
|
市場調査レポート
商品コード
1640350
エネルギー分野のクラウドセキュリティ-市場シェア分析、産業動向・統計、成長予測(2025年~2030年)Cloud Security in Energy Sector - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
カスタマイズ可能
適宜更新あり
|
|||||||
| エネルギー分野のクラウドセキュリティ-市場シェア分析、産業動向・統計、成長予測(2025年~2030年) |
|
出版日: 2025年01月05日
発行: Mordor Intelligence
ページ情報: 英文 120 Pages
納期: 2~3営業日
|
全表示
- 概要
- 目次
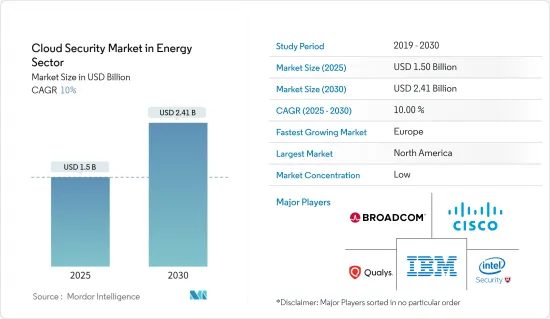
エネルギー分野のクラウドセキュリティ市場は、予測期間(2025~2030年)のCAGR10%で、2025年の15億米ドルから2030年には24億1,000万米ドルに成長すると予測されます。
各国が二酸化炭素排出量の削減と再生可能エネルギーへの転換を望んでいることを考えると、エネルギー分野は大きな変革の真っ只中にあります。温室効果ガス排出削減の必要性、再生可能エネルギーのコスト低下、スマートグリッドなどの新技術の採用により、データの保存、管理、分析の需要が高まっています。エネルギー企業は、こうしたデータの収集と活用にクラウド技術を利用することで大きな恩恵を受けています。電力会社は、この重要なデータのセキュリティを確保するため、さまざまなクラウドコンピューティング企業と協力しています。
主要ハイライト
- Gartner,によると、2024年までにクラウドコンピューティングは、システムインフラ、インフラソフトウェア、アプリケーションソフトウェア、ビジネスプロセスアウトソーシングに対するIT支出の45%以上を占めるようになるといいます。Deloitteの最新レポートによると、エネルギー公益企業の83%がクラウドサービスを利用しているか、今後2年以内に利用したいと考えています。俊敏性と柔軟性の向上、設備投資(CapEx)コストの削減、業務効率の向上など、多くの変数がエネルギー公益事業部門でのクラウド利用を後押ししています。
- システムに社外からアクセスする場合、セキュリティが最も重要になります。レガシー機器は、エネルギー部門の主要課題の1つです。運用技術(OT)ネットワークは、一般的に15年以上前の機器を使って構築されているため、より接続性が高くなっています。IT(情報技術)とOT環境の融合により、セキュリティの問題が生じています。
- COVID-19の大流行は、クラウドストレージが革命的な技術として最も重要な時期であり、クラウドセキュリティサービスの需要をさらに押し上げました。発電所では、遠隔地から安全にシステムにアクセスすることが不可欠となりました。ゼロ・トラスト・アーキテクチャのようなデジタルソリューションに切り替えた企業もあり、セキュリティチームは、さまざまな場所からのフィードをリアルタイムで1つのダッシュボードにまとめることで、より詳細なコンテキスト情報を得ることができるようになりました。
- 2022年4月-Bharat Petroleum Corporation(BPCL)はMicrosoftと契約を締結し、BPCLにインテリジェンスを提供することで、業務を刷新し、よりスマートなサプライチェーンを構築し、顧客エンゲージメントを高めています。Microsoftはこの7年間の契約で、BPCLにネットワークとセキュリティサービスを記載しています。
エネルギー分野のクラウドセキュリティ市場動向
サイバー攻撃の増加がエネルギー分野におけるクラウドセキュリティの必要性を促進
- エネルギー分野の企業は、何千もの異なるサプライヤーを管理し、多くの場所で事業を展開し、他の大陸から製品を調達しなければならないことが多いです。そのため、ハッカーやサイバーテロリストの格好の標的となっています。適切なレベルのセキュリティを確保するために、企業は製品のライフサイクル全体を通じて製品の脆弱性をモニタリングし、最新の基準や規制を遵守しなければならないです。
- サイバー攻撃は、莫大なコストをかけ、電力の途絶や顧客機密データの流出につながる可能性があります。これは、会社の事業運営やそのサービスに依存する人々に大きな影響を与える可能性があります。サイバーセキュリティ会社を雇うことで、エネルギー会社は機密データを暗号化し、悪質な攻撃から守る方法を従業員に教えることができます。
- 2022年2月、ドイツのOiltanking、ベルギーのSEA-Invest、オランダのEvosで発生した混乱は、世界中の石油貯蔵・輸送ターミナル数十カ所に影響を与えました。このようなサイバー攻撃により、各社は限られた操業能力での操業を余儀なくされ、サプライチェーンの問題を引き起こしています。
- さらに、2022年4月には、Oil Indiaがサイバー攻撃を受け、アッサム州での操業に支障をきたしました。サイバー攻撃はOil India Ltd.の地質・リザーバー部門のワークステーションのひとつで発生しました。サイバー攻撃者は感染したPCからのメモを通じて身代金として750万米ドルを要求しました。しかし、掘削と生産作業には影響がなかった。(参照元:https://www.mordorintelligence.com/industry-reports/cloud-security-in-energy-sector-industry)
