|
|
市場調査レポート
商品コード
1682844
ゼロトラストセキュリティの世界市場の規模、シェア、動向分析レポート(認証別、展開別、企業規模別、タイプ別、最終用途別、地域別、展望と予測、2024~2031年)Global Zero Trust Security Market Size, Share & Trends Analysis Report By Authentication (Single-factor, and Multi-factor), By Deployment (Cloud, and On-Premises), By Enterprise Size, By Type, By End Use, By Regional Outlook and Forecast, 2024 - 2031 |
||||||
|
|||||||
| ゼロトラストセキュリティの世界市場の規模、シェア、動向分析レポート(認証別、展開別、企業規模別、タイプ別、最終用途別、地域別、展望と予測、2024~2031年) |
|
出版日: 2025年03月07日
発行: KBV Research
ページ情報: 英文 344 Pages
納期: 即納可能
|
全表示
- 概要
- 図表
- 目次
ゼロトラストセキュリティ市場規模は、予測期間中に16.1%のCAGRで市場成長し、2031年までに1,013億9,000万米ドルに達すると予想されています。
KBV Cardinal matrixで提示された分析に基づくと、Microsoft Corporationはゼロトラストセキュリティ市場の先駆者です。2024年8月、Microsoft CorporationはNISTと提携してゼロトラスト実践ガイドを立ち上げ、実装のための実用的な手順を提供しました。このコラボレーションは、拡大するゼロトラストセキュリティ市場をサポートし、組織がリスクを軽減し、サイバーセキュリティを強化するために安全なモデルを採用できるようにすることを目指しています。シスコシステムズ社やIBM社などの企業は、ゼロトラストセキュリティ市場の主要なイノベーターの一部です。
市場成長要因
急速に進化するサイバー脅威の情勢は、市場の成長を促す主な要因の1つです。さまざまな業界の組織が、ランサムウェア、フィッシング、内部脅威、高度な持続的脅威(APT)などのサイバー攻撃の急増に見舞われています。これらの攻撃はより高度になり、人工知能(AI)と機械学習(ML)を活用して従来のセキュリティ対策を回避しています。したがって、サイバーセキュリティの必要性に対する意識の高まりと厳格なデータ保護規制が相まって、市場の成長を後押ししています。
さらに、ヘルスケア、製造、スマートシティ、金融サービスにおけるIoTとコネクテッドデバイスの採用の増加により、重大なセキュリティ上の課題が生じています。スマートセンサー、産業用コントローラー、医療機器、コネクテッドビークルなどのIoTデバイスは、堅牢なセキュリティ対策が不足していることが多く、サイバー攻撃に対して脆弱です。これらのデバイスの多くは、デフォルトの認証情報、古いファームウェア、パッチが適用されていない脆弱性で動作しているため、ハッカーが企業ネットワークへのエントリポイントとして悪用する可能性があります。結論として、業界がIoTテクノロジーを統合し続けると、ゼロトラストセキュリティの需要が大幅に高まり、市場の成長が促進されます。
市場抑制要因
ただし、ゼロトラストセキュリティフレームワークを実装するには、アイデンティティおよびアクセス管理(IAM)、エンドポイントセキュリティ、多要素認証(MFA)、ネットワークセグメンテーション、行動分析などの高度なセキュリティテクノロジーに多額の先行投資が必要です。組織は、ゼロトラストセキュリティを既存のITインフラストラクチャに統合するためのリソースも割り当てる必要がありますが、これは複雑でコストがかかる可能性があります。これらのコストは、サイバーセキュリティの予算が限られている中小企業(SME)にとって、導入の大きな妨げになる可能性があります。したがって、初期投資額が高く、継続的な運用コストが高いことが市場の成長を妨げています。
認証展望
認証に基づいて、市場は単一要素と多要素に分類されます。多要素セグメントは、2023年に市場で49%の収益シェアを獲得しました。サイバー脅威、データ侵害、および個人情報詐欺に対する懸念の高まりにより、より強力な認証メカニズムの需要が高まっています。パスワード、生体認証、OTPなどの2つ以上の検証要素を組み合わせた多要素認証(MFA)は、不正アクセスのリスクを軽減することでセキュリティを強化し、 BFSI、ヘルスケア、政府部門などの機密データを扱う業界にとって不可欠なコンポーネントとなっています。
展開展望
展開によって、市場はクラウドとオンプレミスに分かれています。オンプレミスセグメントは、2023年に市場で39%の収益シェアを記録しました。これは、大企業や政府機関がセキュリティインフラストラクチャをより細かく制御したいという好みに起因しています。オンプレミス展開では、データ保護が強化され、規制要件に準拠し、サードパーティのクラウドプロバイダーへの依存が軽減されます。
企業規模展望
企業規模に基づいて、市場は中小企業と大企業に分かれています。中小企業セグメントは、2023年に市場で36%の収益シェアを獲得しました。デジタルトランスフォーメーションとクラウドベースのソリューションの採用が拡大する中、中小企業は強力なサイバーセキュリティ対策の必要性をますます認識しています。ゼロトラストセキュリティは、中小企業に、サイバー攻撃、内部脅威、不正アクセスに対するスケーラブルでコスト効率の高い保護を提供します。これは、進化する脅威情勢においてデータセキュリティと事業継続性を確保するための重要な戦略です。
タイプ展望
タイプ別に見ると、市場はネットワークセキュリティ、データセキュリティ、エンドポイントセキュリティ、オンプレミスセキュリティなどに分類されます。データセキュリティセグメントは、2023年に市場で24%の収益シェアを記録しました。クラウドおよびハイブリッド環境全体で生成および保存される機密データの量が増えるにつれて、組織はデータ中心のセキュリティモデルを優先しています。ゼロトラストフレームワークは、重要なデータを侵害、不正な変更、内部の脅威から保護するための暗号化、アクセス制御、継続的な監視に重点を置いており、堅牢なデータセキュリティソリューションの需要を促進しています。
最終用途展望
最終用途別に見ると、市場はBFSI、ヘルスケア、小売、ITおよび通信、その他に分類されます。ITおよび通信セグメントは、2023年に市場で22%の収益シェアを獲得しました。クラウドコンピューティング、5Gネットワーク、IoT接続の急速な拡大により、ITおよび通信業界におけるサイバーセキュリティのリスクが高まっています。ゼロトラストセキュリティソリューションは、ネットワークインフラストラクチャを保護し、不正アクセスを防ぎ、分散システム間でのデータ交換を保護します。データプライバシーとサイバースパイに対する懸念が高まる中、ITおよび通信企業はゼロトラストモデルを優先してセキュリティの回復力を強化しています。
地域展望
地域別に見ると、市場は北米、欧州、アジア太平洋、LAMEAにわたって分析されています。欧州セグメントは、2023年に市場で30%の収益シェアを記録しました。この地域では、GDPRを含むデータプライバシー規制に重点が置かれており、サイバーセキュリティ体制を強化したい企業の間でゼロトラストフレームワークの採用が加速しています。金融機関、政府機関、ヘルスケア提供者に対するサイバー攻撃の増加により、欧州の組織は、ネットワークセグメンテーション、継続的な認証、エンドポイントセキュリティなどの堅牢なセキュリティソリューションに投資するようになりました。
目次
第1章 市場範囲と調査手法
- 市場の定義
- 目的
- 市場範囲
- セグメンテーション
- 調査手法
第2章 市場要覧
- 主なハイライト
第3章 市場概要
- イントロダクション
- 概要
- 市場構成とシナリオ
- 概要
- 市場に影響を与える主な要因
- 市場促進要因
- 市場抑制要因
- 市場機会
- 市場の課題
第4章 競合分析- 世界
- KBV Cardinal Matrix
- 最近の業界全体の戦略的展開
- パートナーシップ、コラボレーション、および契約
- 製品の発売と製品の拡大
- 買収と合併
- 市場シェア分析、2023年
- 主要成功戦略
- 主な戦略
- 主要な戦略的動き
- ポーターのファイブフォース分析
第5章 世界の市場:認証別
- 世界シングルファクター市場:地域別
- 世界マルチファクター市場:地域別
第6章 世界市場:展開別
- 世界クラウド市場:地域別
- 世界オンプレミス市場:地域別
第7章 世界市場:企業規模別
- 世界大企業市場:地域別
- 世界の中小企業市場:地域別
第8章 世界市場:タイプ別
- 世界のネットワークセキュリティ市場:地域別
- 世界のデータセキュリティ市場:地域別
- 世界のエンドポイントセキュリティ市場:地域別
- 世界のオンプレミスセキュリティ市場:地域別
- 世界のその他のタイプ市場:地域別
第9章 世界市場:最終用途別
- 世界のBFSI市場:地域別
- 世界のIT・通信市場:地域別
- 世界の小売市場:地域別
- 世界のヘルスケア市場:地域別
- 世界のその他の最終用途市場:地域別
第10章 世界市場:地域別
- 北米
- 北米の市場:国別
- 米国
- カナダ
- メキシコ
- その他北米地域
- 北米の市場:国別
- 欧州
- 欧州の市場:国別
- ドイツ
- 英国
- フランス
- ロシア
- スペイン
- イタリア
- その他欧州地域
- 欧州の市場:国別
- アジア太平洋地域
- アジア太平洋の市場:国別
- 中国
- 日本
- インド
- 韓国
- シンガポール
- マレーシア
- その他アジア太平洋地域
- アジア太平洋の市場:国別
- ラテンアメリカ・中東・アフリカ
- ラテンアメリカ・中東・アフリカの市場:国別
- ブラジル
- アルゼンチン
- アラブ首長国連邦
- サウジアラビア
- 南アフリカ
- ナイジェリア
- その他ラテンアメリカ・中東・アフリカ地域
- ラテンアメリカ・中東・アフリカの市場:国別
第11章 企業プロファイル
- Broadcom, Inc
- Microsoft Corporation
- Fortinet, Inc
- Palo Alto Networks, Inc
- IBM Corporation
- Cisco Systems, Inc
- Cloudflare, Inc
- Check Point Software Technologies Ltd
- Crowdstrike Holdings, Inc
- Forcepoint LLC(Francisco Partners)
第12章 ゼロトラストセキュリティ市場の成功必須条件
LIST OF TABLES
- TABLE 1 Global Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 2 Global Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 3 Partnerships, Collaborations and Agreements- Zero Trust Security Market
- TABLE 4 Product Launches And Product Expansions- Zero Trust Security Market
- TABLE 5 Acquisition and Mergers- Zero Trust Security Market
- TABLE 6 Global Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 7 Global Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 8 Global Single-factor Market by Region, 2020 - 2023, USD Million
- TABLE 9 Global Single-factor Market by Region, 2024 - 2031, USD Million
- TABLE 10 Global Multi-factor Market by Region, 2020 - 2023, USD Million
- TABLE 11 Global Multi-factor Market by Region, 2024 - 2031, USD Million
- TABLE 12 Global Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 13 Global Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 14 Global Cloud Market by Region, 2020 - 2023, USD Million
- TABLE 15 Global Cloud Market by Region, 2024 - 2031, USD Million
- TABLE 16 Global On-Premises Market by Region, 2020 - 2023, USD Million
- TABLE 17 Global On-Premises Market by Region, 2024 - 2031, USD Million
- TABLE 18 Global Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 19 Global Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 20 Global Large Enterprises Market by Region, 2020 - 2023, USD Million
- TABLE 21 Global Large Enterprises Market by Region, 2024 - 2031, USD Million
- TABLE 22 Global SMEs Market by Region, 2020 - 2023, USD Million
- TABLE 23 Global SMEs Market by Region, 2024 - 2031, USD Million
- TABLE 24 Global Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 25 Global Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 26 Global Network Security Market by Region, 2020 - 2023, USD Million
- TABLE 27 Global Network Security Market by Region, 2024 - 2031, USD Million
- TABLE 28 Global Data Security Market by Region, 2020 - 2023, USD Million
- TABLE 29 Global Data Security Market by Region, 2024 - 2031, USD Million
- TABLE 30 Global Endpoint Security Market by Region, 2020 - 2023, USD Million
- TABLE 31 Global Endpoint Security Market by Region, 2024 - 2031, USD Million
- TABLE 32 Global On-premises Security Market by Region, 2020 - 2023, USD Million
- TABLE 33 Global On-premises Security Market by Region, 2024 - 2031, USD Million
- TABLE 34 Global Other Type Market by Region, 2020 - 2023, USD Million
- TABLE 35 Global Other Type Market by Region, 2024 - 2031, USD Million
- TABLE 36 Global Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 37 Global Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 38 Global BFSI Market by Region, 2020 - 2023, USD Million
- TABLE 39 Global BFSI Market by Region, 2024 - 2031, USD Million
- TABLE 40 Global IT & Telecom Market by Region, 2020 - 2023, USD Million
- TABLE 41 Global IT & Telecom Market by Region, 2024 - 2031, USD Million
- TABLE 42 Global Retail Market by Region, 2020 - 2023, USD Million
- TABLE 43 Global Retail Market by Region, 2024 - 2031, USD Million
- TABLE 44 Global Healthcare Market by Region, 2020 - 2023, USD Million
- TABLE 45 Global Healthcare Market by Region, 2024 - 2031, USD Million
- TABLE 46 Global Other End Use Market by Region, 2020 - 2023, USD Million
- TABLE 47 Global Other End Use Market by Region, 2024 - 2031, USD Million
- TABLE 48 Global Zero Trust Security Market by Region, 2020 - 2023, USD Million
- TABLE 49 Global Zero Trust Security Market by Region, 2024 - 2031, USD Million
- TABLE 50 North America Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 51 North America Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 52 North America Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 53 North America Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 54 North America Single-factor Market by Region, 2020 - 2023, USD Million
- TABLE 55 North America Single-factor Market by Region, 2024 - 2031, USD Million
- TABLE 56 North America Multi-factor Market by Region, 2020 - 2023, USD Million
- TABLE 57 North America Multi-factor Market by Region, 2024 - 2031, USD Million
- TABLE 58 North America Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 59 North America Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 60 North America Cloud Market by Country, 2020 - 2023, USD Million
- TABLE 61 North America Cloud Market by Country, 2024 - 2031, USD Million
- TABLE 62 North America On-Premises Market by Country, 2020 - 2023, USD Million
- TABLE 63 North America On-Premises Market by Country, 2024 - 2031, USD Million
- TABLE 64 North America Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 65 North America Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 66 North America Large Enterprises Market by Country, 2020 - 2023, USD Million
- TABLE 67 North America Large Enterprises Market by Country, 2024 - 2031, USD Million
- TABLE 68 North America SMEs Market by Country, 2020 - 2023, USD Million
- TABLE 69 North America SMEs Market by Country, 2024 - 2031, USD Million
- TABLE 70 North America Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 71 North America Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 72 North America Network Security Market by Country, 2020 - 2023, USD Million
- TABLE 73 North America Network Security Market by Country, 2024 - 2031, USD Million
- TABLE 74 North America Data Security Market by Country, 2020 - 2023, USD Million
- TABLE 75 North America Data Security Market by Country, 2024 - 2031, USD Million
- TABLE 76 North America Endpoint Security Market by Country, 2020 - 2023, USD Million
- TABLE 77 North America Endpoint Security Market by Country, 2024 - 2031, USD Million
- TABLE 78 North America On-premises Security Market by Country, 2020 - 2023, USD Million
- TABLE 79 North America On-premises Security Market by Country, 2024 - 2031, USD Million
- TABLE 80 North America Other Type Market by Country, 2020 - 2023, USD Million
- TABLE 81 North America Other Type Market by Country, 2024 - 2031, USD Million
- TABLE 82 North America Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 83 North America Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 84 North America BFSI Market by Country, 2020 - 2023, USD Million
- TABLE 85 North America BFSI Market by Country, 2024 - 2031, USD Million
- TABLE 86 North America IT & Telecom Market by Country, 2020 - 2023, USD Million
