|
|
市場調査レポート
商品コード
1712527
防衛サイバーセキュリティの世界市場 (2025-2032年)Global Defense Cybersecurity Market - 2025-2032 |
||||||
カスタマイズ可能
適宜更新あり
|
|||||||
| 防衛サイバーセキュリティの世界市場 (2025-2032年) |
|
出版日: 2025年04月22日
発行: DataM Intelligence
ページ情報: 英文 180 Pages
納期: 即日から翌営業日
|
- 全表示
- 概要
- 目次
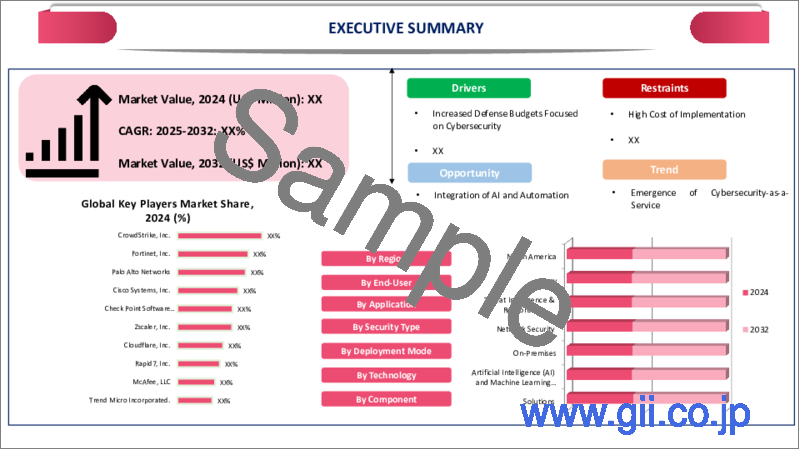
世界の防衛サイバーセキュリティの市場規模は、2024年の372億3,000万米ドルから、予測期間中はCAGR 7.6%で推移し、2032年には668億9,000万米ドルに達すると予測されています。
国家防衛インフラ、軍事ネットワーク、重要な通信システムを標的とするサイバー脅威の頻度と高度化の進展により、世界の防衛サイバーセキュリティ市場は著しい成長を遂げています。各国政府や防衛機関は、機密データの保護、安全な通信の確保、作戦遂行能力の維持を目的に、サイバーセキュリティの優先順位を一層高めています。
サイバースパイ活動、国家支援型の攻撃、ランサムウェアによる防衛システムへの攻撃が増加する中、AIによる脅威検知、ゼロトラストアーキテクチャ、ブロックチェーンベースのセキュリティプロトコルなどの先端サイバーセキュリティ技術への投資が加速しています。業界の主要企業は、脅威インテリジェンスの強化と次世代防衛サイバーセキュリティソリューションの開発を目指し、戦略的提携、買収、研究開発活動に注力しています。
市場動向
IoTの拡大により、サイバー犯罪の機会も増えています。IoTには、ウェアラブル型フィットネストラッカー、スマート冷蔵庫、スマートウォッチ、Amazon EchoやGoogle Homeといった音声アシスタントなどがあります。2026年までに、世界中で640億台のIoTデバイスが設置されると推定されています。この増加傾向は、リモートワークの普及が後押ししています。
フィッシングなどのソーシャルエンジニアリング攻撃は新しい脅威ではありませんが、広範なリモートワークの普及に伴い、より深刻な問題となっています。攻撃者は、自宅から雇用主のネットワークに接続する個人を標的とする傾向があり、これらの個人は比較的攻撃しやすい対象とみなされています。従業員を狙った従来型のフィッシング攻撃に加え、組織の経営幹部を狙う「ホエーリング攻撃」の増加も確認されています。
ダイナミクス
サイバーセキュリティに焦点を当てた防衛予算の増加
各国は防衛支出を大幅に増加させており、その中でもサイバーセキュリティ関連施策への配分が拡大しています。たとえば、オーストラリアでは2025年に向けて防衛費が増加しており、政府はGDPのより大きな割合を軍事支出に充てる方針を打ち出しています。アルバニージー政権はすでに、2025年の防衛予算から10億豪ドルを前倒しで確保しており、特に米国をはじめとする同盟国からの圧力も、防衛支出拡大への動きを加速させています。
さらに、米国の2025会計年度国防権限法 (NDAA) では、約300億米ドルがサイバーセキュリティに充てられ、総額8,952億米ドルに上る米国の軍事予算の中で極めて重要な焦点となっています。加えて、Cybersecurity Venturesは、今後5年間で世界のサイバー犯罪による損失額が年平均15%のペースで増加し、2025年には年間10兆5,000億米ドルに達すると予測しており、これは2015年の3兆米ドルから大幅な増加となります。こうした要因が、防衛サイバーセキュリティ市場の成長を後押ししています。
当レポートでは、世界の防衛サイバーセキュリティの市場を調査し、市場概要、市場成長への各種影響因子の分析、各種区分・地域/主要国別の詳細分析、主要企業のプロファイルなどをまとめています。
目次
第1章 調査手法・調査範囲
第2章 定義と概要
第3章 エグゼクティブサマリー
第4章 市場力学
- 影響要因
- 促進要因
- 抑制要因
- 機会
- 影響分析
第5章 業界分析
- ポーターのファイブフォース分析
- サプライチェーン分析
- 価格分析
- 規制およびコンプライアンス分析
- 持続可能性分析
- DMIオピニオン
第6章 コンポーネント別
- ソリューション
- 脅威インテリジェンス