- さらに2023年11月、ハイブリッドクラウドストレージのリーディングソリューションの1つであるNasuniは、エネルギー産業向けデジタルソリューションの世界のリーダーの1つであるCegalとの戦略的パートナーシップを発表しました。エネルギー組織は、クラウド変革の加速、ファイルデータアーキテクチャの近代化、サイバー耐性の強化のためにNasuniへの依存を高めているNasuniとCegalは、あらゆる場所からデータを大規模に管理・保護するために必要な技術インフラと専門知識を提供することで、組織がクラウド変革を加速するのを支援しています。
欧州が最も高い成長を遂げる見込み
- 公共機関や欧州政府は、オンラインサービスの需要増に対応するため、組織を適応させる必要があった。このため、超複雑な世界経済で競合を維持するために不可欠なインフラとサービスを提供するクラウドコンピューティング技術に対する需要が生まれました。
- 欧州のエネルギーシステムは、気候問題に対処し、EUのロシア産化石燃料への依存度を低減するために、デジタル化が極めて重要な役割を果たす重要な転換期を迎える必要があります。こうした開発を支援するため、EUはスマートエネルギー専門家グループを結成し、エネルギーに関する欧州共通のデータ空間の開発と展開を支援しています。
- EUの全世帯と中小企業の51%がスマート電力メーターを装備しており、セキュリティ、プライバシー、消費者保護などの問題として、エネルギーのデジタル化を導くためのさまざまな施策が導入されています。欧州委員会は、Network and Information Security Group(NIS)と協議の上、協調的なリスク評価の対象となりうる特定のICTサービス、システム、製品を優先的に特定します。
- 英国は2022年に最も暖かい夏を経験し、異常気象のため、ロンドンにあるOracleとGoogleクラウドのデータセンターで一時的な障害が発生しました。水不足とエネルギー不安がデータセンター運営者を不安にさせ、クラウドコンピューティングの運用に影響を与えました。こうした不確実性を克服するため、ECは電力網への6,200億米ドルの投資を計画しており、その中には1,804億米ドルのデジタル化投資も含まれています。
エネルギー分野のクラウドセキュリティ産業概要
クラウドセキュリティのプロバイダーは複数あり、激しい競争が繰り広げられています。主要参入企業は、IBM Corporation、Intel Security-McAfee、Symantec Corporation、Cisco Systems, Inc.、CA Technologies、CA Technologies、Nutanix、Netskope, Inc.、ProtectWiseなどです。コンピテンシーが高いため、市場の集中度は低いと考えられます。
- MicrosoftとSchlumbergerは、Microsoft Energy Data Servicesを開始しました。このデータソリューションは、エネルギー企業がソフトウェアアプリケーションを迅速に作成できるようにするもので、Microsoftの安全で信頼性の高いクラウドサービスを利用します。
- SchlumbergerとCogniteは戦略的パートナーシップを発表しました。CogniteはソフトウェアとIoTサービスを産業企業に提供しています。貯留層、油井、設備からのデータを単一のオープンプラットフォームに統合することで、顧客は組み込まれたAIと先進的分析機能を活用し、生産量の最大化、コスト削減、運用上のフットプリントの最小化を図ることができます。Schlumbergerは、エンタープライズデータソリューションへのアクセスを顧客に記載しています。
その他の特典
- エクセル形式の市場予測(ME)シート
- 3ヶ月間のアナリストサポート
目次
第1章 イントロダクション
- 前提条件と市場定義
- 調査範囲
第2章 調査手法
第3章 エグゼクティブサマリー
第4章 市場力学
- 市場概要
- 市場促進要因と市場抑制要因の採用
- 市場促進要因
- サプライチェーン全体でのIoT導入の増加
- サイバー脅威の増加
- 市場抑制要因
- 既存アーキテクチャとの統合
- 産業のバリューチェーン分析
- 産業の魅力-ポーターのファイブフォース分析
- 新規参入業者の脅威
- 買い手/消費者の交渉力
- 供給企業の交渉力
- 代替品の脅威
- 競争企業間の敵対関係の強さ
- COVID-19の産業への影響評価
第5章 市場セグメンテーション
- ソリューションタイプ
- ID確認とアクセス管理
- データ損失防止
- IDS/IPS
- セキュリティ情報とイベント管理
- 暗号化
- その他のソリューション
- セキュリティタイプ
- アプリケーションセキュリティ
- データベースセキュリティ
- エンドポイントセキュリティ
- ネットワークセキュリティ
- Web・メールセキュリティ
- その他のセキュリティ
- サービスモデル
- IaaS(Infrastructure-as-a-Service)
- PaaS(Platform-as-a-Service)
- SaaS(Software-as-a-Service)
- 展開タイプ
- パブリッククラウド
- プライベートクラウド
- ハイブリッドクラウド
- 地域
- 北米
- 欧州
- アジア太平洋
- ラテンアメリカ
- 中東・アフリカ
第6章 競合情勢
- 企業プロファイル
- IBM Corporation
- Intel Security-McAfee
- Cisco Systems, Inc.