- TABLE 87 North America IT & Telecom Market by Country, 2024 - 2031, USD Million
- TABLE 88 North America Retail Market by Country, 2020 - 2023, USD Million
- TABLE 89 North America Retail Market by Country, 2024 - 2031, USD Million
- TABLE 90 North America Healthcare Market by Country, 2020 - 2023, USD Million
- TABLE 91 North America Healthcare Market by Country, 2024 - 2031, USD Million
- TABLE 92 North America Other End Use Market by Country, 2020 - 2023, USD Million
- TABLE 93 North America Other End Use Market by Country, 2024 - 2031, USD Million
- TABLE 94 North America Zero Trust Security Market by Country, 2020 - 2023, USD Million
- TABLE 95 North America Zero Trust Security Market by Country, 2024 - 2031, USD Million
- TABLE 96 US Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 97 US Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 98 US Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 99 US Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 100 US Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 101 US Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 102 US Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 103 US Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 104 US Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 105 US Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 106 US Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 107 US Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 108 Canada Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 109 Canada Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 110 Canada Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 111 Canada Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 112 Canada Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 113 Canada Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 114 Canada Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 115 Canada Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 116 Canada Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 117 Canada Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 118 Canada Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 119 Canada Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 120 Mexico Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 121 Mexico Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 122 Mexico Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 123 Mexico Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 124 Mexico Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 125 Mexico Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 126 Mexico Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 127 Mexico Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 128 Mexico Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 129 Mexico Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 130 Mexico Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 131 Mexico Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 132 Rest of North America Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 133 Rest of North America Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 134 Rest of North America Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 135 Rest of North America Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 136 Rest of North America Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 137 Rest of North America Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 138 Rest of North America Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 139 Rest of North America Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 140 Rest of North America Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 141 Rest of North America Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 142 Rest of North America Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 143 Rest of North America Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 144 Europe Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 145 Europe Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 146 Europe Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 147 Europe Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 148 Europe Single-factor Market by Country, 2020 - 2023, USD Million
- TABLE 149 Europe Single-factor Market by Country, 2024 - 2031, USD Million
- TABLE 150 Europe Multi-factor Market by Country, 2020 - 2023, USD Million
- TABLE 151 Europe Multi-factor Market by Country, 2024 - 2031, USD Million
- TABLE 152 Europe Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 153 Europe Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 154 Europe Cloud Market by Country, 2020 - 2023, USD Million
- TABLE 155 Europe Cloud Market by Country, 2024 - 2031, USD Million
- TABLE 156 Europe On-Premises Market by Country, 2020 - 2023, USD Million
- TABLE 157 Europe On-Premises Market by Country, 2024 - 2031, USD Million
- TABLE 158 Europe Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 159 Europe Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 160 Europe Large Enterprises Market by Country, 2020 - 2023, USD Million
- TABLE 161 Europe Large Enterprises Market by Country, 2024 - 2031, USD Million
- TABLE 162 Europe SMEs Market by Country, 2020 - 2023, USD Million
- TABLE 163 Europe SMEs Market by Country, 2024 - 2031, USD Million
- TABLE 164 Europe Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 165 Europe Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 166 Europe Network Security Market by Country, 2020 - 2023, USD Million
- TABLE 167 Europe Network Security Market by Country, 2024 - 2031, USD Million
- TABLE 168 Europe Data Security Market by Country, 2020 - 2023, USD Million
- TABLE 169 Europe Data Security Market by Country, 2024 - 2031, USD Million
- TABLE 170 Europe Endpoint Security Market by Country, 2020 - 2023, USD Million
- TABLE 171 Europe Endpoint Security Market by Country, 2024 - 2031, USD Million
- TABLE 172 Europe On-premises Security Market by Country, 2020 - 2023, USD Million
- TABLE 173 Europe On-premises Security Market by Country, 2024 - 2031, USD Million
- TABLE 174 Europe Other Type Market by Country, 2020 - 2023, USD Million
- TABLE 175 Europe Other Type Market by Country, 2024 - 2031, USD Million
- TABLE 176 Europe Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 177 Europe Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 178 Europe BFSI Market by Country, 2020 - 2023, USD Million
- TABLE 179 Europe BFSI Market by Country, 2024 - 2031, USD Million
- TABLE 180 Europe IT & Telecom Market by Country, 2020 - 2023, USD Million
- TABLE 181 Europe IT & Telecom Market by Country, 2024 - 2031, USD Million
- TABLE 182 Europe Retail Market by Country, 2020 - 2023, USD Million
- TABLE 183 Europe Retail Market by Country, 2024 - 2031, USD Million
- TABLE 184 Europe Healthcare Market by Country, 2020 - 2023, USD Million
- TABLE 185 Europe Healthcare Market by Country, 2024 - 2031, USD Million
- TABLE 186 Europe Other End Use Market by Country, 2020 - 2023, USD Million
- TABLE 187 Europe Other End Use Market by Country, 2024 - 2031, USD Million
- TABLE 188 Europe Zero Trust Security Market by Country, 2020 - 2023, USD Million
- TABLE 189 Europe Zero Trust Security Market by Country, 2024 - 2031, USD Million
- TABLE 190 Germany Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 191 Germany Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 192 Germany Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 193 Germany Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 194 Germany Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 195 Germany Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 196 Germany Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 197 Germany Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 198 Germany Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 199 Germany Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 200 Germany Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 201 Germany Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 202 UK Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 203 UK Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 204 UK Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 205 UK Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 206 UK Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 207 UK Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 208 UK Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 209 UK Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 210 UK Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 211 UK Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 212 UK Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 213 UK Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 214 France Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 215 France Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 216 France Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 217 France Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 218 France Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 219 France Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 220 France Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 221 France Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 222 France Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 223 France Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 224 France Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 225 France Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 226 Russia Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 227 Russia Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 228 Russia Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 229 Russia Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 230 Russia Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 231 Russia Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 232 Russia Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 233 Russia Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 234 Russia Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 235 Russia Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 236 Russia Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 237 Russia Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 238 Spain Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 239 Spain Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 240 Spain Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 241 Spain Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 242 Spain Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 243 Spain Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 244 Spain Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 245 Spain Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 246 Spain Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 247 Spain Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 248 Spain Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 249 Spain Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 250 Italy Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 251 