- アイデンティティとアクセス管理 (IAM)
- データ損失防止 (DLP)
- セキュリティ情報およびイベント管理 (SIEM)
- その他
- サービス
- マネージドセキュリティサービス
- コンサルティングとトレーニング
- 統合と展開
- その他
第7章 技術別
- サイバーセキュリティにおけるAIと機械学習 (ML)
- サイバー防御のためのブロックチェーン
- 高度な持続的脅威 (APT) ソリューション
- 次世代ファイアウォール
- ゼロトラストセキュリティ
- 量子暗号 (新興)
- その他
第8章 展開モード別
- オンプレミス
- クラウドベース
第9章 セキュリティタイプ別
- ネットワークセキュリティ
- エンドポイントセキュリティ
- アプリケーションセキュリティ
- クラウドセキュリティ
- データセキュリティ
- その他
第10章 用途別
- 脅威インテリジェンス・対応
- インフラセキュリティ
- データ保護
- ID・アクセス管理
- リスク・コンプライアンス管理
- その他
第11章 地域別
- 北米
- 米国
- カナダ
- メキシコ
- 欧州
- ドイツ
- 英国
- フランス
- イタリア
- スペイン
- その他
- 南米
- ブラジル
- アルゼンチン
- その他
- アジア太平洋
- 中国
- インド
- 日本
- オーストラリア
- その他
- 中東・アフリカ
第12章 企業プロファイル
- Raytheon Technologies Corporation
- Lockheed Martin Corporation
- BAE Systems plc
- Leonardo SpA
- Airbus SAS
- General Dynamics Corporation
- Palantir Technologies Inc.
- Northrop Grumman Corporation
- L3Harris Technologies Inc.
- Thales Group
第13章 付録
Global defense cybersecurity market reached US$ 37.23 billion in 2024 and is expected to reach US$ 66.89 billion by 2032, growing with a CAGR of 7.6% during the forecast period 2025-2032.
The global defense cybersecurity market is experiencing significant growth due to the escalating frequency and sophistication of cyber threats targeting national defense infrastructure, military networks, and critical communication systems. Governments and defense agencies worldwide are increasingly prioritizing cybersecurity to safeguard sensitive data, ensure secure communications, and maintain operational readiness.
The rise in cyber espionage, state-sponsored attacks, and ransomware targeting defense systems has accelerated investments in advanced cybersecurity technologies such as AI-powered threat detection, zero-trust architectures, and blockchain-based security protocols. Key players in the industry are focusing on strategic collaborations, acquisitions, and R&D initiatives to enhance threat intelligence and develop next-generation defense cybersecurity solutions.
