを通じて様々なストレージプラットフォーム全体でAIとイベントモニタリングを使用するように開発されています。
- 2023年2月-サイバー脅威インテリジェンスとセキュリティ運用の最適化に関する顧客のニーズを支援する脅威インテリジェンス企業であるモラドインテリジェンスと、企業やMSSP/MDR向けにローコードSOARと脅威インテリジェンス自動化機能を搭載したサイバーフュージョンセンター、ISACやISAO向けの脅威インテリジェンス共有ソリューションを構築する技術プラットフォームを提供するサイウェアは、パートナーシップを締結しました。このパートナーシップの主要目的は、サイウェアの先進的なTIP & SOARモジュールを使用して、脅威データの効果的な取り込み、強化、分析、対応を行うことで、Moradoの強力な顧客ポートフォリオをより簡単にすることです。
その他の特典
- エクセル形式の市場予測(ME)シート
- 3ヶ月間のアナリストサポート
目次
第1章 イントロダクション
- 調査の前提条件
- 調査範囲
第2章 調査手法
第3章 エグゼクティブサマリー
第4章 市場洞察
- 市場概要
- 産業の魅力-ポーターのファイブフォース分析
- 新規参入業者の脅威
- 買い手/消費者の交渉力
- 供給企業の交渉力
- 代替品の脅威
- 競争企業間の敵対関係の強さ
- COVID-19が市場に与える影響
第5章 市場力学
- 市場促進要因
- シームレスなワークフローを実現するセキュリティ運用の自動化動向の高まり
- ネットワークの複雑性に対応するための個別サイバーセキュリティ技術の必要性
- 市場抑制要因
- 専門家の認識不足
- 技術スナップショット
第6章 市場セグメンテーション
- タイプ
- ソフトウェア
- サービス
- エンドユーザー産業
- BFSI
- IT・通信
- 政府・防衛
- eコマース
- その他
- 地域
- 北米
- 米国
- カナダ
- 欧州
- 英国
- フランス
- ドイツ
- その他の欧州
- アジア太平洋
- 中国
- 日本
- オーストラリア
- その他のアジア太平洋
- その他
- ラテンアメリカ
- 中東・アフリカ
- 北米
第7章 競合情勢
- 企業プロファイル
- IBM Corporation
- Tufin Software Technologies Ltd
- DXC Technology Company
- Cisco System Inc.
- Swimlane LLC
- RSA Security LLC
- FireEye Inc.
- DFLabs SpA
- Palo Alto Networks Inc.
- Siemplify Ltd
- Accenture PLC
- Amazon Web Services Inc.
- Cyberbit Ltd
- Forescout Technologies Inc.
第8章 投資分析
第9章 市場機会と今後の動向
The Security Orchestration Market size is estimated at USD 4.10 billion in 2025, and is expected to reach USD 8.50 billion by 2030, at a CAGR of 15.72% during the forecast period (2025-2030).

The implementation of security orchestration across various organizations can help manage security alerts and prevent severe cyber-attacks. As the sophistication level in cyber-attacks is increasing, security vendors are trying to develop better orchestration platforms to provide proactive and holistic security architecture to handle critical business applications.
Key Highlights
- An increase in the security breaches and occurrences due to dramatic growth in the BYOD trend affecting SMEs, along with the rapid deployment and development of cloud-based solutions, is fueling the application of security orchestration among various organizations.
- A rise in the application of network forensics is expected to drive the market demand, as a growing number of companies are adopting the security orchestration platform to monitor and manage their computer network traffic.
- Growing adoption of various IT enabled services and solutions, due to the growing popularity of connected devices, has further boosted the amount of data generated daily, subsequently resulting in a vast scope for potential vulnerabilities that need effective management and containment.
- Implementation of these solutions has also enabled improved adherence to audit and compliance requirements easily, with proactive policy enforcement and audit and compliance reports, such as ITIL, PCI, Health Insurance Portability and Accountability Act (HIPAA), Sarbanes-Oxley Act (SOX), and Gramm-Leach-Bliley Act. These factors have been aiding the growth of the market.
Security Orchestration Market Trends
IT and Telecommunication Sector is Projected to Record Significant Growth
- The IT and telecommunication industry offers a wide range of global and domestic services for connecting millions of customers. This diverse ecosystem is more prone to frequent cyber attacks, as they are highly dependent on their infrastructure, network, and databases to perform any operation.
- Telecom organizations typically store customers' personal information, such as names, addresses, and financial data. Information-sensitive data is a compelling target for insiders or cyber-criminals to steal money, blackmail customers, or launch further attacks. Therefore, the industry demands a greater focus on updated solutions, the right tools, highly trained personnel, and the ability to respond to threats immediately.
- SOAR tools aid IT teams in defining, standardizing, and automating organizations' incident response activities. Most IT organizations use these tools to automate security operations and processes, respond to incidents, and manage vulnerabilities and threats. Moreover, security orchestration reduces the threat response and resolution time for IT professionals working in enterprise security.