Italy Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 252 Italy Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 253 Italy Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 254 Italy Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 255 Italy Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 256 Italy Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 257 Italy Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 258 Italy Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 259 Italy Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 260 Italy Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 261 Italy Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 262 Rest of Europe Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 263 Rest of Europe Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 264 Rest of Europe Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 265 Rest of Europe Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 266 Rest of Europe Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 267 Rest of Europe Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 268 Rest of Europe Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 269 Rest of Europe Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 270 Rest of Europe Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 271 Rest of Europe Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 272 Rest of Europe Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 273 Rest of Europe Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 274 Asia Pacific Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 275 Asia Pacific Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 276 Asia Pacific Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 277 Asia Pacific Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 278 Asia Pacific Single-factor Market by Country, 2020 - 2023, USD Million
- TABLE 279 Asia Pacific Single-factor Market by Country, 2024 - 2031, USD Million
- TABLE 280 Asia Pacific Multi-factor Market by Country, 2020 - 2023, USD Million
- TABLE 281 Asia Pacific Multi-factor Market by Country, 2024 - 2031, USD Million
- TABLE 282 Asia Pacific Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 283 Asia Pacific Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 284 Asia Pacific Cloud Market by Country, 2020 - 2023, USD Million
- TABLE 285 Asia Pacific Cloud Market by Country, 2024 - 2031, USD Million
- TABLE 286 Asia Pacific On-Premises Market by Country, 2020 - 2023, USD Million
- TABLE 287 Asia Pacific On-Premises Market by Country, 2024 - 2031, USD Million
- TABLE 288 Asia Pacific Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 289 Asia Pacific Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 290 Asia Pacific Large Enterprises Market by Country, 2020 - 2023, USD Million
- TABLE 291 Asia Pacific Large Enterprises Market by Country, 2024 - 2031, USD Million
- TABLE 292 Asia Pacific SMEs Market by Country, 2020 - 2023, USD Million
- TABLE 293 Asia Pacific SMEs Market by Country, 2024 - 2031, USD Million
- TABLE 294 Asia Pacific Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 295 Asia Pacific Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 296 Asia Pacific Network Security Market by Country, 2020 - 2023, USD Million
- TABLE 297 Asia Pacific Network Security Market by Country, 2024 - 2031, USD Million
- TABLE 298 Asia Pacific Data Security Market by Country, 2020 - 2023, USD Million
- TABLE 299 Asia Pacific Data Security Market by Country, 2024 - 2031, USD Million
- TABLE 300 Asia Pacific Endpoint Security Market by Country, 2020 - 2023, USD Million
- TABLE 301 Asia Pacific Endpoint Security Market by Country, 2024 - 2031, USD Million
- TABLE 302 Asia Pacific On-premises Security Market by Country, 2020 - 2023, USD Million
- TABLE 303 Asia Pacific On-premises Security Market by Country, 2024 - 2031, USD Million
- TABLE 304 Asia Pacific Other Type Market by Country, 2020 - 2023, USD Million
- TABLE 305 Asia Pacific Other Type Market by Country, 2024 - 2031, USD Million
- TABLE 306 Asia Pacific Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 307 Asia Pacific Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 308 Asia Pacific BFSI Market by Country, 2020 - 2023, USD Million
- TABLE 309 Asia Pacific BFSI Market by Country, 2024 - 2031, USD Million
- TABLE 310 Asia Pacific IT & Telecom Market by Country, 2020 - 2023, USD Million
- TABLE 311 Asia Pacific IT & Telecom Market by Country, 2024 - 2031, USD Million
- TABLE 312 Asia Pacific Retail Market by Country, 2020 - 2023, USD Million
- TABLE 313 Asia Pacific Retail Market by Country, 2024 - 2031, USD Million
- TABLE 314 Asia Pacific Healthcare Market by Country, 2020 - 2023, USD Million
- TABLE 315 Asia Pacific Healthcare Market by Country, 2024 - 2031, USD Million
- TABLE 316 Asia Pacific Other End Use Market by Country, 2020 - 2023, USD Million
- TABLE 317 Asia Pacific Other End Use Market by Country, 2024 - 2031, USD Million
- TABLE 318 Asia Pacific Zero Trust Security Market by Country, 2020 - 2023, USD Million
- TABLE 319 Asia Pacific Zero Trust Security Market by Country, 2024 - 2031, USD Million
- TABLE 320 China Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 321 China Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 322 China Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 323 China Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 324 China Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 325 China Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 326 China Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 327 China Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 328 China Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 329 China Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 330 China Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 331 China Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 332 Japan Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 333 Japan Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 334 Japan Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 335 Japan Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 336 Japan Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 337 Japan Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 338 Japan Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 339 Japan Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 340 Japan Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 341 Japan Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 342 Japan Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 343 Japan Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 344 India Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 345 India Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 346 India Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 347 India Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 348 India Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 349 India Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 350 India Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 351 India Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 352 India Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 353 India Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 354 India Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 355 India Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 356 South Korea Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 357 South Korea Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 358 South Korea Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 359 South Korea Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 360 South Korea Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 361 South Korea Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 362 South Korea Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 363 South Korea Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 364 South Korea Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 365 South Korea Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 366 South Korea Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 367 South Korea Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 368 Singapore Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 369 Singapore Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 370 Singapore Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 371 Singapore Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 372 Singapore Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 373 Singapore Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 374 Singapore Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 375 Singapore Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 376 Singapore Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 377 Singapore Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 378 Singapore Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 379 Singapore Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 380 Malaysia Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 381 Malaysia Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 382 Malaysia Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 383 Malaysia Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 384 Malaysia Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 385 Malaysia Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 386 Malaysia Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 387 Malaysia Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 388 Malaysia Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 389 Malaysia Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 390 Malaysia Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 391 Malaysia Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 392 Rest of Asia Pacific Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 393 Rest of Asia Pacific Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 394 Rest of Asia Pacific Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 395 Rest of Asia Pacific Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 396 Rest of Asia Pacific Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 397 Rest of Asia Pacific Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 398 Rest of Asia Pacific Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 399 Rest of Asia Pacific Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 400 Rest of Asia Pacific Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 401 Rest of Asia Pacific Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 402 Rest of Asia Pacific Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 403 Rest of Asia Pacific Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 404 LAMEA Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 405 LAMEA Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 406 LAMEA Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 407 LAMEA Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 408 LAMEA Single-factor Market by Country, 2020 - 2023, USD Million