Market Trends
The expanding Internet of Things (IoT) creates more opportunities for cybercrime. The Internet of Things refers to physical devices other than computers, phones, and servers, which connect to the internet and share data. Examples of IoT devices include wearable fitness trackers, smart refrigerators, smartwatches, and voice assistants like Amazon Echo and Google Home. It is estimated that by 2026, there will be 64 billion IoT devices installed around the world. The trend toward remote working is helping to drive this increase.
Social engineering attacks like phishing are not new threats but have become more troubling amid the widespread remote workforce. Attackers target individuals connecting to their employer's network from home because they make easier targets. As well as traditional phishing attacks on employees, there has also been an uptick in whaling attacks targeting executive organizational leadership.
Dynamics
Increased Defense Budgets Focused on Cybersecurity
Countries are significantly increasing their defense spending, with a larger portion allocated toward cybersecurity initiatives. For instance, in 2025, Defence spending in Australia is growing, with the government committing an increasing proportion of GDP to military expenditure. The Albanese government has already brought forward A$1 billion from the 2025 defence budget, while pressure from foreign allies, notably the US, is driving up calls for greater spending.
Additionally, the National Defense Authorization Act (NDAA) for the US military fiscal year 2025 dedicates approximately US$30 billion to cybersecurity, marking it as a crucial focus in the broader US$895.2 billion military budget. Moreover, Cybersecurity Ventures expects global cybercrime costs to grow by 15 percent per year over the next five years, reaching US$10.5 trillion annually by 2025, up from US$3 trillion in 2015. Thus, above factors helps to boost the market growth.
High Implementation and Maintenance Costs
High Implementation and Maintenance Costs significantly restrain the growth of the global defense cybersecurity market by creating financial and logistical barriers, especially for developing nations and smaller defense organizations. Establishing a robust cybersecurity infrastructure for defense requires substantial investment in advanced technologies such as secure communication networks, quantum-safe encryption, and multi-layered firewalls-all of which come at a premium cost.
The high-cost factor not only limits the initial adoption of cybersecurity systems but also restricts scalability, continuous improvement, and widespread deployment, particularly in remote bases or across vast military networks.
Segment Analysis
The global defense cybersecurity market is segmented based on component, technology, deployment mode, security type, application and region.
Strategic Preference for On-Premises Deployment Strengthens Defense Cybersecurity Market Growth
The On-Premises segment drives growth in the global defense cybersecurity market primarily due to the defense sector's high sensitivity to data privacy, control, and regulatory compliance. Defense organizations across the globe prefer on-premises deployment because it allows them to retain full control over their cybersecurity infrastructure and sensitive data, minimizing the risk of external breaches or unauthorized access.
For instance, the US Department of Defense (DoD) relies heavily on on-premises systems for classified networks such as SIPRNet and JWICS, ensuring that critical intelligence and communication channels remain isolated from public or cloud-based environments. Thus, the combination of enhanced control, compliance, and reduced external exposure is making on-premises deployment a preferred and growing segment in the defense cybersecurity space.
Geographical Penetration
North America Leads Defense Cybersecurity Market with Superior Spending and Technological Edge
North America dominates the global defense cybersecurity market due to its unparalleled defense expenditure, technological superiority, and strong focus on cybersecurity preparedness. The US, which accounts for the largest share of global military spending, allocates a significant portion of its defense budget to cybersecurity initiatives through departments such as the Department of Defense (DoD), Cyber Command (USCYBERCOM), and the National Security Agency (NSA).
These agencies are at the forefront of developing and deploying advanced cyber defense technologies, including AI-based threat detection, zero-trust architecture, and quantum-resistant encryption. For example, the US DoD's annual cybersecurity budget exceeds US$10 billion, reflecting its strategic emphasis on digital defense infrastructure. This combination of financial muscle, policy support, and technological capability positions North America as the most advanced and influential region in the defense cybersecurity landscape.