- Broadcom Inc.
- Qualys, Inc.
- Nutanix
- ProtectWise
- AmazonWebServices
第7章 投資分析
第8章 市場の将来
The Cloud Security Market in Energy is expected to grow from USD 1.50 billion in 2025 to USD 2.41 billion by 2030, at a CAGR of 10% during the forecast period (2025-2030).

Considering that nations want to reduce their carbon impact and switch to renewable energy sources, the energy sector is in the midst of a major transformation. The need to reduce greenhouse gas emissions, the falling cost of renewables, and the adoption of new technologies, such as smart grids, have increased the demand for storing, managing, and analyzing data. Energy firms have greatly benefited from using cloud technology to collect and utilize this data. Utility companies are collaborating with various cloud computing firms to provide security for this important data.
Key Highlights
- According to Gartner, by 2024, cloud computing will account for more than 45% of IT spending on system infrastructure, infrastructure software, application software, and business process outsourcing. According to a recent Deloitte report, 83% of energy and utility companies either use cloud services or want to do so within the next two years. Many variables, such as greater agility and flexibility, lower capital expenditure (CapEx) costs, and enhanced operational efficiency, drive the use of clouds in the energy and utilities sector.
- Security becomes paramount when the systems are accessed outside the office premises. Legacy equipment is one of the main challenges of the energy sector. Operational Technology (OT) networks are becoming more connected because they are typically constructed using equipment over 15 years old. Security issues arise due to the fusion of the IT (Information Technology) and OT environments.
- The Covid-19 pandemic was the most important time for Cloud Storage as a revolutionary technology, further driving the demand for cloud security services. For power plants accessing the systems securely from remote locations became essential. Some companies switched to digital solutions like Zero Trust architecture, which provided security teams with greater contextual information by combining feeds from various places on a single dashboard in real time.
- April 2022 - Bharat Petroleum Corporation (BPCL) signed a contract with Microsoft that will give BPCL the intelligence to revamp its operations, create smarter supply chains, and boost customer engagement. Microsoft will provide network and security services to the organization in this seven year deal.
Energy Sector Cloud Security Market Trends
Increasing Number of Cyber Attacks to Drive the Need for Cloud Security in the Energy Sector
- Companies in the energy sector frequently have to manage thousands of different suppliers, operate in many locations, and source their products from other continents. This makes them a prominent target for both hackers and cyber terrorists. To ensure the appropriate level of security, companies must monitor the vulnerabilities in their products during their entire lifecycle and adhere to the most recent standards and regulations.
- A cyber attack can cost a lot of money and lead to power disruptions or the leaking of confidential customer data. This could significantly affect the company's business operations and those who depend on its services. By hiring a cybersecurity company, Energy firms can encrypt sensitive data and train employees on how to protect from malicious attacks.
- In february 2022, the disruption at Oiltanking in Germany, SEA-Invest in Belgium, and Evos in the Netherlands affected dozens of terminals with oil storage and transport worldwide. These cyber-attacks compel companies to operate at a limited capacity, giving rise to supply chain issues.
- Further, in April 2022 - Oil India suffered a cyberattack disrupting its operations in Assam. The cyberattack occurred at one of the workstations of OIL's Geological and Reservoir department (Oil India Ltd.). The cyberattacker demanded USD 7.5 million as a ransom through a note from the infected PC. However, the drilling and production work was unaffected. Source: https://www.mordorintelligence.com/industry-reports/cloud-security-in-energy-sector-industry
- Moreover, in November 2023, Nasuni, one of the leading hybrid cloud storage solutions, announced a strategic partnership with Cegal, one of the global leaders of digital solutions for the energy industry. Energy Organizations Increasingly Rely on Nasuni for Accelerating Cloud Transformations, Modernizing File Data Architectures and Enhanced Cyber Resiliency Nasuni and Cegal are assisting organizations to accelerate their cloud transformations by providing the technology infrastructure and expertise needed to manage and protect data at scale from any location.