- TABLE 409 LAMEA Single-factor Market by Country, 2024 - 2031, USD Million
- TABLE 410 LAMEA Multi-factor Market by Country, 2020 - 2023, USD Million
- TABLE 411 LAMEA Multi-factor Market by Country, 2024 - 2031, USD Million
- TABLE 412 LAMEA Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 413 LAMEA Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 414 LAMEA Cloud Market by Country, 2020 - 2023, USD Million
- TABLE 415 LAMEA Cloud Market by Country, 2024 - 2031, USD Million
- TABLE 416 LAMEA On-Premises Market by Country, 2020 - 2023, USD Million
- TABLE 417 LAMEA On-Premises Market by Country, 2024 - 2031, USD Million
- TABLE 418 LAMEA Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 419 LAMEA Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 420 LAMEA Large Enterprises Market by Country, 2020 - 2023, USD Million
- TABLE 421 LAMEA Large Enterprises Market by Country, 2024 - 2031, USD Million
- TABLE 422 LAMEA SMEs Market by Country, 2020 - 2023, USD Million
- TABLE 423 LAMEA SMEs Market by Country, 2024 - 2031, USD Million
- TABLE 424 LAMEA Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 425 LAMEA Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 426 LAMEA Network Security Market by Country, 2020 - 2023, USD Million
- TABLE 427 LAMEA Network Security Market by Country, 2024 - 2031, USD Million
- TABLE 428 LAMEA Data Security Market by Country, 2020 - 2023, USD Million
- TABLE 429 LAMEA Data Security Market by Country, 2024 - 2031, USD Million
- TABLE 430 LAMEA Endpoint Security Market by Country, 2020 - 2023, USD Million
- TABLE 431 LAMEA Endpoint Security Market by Country, 2024 - 2031, USD Million
- TABLE 432 LAMEA On-premises Security Market by Country, 2020 - 2023, USD Million
- TABLE 433 LAMEA On-premises Security Market by Country, 2024 - 2031, USD Million
- TABLE 434 LAMEA Other Type Market by Country, 2020 - 2023, USD Million
- TABLE 435 LAMEA Other Type Market by Country, 2024 - 2031, USD Million
- TABLE 436 LAMEA Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 437 LAMEA Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 438 LAMEA BFSI Market by Country, 2020 - 2023, USD Million
- TABLE 439 LAMEA BFSI Market by Country, 2024 - 2031, USD Million
- TABLE 440 LAMEA IT & Telecom Market by Country, 2020 - 2023, USD Million
- TABLE 441 LAMEA IT & Telecom Market by Country, 2024 - 2031, USD Million
- TABLE 442 LAMEA Retail Market by Country, 2020 - 2023, USD Million
- TABLE 443 LAMEA Retail Market by Country, 2024 - 2031, USD Million
- TABLE 444 LAMEA Healthcare Market by Country, 2020 - 2023, USD Million
- TABLE 445 LAMEA Healthcare Market by Country, 2024 - 2031, USD Million
- TABLE 446 LAMEA Other End Use Market by Country, 2020 - 2023, USD Million
- TABLE 447 LAMEA Other End Use Market by Country, 2024 - 2031, USD Million
- TABLE 448 LAMEA Zero Trust Security Market by Country, 2020 - 2023, USD Million
- TABLE 449 LAMEA Zero Trust Security Market by Country, 2024 - 2031, USD Million
- TABLE 450 Brazil Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 451 Brazil Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 452 Brazil Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 453 Brazil Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 454 Brazil Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 455 Brazil Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 456 Brazil Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 457 Brazil Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 458 Brazil Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 459 Brazil Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 460 Brazil Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 461 Brazil Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 462 Argentina Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 463 Argentina Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 464 Argentina Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 465 Argentina Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 466 Argentina Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 467 Argentina Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 468 Argentina Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 469 Argentina Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 470 Argentina Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 471 Argentina Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 472 Argentina Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 473 Argentina Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 474 UAE Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 475 UAE Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 476 UAE Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 477 UAE Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 478 UAE Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 479 UAE Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 480 UAE Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 481 UAE Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 482 UAE Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 483 UAE Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 484 UAE Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 485 UAE Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 486 Saudi Arabia Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 487 Saudi Arabia Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 488 Saudi Arabia Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 489 Saudi Arabia Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 490 Saudi Arabia Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 491 Saudi Arabia Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 492 Saudi Arabia Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 493 Saudi Arabia Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 494 Saudi Arabia Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 495 Saudi Arabia Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 496 Saudi Arabia Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 497 Saudi Arabia Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 498 South Africa Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 499 South Africa Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 500 South Africa Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 501 South Africa Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 502 South Africa Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 503 South Africa Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 504 South Africa Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 505 South Africa Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 506 South Africa Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 507 South Africa Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 508 South Africa Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 509 South Africa Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 510 Nigeria Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 511 Nigeria Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 512 Nigeria Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 513 Nigeria Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 514 Nigeria Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 515 Nigeria Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 516 Nigeria Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 517 Nigeria Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 518 Nigeria Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 519 Nigeria Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 520 Nigeria Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 521 Nigeria Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 522 Rest of LAMEA Zero Trust Security Market, 2020 - 2023, USD Million
- TABLE 523 Rest of LAMEA Zero Trust Security Market, 2024 - 2031, USD Million
- TABLE 524 Rest of LAMEA Zero Trust Security Market by Authentication, 2020 - 2023, USD Million
- TABLE 525 Rest of LAMEA Zero Trust Security Market by Authentication, 2024 - 2031, USD Million
- TABLE 526 Rest of LAMEA Zero Trust Security Market by Deployment, 2020 - 2023, USD Million
- TABLE 527 Rest of LAMEA Zero Trust Security Market by Deployment, 2024 - 2031, USD Million
- TABLE 528 Rest of LAMEA Zero Trust Security Market by Enterprise Size, 2020 - 2023, USD Million
- TABLE 529 Rest of LAMEA Zero Trust Security Market by Enterprise Size, 2024 - 2031, USD Million
- TABLE 530 Rest of LAMEA Zero Trust Security Market by Type, 2020 - 2023, USD Million
- TABLE 531 Rest of LAMEA Zero Trust Security Market by Type, 2024 - 2031, USD Million
- TABLE 532 Rest of LAMEA Zero Trust Security Market by End Use, 2020 - 2023, USD Million
- TABLE 533 Rest of LAMEA Zero Trust Security Market by End Use, 2024 - 2031, USD Million
- TABLE 534 Key Information - Broadcom, Inc.
- TABLE 535 Key Information - Microsoft Corporation
- TABLE 536 Key Information - Fortinet, Inc.
- TABLE 537 Key Information - Palo Alto Networks, Inc.
- TABLE 538 Key Information - IBM Corporation
- TABLE 539 Key Information - Cisco Systems, Inc.
- TABLE 540 Key Information - Cloudflare, Inc.
- TABLE 541 Key Information - Check Point Software Technologies Ltd.
- TABLE 542 Key Information - Crowdstrike Holdings, Inc.
- TABLE 543 Key Information - Forcepoint LLC
LIST OF FIGURES
- FIG 1 Methodology for the research
- FIG 2 Global Zero Trust Security Market, 2020 - 2031, USD Million
- FIG 3 Key Factors Impacting Zero Trust Security Market
- FIG 4 KBV Cardinal Matrix
- FIG 5 Market Share Analysis, 2023
- FIG 6 Key Leading Strategies: Percentage Distribution (2020-2024)
- FIG 7 Key Strategic Move: (Partnerships, Collaborations & Agreements: 2022, Aug - 2025, Feb Leading Players
- FIG 8 Porter's Five Forces Analysis - Zero Trust Security Market
- FIG 9 Global Zero Trust Security Market share by Authentication, 2023
- FIG 10 Global Zero Trust Security Market share by Authentication, 2031
- FIG 11 Global Zero Trust Security Market by Authentication, 2020 - 2031, USD Million
- FIG 12 Global Zero Trust Security Market share by Deployment, 2023
- FIG 13 Global Zero Trust Security Market share by Deployment, 2031
- FIG 14 Global Zero Trust Security Market by Deployment, 2020 - 2031, USD Million
- FIG 15 Global Zero Trust Security Market share by Enterprise Size, 2023
- FIG 16 Global Zero Trust Security Market share by Enterprise Size, 2031
- FIG 17 Global Zero Trust Security Market by Enterprise Size, 2020 - 2031, USD Million
- FIG 18 Global Zero Trust Security Market share by Type, 2023
- FIG 19 Global Zero Trust Security Market share by Type, 2031
- FIG 20 Global Zero Trust Security Market by Type, 2020 - 2031, USD Million
- FIG 21 Global Zero Trust Security Market share by End Use, 2023
- FIG 22 Global Zero Trust Security Market share by End Use, 2031
- FIG 23 Global Zero Trust Security Market by End Use, 2020 - 2031, USD Million
- FIG 24 Global Zero Trust Security Market share by Region, 2023
- FIG 25 Global Zero Trust Security Market share by Region, 2031
- FIG 26 Global Zero Trust Security Market by Region, 2020 - 2031, USD Million
- FIG 27 SWOT Analysis: Broadcom, Inc.