Sustainability Analysis
Sustainability in the global defense cybersecurity market hinges on long-term investment, technological innovation, workforce development, and adaptive policy frameworks. As cyber threats become more complex and persistent, defense agencies are recognizing cybersecurity not as a one-time investment but as a continuous strategic imperative.
Sustainable growth in this market is supported by the integration of energy-efficient data centers, green IT infrastructure, and AI-driven systems that optimize resource utilization while enhancing threat detection capabilities. Governments are also emphasizing capacity-building and education programs to address the talent gap, ensuring a steady pipeline of skilled cyber professionals.
Competitive Landscape
The major global players in the market include Raytheon Technologies Corporation, Lockheed Martin Corporation, BAE Systems plc, Leonardo S.p.A., Airbus S.A.S., General Dynamics Corporation, Palantir Technologies Inc., Northrop Grumman Corporation, L3Harris Technologies Inc., Thales Group and among others.
Key Developments
- In 2024, Google's AI Cyber Defense Initiative, launched at the Munich Security Conference, signals a belief that the company's experience in deploying AI can help to reverse what it calls the defender's dilemma.
- In 2025, Blackwire Labs, a leader in trusted AI-driven cybersecurity solutions, announces the launch of its new industry-specific Advisory Solutions designed to provide tailored cybersecurity guidance to healthcare, state and local governments, the defense industrial base, and nonprofit organizations.
- In 2024, LTIMindtree, a global technology consulting and digital solutions company, announced the launch of its Cyber Defense Resiliency Center (CDRC) in India.
Why Choose DataM?
- Data-Driven Insights: Dive into detailed analyses with granular insights such as pricing, market shares and value chain evaluations, enriched by interviews with industry leaders and disruptors.
- Post-Purchase Support and Expert Analyst Consultations: As a valued client, gain direct access to our expert analysts for personalized advice and strategic guidance, tailored to your specific needs and challenges.
- White Papers and Case Studies: Benefit quarterly from our in-depth studies related to your purchased titles, tailored to refine your operational and marketing strategies for maximum impact.
- Annual Updates on Purchased Reports: As an existing customer, enjoy the privilege of annual updates to your reports, ensuring you stay abreast of the latest market insights and technological advancements. Terms and conditions apply.
- Specialized Focus on Emerging Markets: DataM differentiates itself by delivering in-depth, specialized insights specifically for emerging markets, rather than Security Type generalized geographic overviews. This approach equips our clients with a nuanced understanding and actionable intelligence that are essential for navigating and succeeding in high-growth regions.
- Value of DataM Reports: Our reports offer specialized insights tailored to the latest trends and specific business inquiries. This personalized approach provides a deeper, strategic perspective, ensuring you receive the precise information necessary to make informed decisions. These insights complement and go beyond what is typically available in generic databases.
