
|
市場調査レポート
商品コード
1639422
サイバーテロ対策:市場シェア分析、産業動向・統計、成長予測(2025年~2030年)Counter Cyberterrorism - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
カスタマイズ可能
適宜更新あり
|
|||||||
| サイバーテロ対策:市場シェア分析、産業動向・統計、成長予測(2025年~2030年) |
|
出版日: 2025年01月05日
発行: Mordor Intelligence
ページ情報: 英文 122 Pages
納期: 2~3営業日
|
全表示
- 概要
- 目次
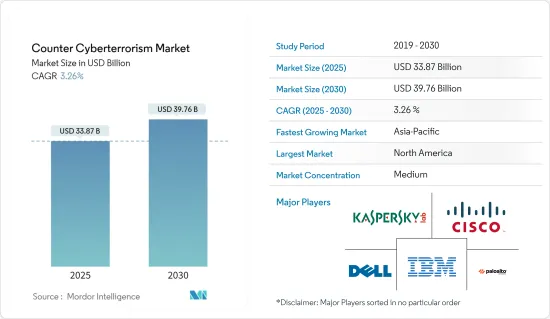
サイバーテロ対策市場規模は2025年に338億7,000万米ドルと推定され、予測期間(2025~2030年)のCAGRは3.26%で、2030年には397億6,000万米ドルに達すると予測されます。
サイバーテロ対策市場の主要原動力は、国家にさまざまな影響を与える可能性のあるサイバーテロに対する恐怖心の高まりであり、このような攻撃を防ぐためのサイバーセキュリティソリューションの展開につながっています。さらに、攻撃への恐怖は調査期間中に大幅に増加しており、より強力で安全なソリューションの構築と展開に各国首脳の注目が集まっています。
主要ハイライト
- 情報・手続きのデジタル化とインターネットプラットフォームの世界の普及により、サイバーテロの絶対的リスクは増大しています。相互接続が進む世界と、ビジネスや社会におけるデジタル技術やプロセス(IoT、クラウド、モバイル、ビッグデータ、人工知能)の導入は、日常生活を変化させ、その運営方法を一変させました。
- あらゆるものがつながるようになったことで、セキュリティ、コンプライアンス、データ保護の課題がより大きくなり、サイバーテロの絶対的リスクも高まっています。サイバー犯罪者はまた、組織のセキュリティを突破し、IPから個々の顧客情報まであらゆるものにアクセスするための新たな手法に取り組んでいます。このため、効果的な対策の必要性が高まっており、サイバーテロ対策市場を牽引しています。
- アプリケーションの識別と制御といった次世代機能の台頭により、ファイアウォール技術はより柔軟で安全なものに進化しています。さらに、ファイアウォールの増加は、外部と内部の脅威を防止するためのコンプライアンス・ガイドラインや規制の高まりが背景にあります。また、実際の内部脅威の急増により、ユーザーは現在、特にスイッチ、信頼境界、バックエンドサーバー間の内部ネットワークにファイアウォールを導入しています。サイバーテロリズムの増加やデータ盗難の急増が、調査対象市場の原動力になると予測されています。
- MicrosoftによるDigital Defense Report(2022年)では、主要な国家によるサイバー攻撃の最も一般的な目的は、スパイ活動、混乱、破壊であると指摘しています。最も一般的な手法は、偵察、クレデンシャルハーベスティング、マルウェア、VPNの悪用でした。大規模なスピアフィッシング・キャンペーンのような試行錯誤の手法も、ハッカーにとっては貴重なツールです。報告書によると、国家を標的にした攻撃の約80%は、政府、NGO、シンクタンクに対するものでした。攻撃者はNGOコミュニティと政府組織のつながりを利用して、国の施策計画や意図を理解することができます。
- さらに、電力公社、水処理サービス、保健・救急システムなどの主要インフラに対する攻撃も一般的になりつつあり、業務遂行に大きな影響を及ぼす可能性があります。
サイバーテロ対策市場の動向
サイバー攻撃の深刻化が市場を牽引
- 企業、政府、個人に対する攻撃は最近著しく増加しています。防衛関連のインフラは、国家によるサイバー攻撃者の間で最も標的とされる選択肢の1つになりつつあります。そのため、これらの組織は、以前は侵入不可能と考えられていたセキュリティシステムを破壊することの価値を認めています。
- 2022年には、Colonial Pipeline、Massachusetts Steamship Authority、JBS(世界最大の食肉業者)、ワシントンDC警視庁に対するサイバー攻撃が導入されました。米国の組織や企業に対するこれらの攻撃は、さまざまな重要インフラを停止させ、その結果、品不足、商品サービスの価格上昇、活動の停止による経済的損失をもたらしました。
- 航空宇宙領域におけるマシンツーマシン(M2M)技術の採用の増加や、サイバーテロ対策としてサイバーセキュリティの拡大に注力する政府の動きが、過去10年間のサイバーセキュリティ市場の成長につながりました。
- サイバーテロの脅威の可能性は、広く懸念の火種となっています。複数のセキュリティ専門家や議員などによると、サイバーテロリストは政府や企業のコンピュータ・ネットワークをハッキングし、先進国の金融、軍事、サービス部門を麻痺させています。
- さらに、世界中で急増するデータ漏洩は、サイバーテロ対策市場の主要促進要因の1つとなっています。したがって、データ漏洩の事例の増加は、サイバーテロ対策市場に様々な成長機会を生み出すと考えられます。SurfSharkによると、2022年第1四半期に世界のインターネットユーザーは約1,810万件のデータ漏洩を経験しました。
北米が大きな市場シェアを占める
- 米国はサイバーテロの標的となり、そのような攻撃に対抗するために最も重要な国です。さらに、同国は国家主導のサイバー攻撃で他国からの大きな批判にもさらされています。しかし、このような攻撃の実施にアメリカのセキュリティ機関や政府が関与していると全面的に主張できるような事件は起きていないです。
- 2022年2月、北京に拠点を置くサイバーセキュリティ企業が、米国家安全保障局が45カ国以上の企業や政府をスパイするためのバックドアを作成したと告発しました。中国外務省の代表者によると、このような行為は中国の重要インフラの安全を脅かし、企業秘密を危険にさらす可能性があるといいます。