- FIG 28 Recent strategies and developments: Microsoft Corporation
- FIG 29 SWOT Analysis: Microsoft Corporation
- FIG 30 Recent strategies and developments: Fortinet, Inc.
- FIG 31 SWOT Analysis: Fortinet, Inc.'
- FIG 32 Recent strategies and developments: PALO ALTO NETWORKS, INC.
- FIG 33 SWOT Analysis: PALO ALTO NETWORKS, INC.
- FIG 34 Recent strategies and developments: IBM Corporation
- FIG 35 SWOT Analysis: IBM Corporation
- FIG 36 SWOT Analysis: Cisco Systems, Inc.
- FIG 37 SWOT Analysis: Cloudflare, Inc.
- FIG 38 SWOT Analysis: CHECK POINT SOFTWARE TECHNOLOGIES LTD.
- FIG 39 SWOT Analysis: CROWDSTRIKE HOLDINGS, INC.
- FIG 40 SWOT Analysis: Forcepoint LLC
The Global Zero Trust Security Market size is expected to reach $101.39 billion by 2031, rising at a market growth of 16.1% CAGR during the forecast period.
The North America segment recorded 34% revenue share in the market in 2023. This dominance was driven by the high adoption of advanced cybersecurity solutions, stringent regulatory frameworks, and the increasing frequency of cyber threats targeting enterprises and government institutions. The presence of major cybersecurity vendors, growing investments in cloud security, and the rapid expansion of remote work environments further fuelled the demand for zero-trust security solutions across industries such as BFSI, healthcare, and IT & telecom.
The major strategies followed by the market participants are Partnerships as the key developmental strategy to keep pace with the changing demands of end users. For instance, In November, 2024, Cisco Systems, Inc. and LTIMindtree expanded their partnership to offer next-generation Secure Access Service Edge (SASE) solutions, incorporating Zero Trust Network Access (ZTNA) and AI. This collaboration enhances secure hybrid work experiences and simplifies IT management for global clients. Moreover, In February, 2025, Check Point Software and Wiz have partnered to enhance hybrid cloud security by integrating cloud network security with Cloud Native Application Protection (CNAPP). This collaboration aims to provide unified security insights, optimized operations, and strengthened protection, aligning with Zero Trust principles.
Based on the Analysis presented in the KBV Cardinal matrix; Microsoft Corporation is the forerunners in the Zero Trust Security Market. In August, 2024, Microsoft Corporation partnered with NIST to launch a Zero Trust practice guide, offering practical steps for implementation. This collaboration aims to support the expanding Zero Trust security market, helping organizations adopt secure models to mitigate risks and strengthen cybersecurity. Companies such as Cisco Systems, Inc. and IBM Corporation are some of the key innovators in Zero Trust Security Market.
Market Growth Factors
The rapidly evolving cyber threat landscape is one of the primary drivers for the growth of the market. Organizations across industries are experiencing an alarming rise in cyberattacks, including ransomware, phishing, insider threats, and advanced persistent threats (APTs). These attacks are becoming more sophisticated, leveraging artificial intelligence (AI) and machine learning (ML) to bypass traditional security measures. Thus, the increasing awareness about the necessity of cybersecurity, coupled with strict data protection regulations, is fuelling the growth of the market.
Additionally, The growing adoption of IoT and connected devices in healthcare, manufacturing, smart cities, and financial services has created significant security challenges. IoT devices, including smart sensors, industrial controllers, medical equipment, and connected vehicles, often lack robust security measures, making them vulnerable to cyberattacks. Many of these devices operate with default credentials, outdated firmware, and unpatched vulnerabilities, allowing hackers to exploit them as entry points into enterprise networks. In conclusion, as industries continue integrating IoT technologies, the demand for zero trust security will rise significantly, driving market growth.
Market Restraining Factors
However, Implementing a zero trust security framework requires a significant upfront investment in advanced security technologies, including identity and access management (IAM), endpoint security, multi-factor authentication (MFA), network segmentation, and behavioural analytics. Organizations must also allocate resources for integrating zero trust security with existing IT infrastructure, which can be complex and costly. These costs can be a major deterrent to adoption for small and medium-sized enterprises (SMEs) with limited cybersecurity budgets. Hence, high initial investment and ongoing operational costs are impeding the growth of the market.
Authentication Outlook
Based on authentication, the market is characterized into single-factor and multi-factor. The multi-factor segment procured 49% revenue share in the market in 2023. Rising concerns over cyber threats, data breaches, and identity fraud have fuelled the demand for stronger authentication mechanisms. Multi-factor authentication (MFA), which combines two or more verification factors-such as passwords, biometrics, and OTPs-enhances security by reducing the risk of unauthorized access, making it an essential component for industries handling sensitive data, including BFSI, healthcare, and government sectors.
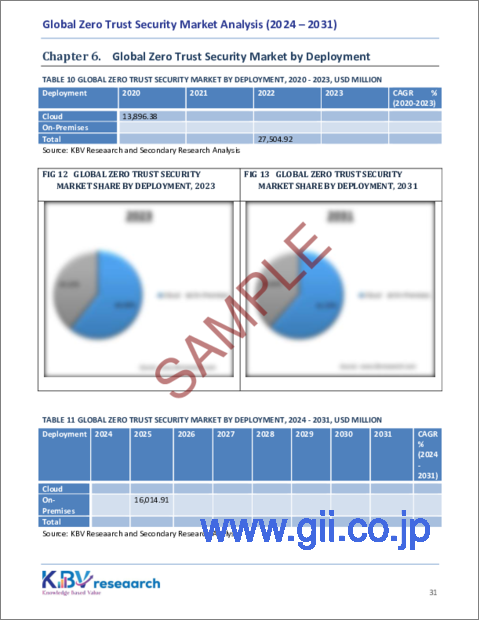
Deployment Outlook
By deployment, the market is divided into cloud and on-premises. The on-premises segment witnessed 39% revenue share in the market in 2023. This is driven by the preference of large enterprises and government organizations for greater control over their security infrastructure. On-premises deployment offers enhanced data protection, compliance with regulatory requirements, and reduced reliance on third-party cloud providers.
Enterprise Size Outlook
Based on enterprise size, the market is segmented into SMEs and large enterprises. The SMEs segment acquired 36% revenue share in the market in 2023. With the growing adoption of digital transformation and cloud-based solutions, SMEs increasingly recognize the need for strong cybersecurity measures. Zero-trust security offers SMEs scalable and cost-effective protection against cyberattacks, insider threats, and unauthorized access. It is an essential strategy for ensuring data security and business continuity in an evolving threat landscape.
Type Outlook
On the basis of type, the market is classified into network security, data security, endpoint security, on-premises security, and others. The data security segment recorded 24% revenue share in the market in 2023. With the growing volume of sensitive data generated and stored across cloud and hybrid environments, organizations are prioritizing data-centric security models. Zero-trust frameworks focus on encryption, access controls, and continuous monitoring to protect critical data from breaches, unauthorized modifications, and insider threats, driving demand for robust data security solutions.
End Use Outlook
By end use, the market is divided into BFSI, healthcare, retail, IT & telecom, and others. The IT & telecom segment procured 22% revenue share in the market in 2023. The rapid expansion of cloud computing, 5G networks, and IoT connectivity has increased cybersecurity risks in the IT and telecom industry. Zero-trust security solutions protect network infrastructure, prevent unauthorized access, and secure data exchanges across distributed systems. With growing concerns over data privacy and cyber espionage, IT and telecom companies prioritize zero-trust models to enhance security resilience.
Regional Outlook
Region-wise, the market is analyzed across North America, Europe, Asia Pacific, and LAMEA. The Europe segment witnessed 30% revenue share in the market in 2023. The region's strong emphasis on data privacy regulations, including GDPR, has accelerated the adoption of zero-trust frameworks among enterprises looking to enhance their cybersecurity posture. Increasing cyberattacks on financial institutions, government agencies, and healthcare providers have prompted European organizations to invest in robust security solutions, including network segmentation, continuous authentication, and endpoint security.