Europe is Expected to Witness the Highest Growth
- Public agencies and the European government had to adapt their organizations to meet the increased demand for online services. This created a demand for cloud computing technologies that led infrastructure and services essential for staying competitive in a hypercomplex global economy.
- The European energy system needs to undergo a significant transition, with digitalization playing a pivotal role, in addressing the climate issue and reduce the EU's reliance on Russian fossil fuels. To support these developments, European Union formed a Smart Energy Expert Group to support the development and rolling out of a common European data space for energy.
- 51% of all EU households and SMEs are equipped with smart electricity meters, and various policies have been introduced to guide the digitalization of energy as issues like security, privacy, and consumer protection. In consultation with Network and Information Security Group (NIS), the Commission will identify the specific ICT services, systems, and products that might be subjected to coordinated risk assessments with priority.
- The UK experienced the warmest summer in 2022, and the extreme weather caused temporary failures at Oracle and Google Cloud's data centers in London. Water scarcity and energy insecurity made data center operators uneasy, which affected cloud computing operations. To overcome these uncertainties, EC plans an investment of USD 620 billion in the electricity grid, including USD 180.4 billion in digitalization.
Energy Sector Cloud Security Industry Overview
There is intense competition with several providers of Cloud Security. The major players include IBM Corporation, Intel Security- McAfee, Symantec Corporation, Cisco Systems, Inc., CA Technologies, CA Technologies, Nutanix, Netskope, Inc., and ProtectWise. Due to high competency, the market concentration will be low.
- Microsoft and Schlumberger launched Microsoft Energy Data Services. This data solution will make it possible for energy corporations to create software applications quickly, and it will be powered by Microsoft's secure and trusted cloud services.
- Schlumberger and Cognite announced a strategic partnership. Cognite provides software and IoT services to industrial companies. While integrating data from reservoirs, wells, and facilities into a single, open platform, clients can utilize embedded AI and advanced analytics capabilities to maximize production, save costs, and minimize operational footprint. Schlumberger will provide customers with access to the Enterprise Data Solution.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 StudyAssumptionsandMarketDefinition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET DYNAMICS
- 4.1 Market Overview
- 4.2 Introduction to Market Drivers and Restraints
- 4.3 Market Drivers
- 4.3.1 Increasing Adoption of IoT across the Supply Chain
- 4.3.2 Increasing Number of Cyber Threats
- 4.4 Market Restraints
- 4.4.1 Integration with Existing Architecture
- 4.5 Industry Value Chain Analysis
- 4.6 Industry Attractiveness - Porter's Five Force Analysis
- 4.6.1 Threat of New Entrants
- 4.6.2 Bargaining Power of Buyers/Consumers
- 4.6.3 Bargaining Power of Suppliers
- 4.6.4 Threat of Substitute Products
- 4.6.5 Intensity of Competitive Rivalry
- 4.7 An Assessment of the Impact of COVID-19 on the Industry
5 MARKET SEGMENTATION
- 5.1 Solution Type
- 5.1.1 Identity and Access Management
- 5.1.2 Data Loss Prevention
- 5.1.3 IDS/IPS
- 5.1.4 Security Information and Event Management
- 5.1.5 Encryption
- 5.1.6 Other Solution Type
- 5.2 Security Type
- 5.2.1 Application Security
- 5.2.2 Database Security
- 5.2.3 Endpoint Security
- 5.2.4 Network Security
- 5.2.5 Web & Email Security
- 5.2.6 Other Security Type
- 5.3 Service Model
- 5.3.1 Infrastructure-as-a-Service
- 5.3.2 Platform-as-a-Service
- 5.3.3 Software-as-a-Service
- 5.4 Deployment Type
- 5.4.1 Public Cloud
- 5.4.2 Private Cloud
- 5.4.3 Hybrid Cloud
- 5.5 Geography
- 5.5.1 North America
- 5.5.2 Europe
- 5.5.3 Asia Pacific
- 5.5.4 Latin America
- 5.5.5 Middle East and Africa
6 COMPETITIVE LANDSCAPE
- 6.1 Company Profiles
- 6.1.1 IBM Corporation
- 6.1.2 Intel Security - McAfee
- 6.1.3 Cisco Systems, Inc.
- 6.1.4 Broadcom Inc.
- 6.1.5 Qualys, Inc.
- 6.1.6 Nutanix
- 6.1.7 ProtectWise
- 6.1.8 AmazonWebServices