- 米国平和ラボによると、9.11以前から、軍事産業やエネルギー産業のコンピューター・ネットワークに明らかな脆弱性があることが、いくつかの演習で明らかになっていました。9.11の後、安全保障とテロリズムのシナリオは急速にサイバーテロリズムを含むものへと変化し、政治、企業、安全保障に関心を持つ関係者はこれを奨励しました。
- バイデン大統領は、サイバーセキュリティを国土安全保障省(DHS)の任務の重要な要素であることから、バイデン=ハリス政権のあらゆるレベルにおける最優先事項としています。マヨルカス長官は、ハンプトン大学とGirl Scouts of the USAとの提携によるRSAカンファレンス主催の仮想講演で、同省のサイバーセキュリティ活動に関する広範なビジョンとロードマップについて概説しました。
- 2023年2月、米国連邦保安局は、法執行資料、従業員の個人情報、連邦捜査の対象となる可能性のある情報など、最も重要な情報の一部が漏洩した重大なランサムウェア攻撃を調査しています。このサイバー攻撃は、サービス内の独立系システムに影響を与えた「重大インシデント」とみなされています。
サイバーテロ対策産業概要
サイバーテロ対策市場は、世界規模で様々な参入企業が活動しているため、若干競合が激しいです。市場の主要企業には、Cisco Systems Inc.、Palo Alto Networks、IBM Corporationなどがあります。
2023年1月、11月のAll India Institute of Medical Science(AIIMS)攻撃の後、National Counter Ransomware Taskforce(NCRT)が導入されました。中央政府は、今後このような攻撃を防ぐためのタスクフォースに取り組みました。政府は特にサイバーテロ、サイバースパイ、ランサムウェアを懸念しており、特にAIIMS攻撃の調査中に中国とパキスタンの関与の可能性が浮上したためです。
2022年5月、イタリア上院、国防省、国立衛生ラボなど、イタリアのいくつかの機関のウェブサイトがオフラインになり、数時間アクセス不能になりました。これは初日に数日間にわたって行われたサイバー攻撃で、他のイタリアのウェブサイトや他国も標的にされました。親ロシア派のハッカー集団であるKillnetとLegionは、彼らのTelegramチャネルであるkillnet_channelとlegion_russiaを通じて攻撃を主張しました。彼らはイタリアのウェブサイトへのDDoS(分散型サービス拒否)攻撃を行うためにMiraiマルウェアを使用しました。
2022年1月、ベルギー国防省はサイバー攻撃を検知し、影響を受けたネットワークの一部を隔離しました。ベルギー国防省は、同省のメールシステムを含むコンピュータネットワークの一部を何日間もシャットダウンしました。攻撃者はLog4jの脆弱性を利用してネットワークにアクセスしました。
その他の特典
- エクセル形式の市場予測(ME)シート
- 3ヶ月のアナリストサポート
目次
第1章 イントロダクション
- 調査の前提条件と市場定義
- 調査範囲
第2章 調査手法
第3章 エグゼクティブサマリー
第4章 市場洞察
- 市場概要
- 産業バリューチェーン分析
- 産業の魅力-ポーターのファイブフォース分析
- 供給企業の交渉力
- 消費者の交渉力
- 新規参入業者の脅威
- 競争企業間の敵対関係
- 代替品の脅威
- 産業のガイドラインと施策
- COVID-19の市場への影響評価
第5章 市場力学
- 市場促進要因
- 国家安全保障に関する懸念の高まり
- 重要データを保護するための政府の取り組みの増加
- 市場抑制要因
- サイバー戦争の専門家の不足
第6章 市場セグメンテーション
- エンドユーザー産業別
- 防衛
- 航空宇宙
- BFSI
- 企業
- 電力・公益事業
- 政府機関
- その他
- 地域別
- 北米
- 欧州
- アジア
- ラテンアメリカ
- 中東・アフリカ
第7章 競合情勢
- 企業プロファイル
- AO Kaspersky Lab
- Cisco Systems
- Dell Inc.
- DXC Technology Company
- International Intelligence Limited
- Palo Alto Networks
- Nexusguard Limited
- Leidos
- IBM Corporation
- Raytheon Company
- Symantec Corporation
- SAP SE
第8章 投資分析
第9章 市場の将来
The Counter Cyberterrorism Market size is estimated at USD 33.87 billion in 2025, and is expected to reach USD 39.76 billion by 2030, at a CAGR of 3.26% during the forecast period (2025-2030).

The Counter Cyberterrorism market is primarily driven by the growth in fear of cyberterrorism, which can impact a nation in several ways, leading to the deployment of cybersecurity solutions to prevent such attacks. Furthermore, the fear of attacks has increased significantly in the studied period, drawing the attention of state heads to building and deploying stronger and more secure solutions.
Key Highlights