Recent Strategies Deployed in the Market
- Jan-2025: IBM Corporation has acquired Applications Software Technology to strengthen its Oracle Cloud expertise, with a focus on public sector cloud transformations, enhancing its ability to support clients in North America, the UK, and Ireland with Oracle Cloud solutions.
- Dec-2024: Microsoft Corporation expands its product offerings to support U.S. government agencies in adopting Zero Trust principles, aligning with the CISA Zero Trust Maturity Model. Key services like Entra ID and Defender XDR enhance identity management, security, and risk-based access control.
- Aug-2024: Fortinet, Inc. acquired Lacework, enhancing its cloud-native security capabilities by integrating Lacework's platform with Fortinet's Security Fabric, bolstering its AI-driven, Zero Trust security solutions for comprehensive protection across cloud and on-premises environments.
- May-2024: Palo Alto Networks and IBM announced a partnership to provide AI-powered security solutions. IBM will integrate Palo Alto Networks' platforms, including Cortex XSIAM and Prisma SASE 3.0, for advanced threat protection and zero-trust security in hybrid cloud and AI environments.
- May-2024: CrowdStrike Holdings, Inc. and Cloudflare expanded their partnership to enhance security with a combination of Zero Trust protection and AI-native cybersecurity. This collaboration strengthens defense across networks, devices, endpoints, cloud, identity, data, and applications, aiming to prevent breaches at scale.
List of Key Companies Profiled
- Broadcom, Inc.
- Microsoft Corporation
- Fortinet, Inc.
- Palo Alto Networks, Inc.
- IBM Corporation
- Cisco Systems, Inc.
- Cloudflare, Inc.
- Check Point Software Technologies Ltd.
- CrowdStrike Holdings, Inc.
- Forcepoint LLC (Francisco Partners)
Global Zero Trust Security Market Report Segmentation
By Authentication
- Single-factor
- Multi-factor
By Deployment
- Cloud
- On-Premises
By Enterprise Size
- Large Enterprises
- SMEs
By Type
- Network Security
- Data Security
- Endpoint Security
- On-premises Security
- Other Type
By End Use
- BFSI
- IT & Telecom
- Retail
- Healthcare
- Other End Use
By Geography
- North America
- US
- Canada
- Mexico
- Rest of North America
- Europe
- Germany
- UK
- France
- Russia
- Spain
- Italy
- Rest of Europe
- Asia Pacific
- China
- Japan
- India
- South Korea
- Singapore
- Malaysia
- Rest of Asia Pacific
- LAMEA
- Brazil
- Argentina
- UAE
- Saudi Arabia
- South Africa
- Nigeria
- Rest of LAMEA
Table of Contents
Chapter 1. Market Scope & Methodology
- 1.1 Market Definition
- 1.2 Objectives
- 1.3 Market Scope
- 1.4 Segmentation
- 1.4.1 Global Zero Trust Security Market, by Authentication
- 1.4.2 Global Zero Trust Security Market, by Deployment
- 1.4.3 Global Zero Trust Security Market, by Enterprise Size
- 1.4.4 Global Zero Trust Security Market, by Type
- 1.4.5 Global Zero Trust Security Market, by End Use
- 1.4.6 Global Zero Trust Security Market, by Geography
- 1.5 Methodology for the research
Chapter 2. Market at a Glance
- 2.1 Key Highlights
Chapter 3. Market Overview
- 3.1 Introduction
- 3.1.1 Overview
- 3.1.1.1 Market Composition and Scenario
- 3.1.1 Overview
- 3.2 Key Factors Impacting the Market
- 3.2.1 Market Drivers
- 3.2.2 Market Restraints
- 3.2.3 Market Opportunities
- 3.2.4 Market Challenges
Chapter 4. Competition Analysis - Global
- 4.1 KBV Cardinal Matrix
- 4.2 Recent Industry Wide Strategic Developments
- 4.2.1 Partnerships, Collaborations and Agreements
- 4.2.2 Product Launches and Product Expansions
- 4.2.3 Acquisition and Mergers
- 4.3 Market Share Analysis, 2023
- 4.4 Top Winning Strategies
- 4.4.1 Key Leading Strategies: Percentage Distribution (2020-2024)
- 4.4.2 Key Strategic Move: (Partnerships, Collaborations & Agreements: 2022, Aug - 2025, Feb) Leading Players
- 4.5 Porter Five Forces Analysis
Chapter 5. Global Zero Trust Security Market by Authentication
- 5.1 Global Single-factor Market by Region
- 5.2 Global Multi-factor Market by Region
Chapter 6. Global Zero Trust Security Market by Deployment
- 6.1 Global Cloud Market by Region
- 6.2 Global On-Premises Market by Region
Chapter 7. Global Zero Trust Security Market by Enterprise Size
- 7.1 Global Large Enterprises Market by Region
- 7.2 Global SMEs Market by Region
Chapter 8. Global Zero Trust Security Market by Type
- 8.1 Global Network Security Market by Region
- 8.2 Global Data Security Market by Region
- 8.3 Global Endpoint Security Market by Region
- 8.4 Global On-premises Security Market by Region
- 8.5 Global Other Type Market by Region
Chapter 9. Global Zero Trust Security Market by End Use
- 9.1 Global BFSI Market by Region
- 9.2 Global IT & Telecom Market by Region
- 9.3 Global Retail Market by Region
- 9.4 Global Healthcare Market by Region
- 9.5 Global Other End Use Market by Region
Chapter 10. Global Zero Trust Security Market by Region
- 10.1 North America Zero Trust Security Market
- 10.1.1 North America Zero Trust Security Market by Authentication
- 10.1.1.1 North America Single-factor Market by Region
- 10.1.1.2 North America Multi-factor Market by Region
- 10.1.2 North America Zero Trust Security Market by Deployment
- 10.1.2.1 North America Cloud Market by Country
- 10.1.2.2 North America On-Premises Market by Country
- 10.1.3 North America Zero Trust Security Market by Enterprise Size
- 10.1.3.1 North America Large Enterprises Market by Country
- 10.1.3.2 North America SMEs Market by Country
- 10.1.4 North America Zero Trust Security Market by Type
- 10.1.4.1 North America Network Security Market by Country
- 10.1.4.2 North America Data Security Market by Country
- 10.1.4.3 North America Endpoint Security Market by Country
- 10.1.4.4 North America On-premises Security Market by Country
- 10.1.4.5 North America Other Type Market by Country
- 10.1.5 North America Zero Trust Security Market by End Use
- 10.1.5.1 North America BFSI Market by Country
- 10.1.5.2 North America IT & Telecom Market by Country
- 10.1.5.3 North America Retail Market by Country
- 10.1.5.4 North America Healthcare Market by Country
- 10.1.5.5 North America Other End Use Market by Country
- 10.1.6 North America Zero Trust Security Market by Country
- 10.1.6.1 US Zero Trust Security Market
- 10.1.6.1.1 US Zero Trust Security Market by Authentication
- 10.1.6.1.2 US Zero Trust Security Market by Deployment
- 10.1.6.1.3 US Zero Trust Security Market by Enterprise Size
- 10.1.6.1.4 US Zero Trust Security Market by Type
- 10.1.6.1.5 US Zero Trust Security Market by End Use
- 10.1.6.2 Canada Zero Trust Security Market
- 10.1.6.2.1 Canada Zero Trust Security Market by Authentication
- 10.1.6.2.2 Canada Zero Trust Security Market by Deployment
- 10.1.6.2.3 Canada Zero Trust Security Market by Enterprise Size
- 10.1.6.2.4 Canada Zero Trust Security Market by Type
- 10.1.6.2.5 Canada Zero Trust Security Market by End Use
- 10.1.6.3 Mexico Zero Trust Security Market
- 10.1.6.3.1 Mexico Zero Trust Security Market by Authentication
- 10.1.6.3.2 Mexico Zero Trust Security Market by Deployment
- 10.1.6.3.3 Mexico Zero Trust Security Market by Enterprise Size
- 10.1.6.3.4 Mexico Zero Trust Security Market by Type
- 10.1.6.3.5 Mexico Zero Trust Security Market by End Use
- 10.1.6.4 Rest of North America Zero Trust Security Market
- 10.1.6.4.1 Rest of North America Zero Trust Security Market by Authentication