Target Audience 2024
- Manufacturers/ Buyers
- Industry Investors/Investment Bankers
- Research Professionals
- Emerging Companies
Table of Contents
1. Methodology and Scope
- 1.1. Research Methodology
- 1.2. Research Objective and Scope of the Report
2. Definition and Overview
3. Executive Summary
- 3.1. Snippet by Component
- 3.2. Snippet by Technology
- 3.3. Snippet by Deployment Mode
- 3.4. Snippet by Security Type
- 3.5. Snippet by Application
- 3.6. Snippet by Region
4. Dynamics
- 4.1. Impacting Factors
- 4.1.1. Drivers
- 4.1.1.1. Increased Defense Budgets Focused on Cybersecurity
- 4.1.2. Restraints
- 4.1.2.1. High Implementation and Maintenance Costs
- 4.1.3. Opportunity
- 4.1.4. Impact Analysis
- 4.1.1. Drivers
5. Industry Analysis
- 5.1. Porter's Five Force Analysis
- 5.2. Supply Chain Analysis
- 5.3. Pricing Analysis
- 5.4. Regulatory and Compliance Analysis
- 5.5. Sustainability Analysis
- 5.6. DMI Opinion
6. By Component
- 6.1. Introduction
- 6.1.1. Market Size Analysis and Y-o-Y Growth Analysis (%), By Component
- 6.1.2. Market Attractiveness Index, By Component
- 6.2. Solutions *
- 6.2.1. Introduction
- 6.2.2. Market Size Analysis and Y-o-Y Growth Analysis (%)
- 6.2.3. Threat Intelligence
- 6.2.4. Identity & Access Management (IAM)
- 6.2.5. Data Loss Prevention (DLP
- 6.2.6. Security Information and Event Management (SIEM)
- 6.2.7. Others
- 6.3. Services
- 6.3.1. Managed Security Services
- 6.3.2. Consulting & Training
- 6.3.3. Integration & Deployment
- 6.3.4. Others
7. By Technology
- 7.1. Introduction
- 7.1.1. Market Size Analysis and Y-o-Y Growth Analysis (%), By Technology
- 7.1.2. Market Attractiveness Index, By Technology
- 7.2. Artificial Intelligence (AI) and Machine Learning (ML) in Cybersecurity *
- 7.2.1. Introduction
- 7.2.2. Market Size Analysis and Y-o-Y Growth Analysis (%)
- 7.3. Blockchain for Cyber Defense
- 7.4. Advanced Persistent Threats (APT) Solutions
- 7.5. Next-Gen Firewalls
- 7.6. Zero Trust Security
- 7.7. Quantum Cryptography (Emerging)
- 7.8. Others
8. By Deployment Mode
- 8.1. Introduction
- 8.1.1. Market Size Analysis and Y-o-Y Growth Analysis (%), By Deployment Mode
- 8.1.2. Market Attractiveness Index, By Deployment Mode
- 8.2. On-Premises *
- 8.2.1. Introduction
- 8.2.2. Market Size Analysis and Y-o-Y Growth Analysis (%)
- 8.3. Cloud-Based
9. By Security Type
- 9.1. Introduction
- 9.1.1. Market Size Analysis and Y-o-Y Growth Analysis (%), By Security Type
- 9.1.2. Market Attractiveness Index, By Security Type
- 9.2. Network Security *
- 9.2.1. Introduction
- 9.2.2. Market Size Analysis and Y-o-Y Growth Analysis (%)
- 9.3. Endpoint Security
- 9.4. Application Security
- 9.5. Cloud Security
- 9.6. Data Security
- 9.7. Others
10. By Application
- 10.1. Introduction
- 10.1.1. Market Size Analysis and Y-o-Y Growth Analysis (%), By Application
- 10.1.2. Market Attractiveness Index, By Application
- 10.2. Threat Intelligence & Response *
- 10.2.1. Introduction
- 10.2.2. Market Size Analysis and Y-o-Y Growth Analysis (%)
- 10.3. Infrastructure Security
- 10.4. Data Protection
- 10.5. Identity and Access Management
- 10.6. Risk & Compliance Management
- 10.7. Others
11. By Region
- 11.1. Introduction
- 11.1.1. Market Size Analysis and Y-o-Y Growth Analysis (%), By Region
- 11.1.2. Market Attractiveness Index, By Region
- 11.2. North America
- 11.2.1. Introduction
- 11.2.2. Key Region-Specific Dynamics