- With the increased data connectivity with the cloud as well as IoT taking center stage in the IT sector, security has been a top priority for the all the organizations in the industry to protect themselves from the data breaches. Further, COVID-19 pandemic has led Information and communication technology organizations to rethink their business processes and improve their network performance to provide their customers with reliable services throughout the pandemic, specially when the demand for telecom networks has doubled. Thus, companies are adopting these security orchestration solutions thereby driving the market growth rate.
North America Accounts for the Largest Market Share
- North America dominates the security orchestration market, owing to many prominent security orchestration vendors across the region, such as IBM Corporation, DXC Technology Company, Cisco System Inc., FireEye Inc., etc. Factors such as the growing end-user industries, government expenditure toward critical infrastructure, well-established R&D centers, and the demand for advanced security technology across the region are expected to drive market growth.
- The growing number of cyber attacks in the region further contributes to the market growth. In 2021, The National Security Agency (NSA), the Cybersecurity and Infrastructure Security Agency (CISA), and the Federal Bureau of Investigation (FBI) reportedly witnessed occurrences involving ransomware against 14 of the 16 critical infrastructure sectors in the United States, including the Defense Industrial Base, Emergency Services, Food and Agriculture, Government Facilities, and Information Technology Sectors.
- Also, various organizations have admitted that network complexity has increased over the past few years and will continue to increase over the next five years. Therefore, there is a high need for network security to stop hacking and cyber-attacks from securing industrial processes, and that is where security orchestration plays its part.
- Further, the region is witnessing an explosion of new cloud tools adopted for hybrid and multicloud environments, while at the same time, established cloud platforms are pivoting to fit into the new hybrid reality.
Security Orchestration Industry Overview
The security orchestration market is highly competitive and consists of several major players. In terms of market share, few major players currently dominate the market. Moreover, due to the emergence of the cloud network segment, most companies are increasing their SOAR market presence, tapping customers across the subsequent markets. Further, the players are opting for various strategies, such as collaborations and solution launches, thereby contributing to the market growth rate. For instance:
- March 2023-IBM and Cohesity have formed a new partnership to meet organizations' essential need for better data security and reliability in hybrid cloud settings. IBM Storage Defender is being developed to use AI and event monitoring across various storage platforms through one single window to assist in safeguarding organizations' data layer from threats, including ransomware, human error, and attack.
- February 2023-Morado Intelligence, a threat intelligence company that assists clients with their needs for cyber threat intelligence and security operations optimisation, and Cyware, a provider of the technology platform to build low-code SOAR and threat intel automation powered Cyber Fusion Centres for businesses and MSSPs/MDRs, as well as threat intelligence sharing solutions for ISACs and ISAOs, have formed a partnership. The partnership's primary objective is to make it easier for Morado's robust client portfolio to use Cyware's advanced TIP & SOAR modules to effectively ingest, enhance, analyze, and respond on threat data.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Attractiveness - Porter's Five Forces Analysis
- 4.2.1 Threat of New Entrants
- 4.2.2 Bargaining Power of Buyers/Consumers
- 4.2.3 Bargaining Power of Suppliers
- 4.2.4 Threat of Substitute Products
- 4.2.5 Intensity of Competitive Rivalry
- 4.3 Impact of COVID-19 on the market
5 Market Dynamics
- 5.1 Market Drivers
- 5.1.1 Rising Trend of Automated Security Operation for Seamless Workflow
- 5.1.2 Need of Disparate Cybersecurity Technologies to Handle Network Complexity
- 5.2 Market Restraints
- 5.2.1 Lack of Awareness among Professionals
- 5.3 Technology Snapshot
6 MARKET SEGMENTATION
- 6.1 Type
- 6.1.1 Software
- 6.1.2 Services
- 6.2 End-user Industry
- 6.2.1 BFSI
- 6.2.2 IT and Telecommunication
- 6.2.3 Government and Defence
- 6.2.4 E-commerce
- 6.2.5 Other End-user Industries
- 6.3 Geography
- 6.3.1 North America
- 6.3.1.1 United States
- 6.3.1.2 Canada
- 6.3.2 Europe
- 6.3.2.1 United Kingdom
- 6.3.2.2 France
- 6.3.2.3 Germany
- 6.3.2.4 Rest of Europe
- 6.3.3 Asia-Pacific
- 6.3.3.1 China
- 6.3.3.2 Japan
- 6.3.3.3 Australia
- 6.3.3.4 Rest of Asia-Pacific
- 6.3.4 Rest of the World
- 6.3.4.1 Latin America
- 6.3.4.2 Middle-East & Africa
- 6.3.1 North America
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 IBM Corporation
- 7.1.2 Tufin Software Technologies Ltd
- 7.1.3 DXC Technology Company
- 7.1.4 Cisco System Inc.
- 7.1.5 Swimlane LLC
- 7.1.6 RSA Security LLC
- 7.1.7 FireEye Inc.
- 7.1.8 DFLabs SpA
- 7.1.9 Palo Alto Networks Inc.
- 7.1.10 Siemplify Ltd
- 7.1.11 Accenture PLC
- 7.1.12 Amazon Web Services Inc.
- 7.1.13 Cyberbit Ltd
- 7.1.14 Forescout Technologies Inc.