- 10.1.6.4.2 Rest of North America Zero Trust Security Market by Deployment
- 10.1.6.4.3 Rest of North America Zero Trust Security Market by Enterprise Size
- 10.1.6.4.4 Rest of North America Zero Trust Security Market by Type
- 10.1.6.4.5 Rest of North America Zero Trust Security Market by End Use
- 10.1.6.1 US Zero Trust Security Market
- 10.1.1 North America Zero Trust Security Market by Authentication
- 10.2 Europe Zero Trust Security Market
- 10.2.1 Europe Zero Trust Security Market by Authentication
- 10.2.1.1 Europe Single-factor Market by Country
- 10.2.1.2 Europe Multi-factor Market by Country
- 10.2.2 Europe Zero Trust Security Market by Deployment
- 10.2.2.1 Europe Cloud Market by Country
- 10.2.2.2 Europe On-Premises Market by Country
- 10.2.3 Europe Zero Trust Security Market by Enterprise Size
- 10.2.3.1 Europe Large Enterprises Market by Country
- 10.2.3.2 Europe SMEs Market by Country
- 10.2.4 Europe Zero Trust Security Market by Type
- 10.2.4.1 Europe Network Security Market by Country
- 10.2.4.2 Europe Data Security Market by Country
- 10.2.4.3 Europe Endpoint Security Market by Country
- 10.2.4.4 Europe On-premises Security Market by Country
- 10.2.4.5 Europe Other Type Market by Country
- 10.2.5 Europe Zero Trust Security Market by End Use
- 10.2.5.1 Europe BFSI Market by Country
- 10.2.5.2 Europe IT & Telecom Market by Country
- 10.2.5.3 Europe Retail Market by Country
- 10.2.5.4 Europe Healthcare Market by Country
- 10.2.5.5 Europe Other End Use Market by Country
- 10.2.6 Europe Zero Trust Security Market by Country
- 10.2.6.1 Germany Zero Trust Security Market
- 10.2.6.1.1 Germany Zero Trust Security Market by Authentication
- 10.2.6.1.2 Germany Zero Trust Security Market by Deployment
- 10.2.6.1.3 Germany Zero Trust Security Market by Enterprise Size
- 10.2.6.1.4 Germany Zero Trust Security Market by Type
- 10.2.6.1.5 Germany Zero Trust Security Market by End Use
- 10.2.6.2 UK Zero Trust Security Market
- 10.2.6.2.1 UK Zero Trust Security Market by Authentication
- 10.2.6.2.2 UK Zero Trust Security Market by Deployment
- 10.2.6.2.3 UK Zero Trust Security Market by Enterprise Size
- 10.2.6.2.4 UK Zero Trust Security Market by Type
- 10.2.6.2.5 UK Zero Trust Security Market by End Use
- 10.2.6.3 France Zero Trust Security Market
- 10.2.6.3.1 France Zero Trust Security Market by Authentication
- 10.2.6.3.2 France Zero Trust Security Market by Deployment
- 10.2.6.3.3 France Zero Trust Security Market by Enterprise Size
- 10.2.6.3.4 France Zero Trust Security Market by Type
- 10.2.6.3.5 France Zero Trust Security Market by End Use
- 10.2.6.4 Russia Zero Trust Security Market
- 10.2.6.4.1 Russia Zero Trust Security Market by Authentication
- 10.2.6.4.2 Russia Zero Trust Security Market by Deployment
- 10.2.6.4.3 Russia Zero Trust Security Market by Enterprise Size
- 10.2.6.4.4 Russia Zero Trust Security Market by Type
- 10.2.6.4.5 Russia Zero Trust Security Market by End Use
- 10.2.6.5 Spain Zero Trust Security Market
- 10.2.6.5.1 Spain Zero Trust Security Market by Authentication
- 10.2.6.5.2 Spain Zero Trust Security Market by Deployment
- 10.2.6.5.3 Spain Zero Trust Security Market by Enterprise Size
- 10.2.6.5.4 Spain Zero Trust Security Market by Type
- 10.2.6.5.5 Spain Zero Trust Security Market by End Use
- 10.2.6.6 Italy Zero Trust Security Market
- 10.2.6.6.1 Italy Zero Trust Security Market by Authentication
- 10.2.6.6.2 Italy Zero Trust Security Market by Deployment
- 10.2.6.6.3 Italy Zero Trust Security Market by Enterprise Size
- 10.2.6.6.4 Italy Zero Trust Security Market by Type
- 10.2.6.6.5 Italy Zero Trust Security Market by End Use
- 10.2.6.7 Rest of Europe Zero Trust Security Market
- 10.2.6.7.1 Rest of Europe Zero Trust Security Market by Authentication
- 10.2.6.7.2 Rest of Europe Zero Trust Security Market by Deployment
- 10.2.6.7.3 Rest of Europe Zero Trust Security Market by Enterprise Size
- 10.2.6.7.4 Rest of Europe Zero Trust Security Market by Type
- 10.2.6.7.5 Rest of Europe Zero Trust Security Market by End Use
- 10.2.6.1 Germany Zero Trust Security Market
- 10.2.1 Europe Zero Trust Security Market by Authentication
- 10.3 Asia Pacific Zero Trust Security Market
- 10.3.1 Asia Pacific Zero Trust Security Market by Authentication
- 10.3.1.1 Asia Pacific Single-factor Market by Country
- 10.3.1.2 Asia Pacific Multi-factor Market by Country
- 10.3.2 Asia Pacific Zero Trust Security Market by Deployment
- 10.3.2.1 Asia Pacific Cloud Market by Country
- 10.3.2.2 Asia Pacific On-Premises Market by Country
- 10.3.3 Asia Pacific Zero Trust Security Market by Enterprise Size
- 10.3.3.1 Asia Pacific Large Enterprises Market by Country
- 10.3.3.2 Asia Pacific SMEs Market by Country
- 10.3.4 Asia Pacific Zero Trust Security Market by Type
- 10.3.4.1 Asia Pacific Network Security Market by Country
- 10.3.4.2 Asia Pacific Data Security Market by Country
- 10.3.4.3 Asia Pacific Endpoint Security Market by Country
- 10.3.4.4 Asia Pacific On-premises Security Market by Country
- 10.3.4.5 Asia Pacific Other Type Market by Country
- 10.3.5 Asia Pacific Zero Trust Security Market by End Use
- 10.3.5.1 Asia Pacific BFSI Market by Country
- 10.3.5.2 Asia Pacific IT & Telecom Market by Country
- 10.3.5.3 Asia Pacific Retail Market by Country
- 10.3.5.4 Asia Pacific Healthcare Market by Country
- 10.3.5.5 Asia Pacific Other End Use Market by Country
- 10.3.6 Asia Pacific Zero Trust Security Market by Country
- 10.3.6.1 China Zero Trust Security Market
- 10.3.6.1.1 China Zero Trust Security Market by Authentication
- 10.3.6.1.2 China Zero Trust Security Market by Deployment
- 10.3.6.1.3 China Zero Trust Security Market by Enterprise Size
- 10.3.6.1.4 China Zero Trust Security Market by Type
- 10.3.6.1.5 China Zero Trust Security Market by End Use
- 10.3.6.2 Japan Zero Trust Security Market
- 10.3.6.2.1 Japan Zero Trust Security Market by Authentication
- 10.3.6.2.2 Japan Zero Trust Security Market by Deployment
- 10.3.6.2.3 Japan Zero Trust Security Market by Enterprise Size
- 10.3.6.2.4 Japan Zero Trust Security Market by Type
- 10.3.6.2.5 Japan Zero Trust Security Market by End Use
- 10.3.6.3 India Zero Trust Security Market
- 10.3.6.3.1 India Zero Trust Security Market by Authentication
- 10.3.6.3.2 India Zero Trust Security Market by Deployment
- 10.3.6.3.3 India Zero Trust Security Market by Enterprise Size
- 10.3.6.3.4 India Zero Trust Security Market by Type
- 10.3.6.3.5 India Zero Trust Security Market by End Use
- 10.3.6.4 South Korea Zero Trust Security Market
- 10.3.6.4.1 South Korea Zero Trust Security Market by Authentication
- 10.3.6.4.2 South Korea Zero Trust Security Market by Deployment
- 10.3.6.4.3 South Korea Zero Trust Security Market by Enterprise Size
- 10.3.6.4.4 South Korea Zero Trust Security Market by Type
- 10.3.6.4.5 South Korea Zero Trust Security Market by End Use
- 10.3.6.5 Singapore Zero Trust Security Market
- 10.3.6.5.1 Singapore Zero Trust Security Market by Authentication
- 10.3.6.5.2 Singapore Zero Trust Security Market by Deployment
- 10.3.6.5.3 Singapore Zero Trust Security Market by Enterprise Size
- 10.3.6.5.4 Singapore Zero Trust Security Market by Type
- 10.3.6.5.5 Singapore Zero Trust Security Market by End Use
- 10.3.6.6 Malaysia Zero Trust Security Market