- 11.2.3. Market Size Analysis and Y-o-Y Growth Analysis (%), By Component
- 11.2.4. Market Size Analysis and Y-o-Y Growth Analysis (%), By Technology
- 11.2.5. Market Size Analysis and Y-o-Y Growth Analysis (%), By Deployment Mode
- 11.2.6. Market Size Analysis and Y-o-Y Growth Analysis (%), By Security Type
- 11.2.7. Market Size Analysis and Y-o-Y Growth Analysis (%), By Application
- 11.2.8. Market Size Analysis and Y-o-Y Growth Analysis (%), By Country
- 11.2.8.1. US
- 11.2.8.2. Canada
- 11.2.8.3. Mexico
- 11.3. Europe
- 11.3.1. Introduction
- 11.3.2. Key Region-Specific Dynamics
- 11.3.3. Market Size Analysis and Y-o-Y Growth Analysis (%), By Component
- 11.3.4. Market Size Analysis and Y-o-Y Growth Analysis (%), By Technology
- 11.3.5. Market Size Analysis and Y-o-Y Growth Analysis (%), By Deployment Mode
- 11.3.6. Market Size Analysis and Y-o-Y Growth Analysis (%), By Security Type
- 11.3.7. Market Size Analysis and Y-o-Y Growth Analysis (%), By Application
- 11.3.8. Market Size Analysis and Y-o-Y Growth Analysis (%), By Country
- 11.3.8.1. Germany
- 11.3.8.2. UK
- 11.3.8.3. France
- 11.3.8.4. Italy
- 11.3.8.5. Spain
- 11.3.8.6. Rest of Europe
- 11.4. South America
- 11.4.1. Introduction
- 11.4.2. Key Region-Specific Dynamics
- 11.4.3. Market Size Analysis and Y-o-Y Growth Analysis (%), By Component
- 11.4.4. Market Size Analysis and Y-o-Y Growth Analysis (%), By Technology
- 11.4.5. Market Size Analysis and Y-o-Y Growth Analysis (%), By Deployment Mode
- 11.4.6. Market Size Analysis and Y-o-Y Growth Analysis (%), By Security Type
- 11.4.7. Market Size Analysis and Y-o-Y Growth Analysis (%), By Application
- 11.4.8. Market Size Analysis and Y-o-Y Growth Analysis (%), By Country
- 11.4.8.1. Brazil
- 11.4.8.2. Argentina
- 11.4.8.3. Rest of South America
- 11.5. Asia-Pacific
- 11.5.1. Introduction
- 11.5.2. Key Region-Specific Dynamics
- 11.5.3. Market Size Analysis and Y-o-Y Growth Analysis (%), By Component
- 11.5.4. Market Size Analysis and Y-o-Y Growth Analysis (%), By Technology
- 11.5.5. Market Size Analysis and Y-o-Y Growth Analysis (%), By Deployment Mode
- 11.5.6. Market Size Analysis and Y-o-Y Growth Analysis (%), By Security Type
- 11.5.7. Market Size Analysis and Y-o-Y Growth Analysis (%), By Application
- 11.5.8. Market Size Analysis and Y-o-Y Growth Analysis (%), By Country
- 11.5.8.1. China
- 11.5.8.2. India
- 11.5.8.3. Japan
- 11.5.8.4. Australia
- 11.5.8.5. Rest of Asia-Pacific
- 11.6. Middle East and Africa
- 11.6.1. Introduction
- 11.6.2. Key Region-Specific Dynamics
- 11.6.3. Market Size Analysis and Y-o-Y Growth Analysis (%), By Component
- 11.6.4. Market Size Analysis and Y-o-Y Growth Analysis (%), By Technology
- 11.6.5. Market Size Analysis and Y-o-Y Growth Analysis (%), By Deployment Mode
- 11.6.6. Market Size Analysis and Y-o-Y Growth Analysis (%), By Security Type
- 11.6.7. Market Size Analysis and Y-o-Y Growth Analysis (%), By Application
12. Company Profiles
- 12.1. Raytheon Technologies Corporation *
- 12.1.1. Company Overview
- 12.1.2. Product Portfolio and Description
- 12.1.3. Financial Overview
- 12.1.4. Key Developments
- 12.2. Lockheed Martin Corporation
- 12.3. BAE Systems plc
- 12.4. Leonardo S.p.A.
- 12.5. Airbus S.A.S.
- 12.6. General Dynamics Corporation
- 12.7. Palantir Technologies Inc.
- 12.8. Northrop Grumman Corporation
- 12.9. L3Harris Technologies Inc.
- 12.10. Thales Group
LIST NOT EXHAUSTIVE
13. Appendix
- 13.1. About Us and Services
- 13.2. Contact Us