- 10.3.6.6.1 Malaysia Zero Trust Security Market by Authentication
- 10.3.6.6.2 Malaysia Zero Trust Security Market by Deployment
- 10.3.6.6.3 Malaysia Zero Trust Security Market by Enterprise Size
- 10.3.6.6.4 Malaysia Zero Trust Security Market by Type
- 10.3.6.6.5 Malaysia Zero Trust Security Market by End Use
- 10.3.6.7 Rest of Asia Pacific Zero Trust Security Market
- 10.3.6.7.1 Rest of Asia Pacific Zero Trust Security Market by Authentication
- 10.3.6.7.2 Rest of Asia Pacific Zero Trust Security Market by Deployment
- 10.3.6.7.3 Rest of Asia Pacific Zero Trust Security Market by Enterprise Size
- 10.3.6.7.4 Rest of Asia Pacific Zero Trust Security Market by Type
- 10.3.6.7.5 Rest of Asia Pacific Zero Trust Security Market by End Use
- 10.3.6.1 China Zero Trust Security Market
- 10.3.1 Asia Pacific Zero Trust Security Market by Authentication
- 10.4 LAMEA Zero Trust Security Market
- 10.4.1 LAMEA Zero Trust Security Market by Authentication
- 10.4.1.1 LAMEA Single-factor Market by Country
- 10.4.1.2 LAMEA Multi-factor Market by Country
- 10.4.2 LAMEA Zero Trust Security Market by Deployment
- 10.4.2.1 LAMEA Cloud Market by Country
- 10.4.2.2 LAMEA On-Premises Market by Country
- 10.4.3 LAMEA Zero Trust Security Market by Enterprise Size
- 10.4.3.1 LAMEA Large Enterprises Market by Country
- 10.4.3.2 LAMEA SMEs Market by Country
- 10.4.4 LAMEA Zero Trust Security Market by Type
- 10.4.4.1 LAMEA Network Security Market by Country
- 10.4.4.2 LAMEA Data Security Market by Country
- 10.4.4.3 LAMEA Endpoint Security Market by Country
- 10.4.4.4 LAMEA On-premises Security Market by Country
- 10.4.4.5 LAMEA Other Type Market by Country
- 10.4.5 LAMEA Zero Trust Security Market by End Use
- 10.4.5.1 LAMEA BFSI Market by Country
- 10.4.5.2 LAMEA IT & Telecom Market by Country
- 10.4.5.3 LAMEA Retail Market by Country
- 10.4.5.4 LAMEA Healthcare Market by Country
- 10.4.5.5 LAMEA Other End Use Market by Country
- 10.4.6 LAMEA Zero Trust Security Market by Country
- 10.4.6.1 Brazil Zero Trust Security Market
- 10.4.6.1.1 Brazil Zero Trust Security Market by Authentication
- 10.4.6.1.2 Brazil Zero Trust Security Market by Deployment
- 10.4.6.1.3 Brazil Zero Trust Security Market by Enterprise Size
- 10.4.6.1.4 Brazil Zero Trust Security Market by Type
- 10.4.6.1.5 Brazil Zero Trust Security Market by End Use
- 10.4.6.2 Argentina Zero Trust Security Market
- 10.4.6.2.1 Argentina Zero Trust Security Market by Authentication
- 10.4.6.2.2 Argentina Zero Trust Security Market by Deployment
- 10.4.6.2.3 Argentina Zero Trust Security Market by Enterprise Size
- 10.4.6.2.4 Argentina Zero Trust Security Market by Type
- 10.4.6.2.5 Argentina Zero Trust Security Market by End Use
- 10.4.6.3 UAE Zero Trust Security Market
- 10.4.6.3.1 UAE Zero Trust Security Market by Authentication
- 10.4.6.3.2 UAE Zero Trust Security Market by Deployment
- 10.4.6.3.3 UAE Zero Trust Security Market by Enterprise Size
- 10.4.6.3.4 UAE Zero Trust Security Market by Type
- 10.4.6.3.5 UAE Zero Trust Security Market by End Use
- 10.4.6.4 Saudi Arabia Zero Trust Security Market
- 10.4.6.4.1 Saudi Arabia Zero Trust Security Market by Authentication
- 10.4.6.4.2 Saudi Arabia Zero Trust Security Market by Deployment
- 10.4.6.4.3 Saudi Arabia Zero Trust Security Market by Enterprise Size
- 10.4.6.4.4 Saudi Arabia Zero Trust Security Market by Type
- 10.4.6.4.5 Saudi Arabia Zero Trust Security Market by End Use
- 10.4.6.5 South Africa Zero Trust Security Market
- 10.4.6.5.1 South Africa Zero Trust Security Market by Authentication
- 10.4.6.5.2 South Africa Zero Trust Security Market by Deployment
- 10.4.6.5.3 South Africa Zero Trust Security Market by Enterprise Size
- 10.4.6.5.4 South Africa Zero Trust Security Market by Type
- 10.4.6.5.5 South Africa Zero Trust Security Market by End Use
- 10.4.6.6 Nigeria Zero Trust Security Market
- 10.4.6.6.1 Nigeria Zero Trust Security Market by Authentication
- 10.4.6.6.2 Nigeria Zero Trust Security Market by Deployment
- 10.4.6.6.3 Nigeria Zero Trust Security Market by Enterprise Size
- 10.4.6.6.4 Nigeria Zero Trust Security Market by Type
- 10.4.6.6.5 Nigeria Zero Trust Security Market by End Use
- 10.4.6.7 Rest of LAMEA Zero Trust Security Market
- 10.4.6.7.1 Rest of LAMEA Zero Trust Security Market by Authentication
- 10.4.6.7.2 Rest of LAMEA Zero Trust Security Market by Deployment
- 10.4.6.7.3 Rest of LAMEA Zero Trust Security Market by Enterprise Size
- 10.4.6.7.4 Rest of LAMEA Zero Trust Security Market by Type
- 10.4.6.7.5 Rest of LAMEA Zero Trust Security Market by End Use
- 10.4.6.1 Brazil Zero Trust Security Market
- 10.4.1 LAMEA Zero Trust Security Market by Authentication
Chapter 11. Company Profiles
- 11.1 Broadcom, Inc.
- 11.1.1 Company Overview
- 11.1.2 Financial Analysis
- 11.1.3 Segmental and Regional Analysis
- 11.1.4 Research & Development Expense
- 11.1.5 Recent strategies and developments:
- 11.1.5.1 Acquisition and Mergers:
- 11.1.6 SWOT Analysis
- 11.2 Microsoft Corporation
- 11.2.1 Company Overview
- 11.2.2 Financial Analysis
- 11.2.3 Segmental and Regional Analysis
- 11.2.4 Research & Development Expenses
- 11.2.5 Recent strategies and developments:
- 11.2.5.1 Partnerships, Collaborations, and Agreements:
- 11.2.5.2 Product Launches and Product Expansions:
- 11.2.6 SWOT Analysis
- 11.3 Fortinet, Inc.
- 11.3.1 Company Overview
- 11.3.2 Financial Analysis
- 11.3.3 Regional Analysis
- 11.3.4 Research & Development Expenses
- 11.3.5 Recent strategies and developments:
- 11.3.5.1 Partnerships, Collaborations, and Agreements:
- 11.3.5.2 Acquisition and Mergers:
- 11.3.6 SWOT Analysis
- 11.4 Palo Alto Networks, Inc.
- 11.4.1 Company Overview
- 11.4.2 Financial Analysis
- 11.4.3 Regional Analysis
- 11.4.4 Research & Development Expense
- 11.4.5 Recent strategies and developments:
- 11.4.5.1 Partnerships, Collaborations, and Agreements:
- 11.4.5.2 Product Launches and Product Expansions:
- 11.4.6 SWOT Analysis
- 11.5 IBM Corporation
- 11.5.1 Company Overview
- 11.5.2 Financial Analysis
- 11.5.3 Regional & Segmental Analysis
- 11.5.4 Research & Development Expenses
- 11.5.5 Recent strategies and developments:
- 11.5.5.1 Partnerships, Collaborations, and Agreements:
- 11.5.5.2 Acquisition and Mergers:
- 11.5.6 SWOT Analysis
- 11.6 Cisco Systems, Inc.
- 11.6.1 Company Overview
- 11.6.2 Financial Analysis
- 11.6.3 Regional Analysis
- 11.6.4 Research & Development Expense
- 11.6.5 Recent strategies and developments:
- 11.6.5.1 Partnerships, Collaborations, and Agreements:
- 11.6.6 SWOT Analysis
- 11.7 Cloudflare, Inc.
- 11.7.1 Company Overview
- 11.7.2 Financial Analysis
- 11.7.3 Regional Analysis
- 11.7.4 Research & Development Expense
- 11.7.5 SWOT Analysis
- 11.8 Check Point Software Technologies Ltd.
- 11.8.1 Company Overview
- 11.8.2 Financial Analysis
- 11.8.3 Regional Analysis
- 11.8.4 Research & Development Expenses
- 11.8.5 Recent strategies and developments:
- 11.8.5.1 Partnerships, Collaborations, and Agreements:
- 11.8.6 SWOT Analysis
- 11.9 Crowdstrike Holdings, Inc.
- 11.9.1 Company Overview
- 11.9.2 Financial Analysis
- 11.9.3 Regional Analysis
- 11.9.4 Research & Development Expenses
- 11.9.5 Recent strategies and developments:
- 11.9.5.1 Partnerships, Collaborations, and Agreements:
- 11.9.6 SWOT Analysis
- 11.10. Forcepoint LLC (Francisco Partners)
- 11.10.1 Company Overview
- 11.10.2 SWOT Analysis