- The digitalization of information & procedures and the increasing penetration of Internet platforms across the globe have increased the absolute risk of cyberterrorism. The increasingly interconnected world and the adoption of digital technologies and processes (IoT, cloud, mobile, big data, and artificial intelligence) in business and society have changed everyday life and revolutionized how they run.
- The rise in the connectivity of everything brings greater security, compliance, and data protection challenges and increases the absolute risk of cyberterrorism. Cybercriminals are also working on new methodologies to get through organizations' security and access everything from IP to individual customer information. This enhances the need for effective measures, thus driving the counter-cyberterrorism market.
- With the rise of next-generation features like application identification & control, firewall technology is evolving to become more flexible and secure. Moreover, the increase in firewalls is driven by the rising compliance guidelines and regulations to prevent external and internal threats. Also, due to the surge in real internal threats, users are now deploying firewalls in their internal networks, especially between switches, trust boundaries, and back-end servers. The market studied is anticipated to be driven by increasing cyberterrorism and the rapid rise in data theft.
- In the Digital Defense Report (2022) by Microsoft, the organization identified the most common goals of major nation-state cyberattacks as espionage, disruption, and destruction. The most common methods were reconnaissance, credential harvesting, malware, and VPN exploitation. Tried and tested methods like large-scale spear-phishing campaigns are also valuable tools to hackers. According to the report, around 80% of nation-state-targeted attacks were on governments, NGOs, and think tanks. Attackers can utilize the connections between the NGO community & government organizations to understand national policy plans and intentions.
- Moreover, attacks on key infrastructures, such as power utilities, water treatment services, and health and emergency systems, are becoming more common and can have major consequences on operational performance.
Counter Cyberterrorism Market Trends
Growing Severity of Cyberattacks to Drive the Market
- Attacks on businesses, governments, and individuals have recently increased significantly. Infrastructure related to defense is fast becoming one of the most targeted choices among state-sponsored cyberattackers. Hence, these organizations have been acknowledging the value of disrupting the security systems that were previously considered impenetrable.
- Cyberattacks were introduced against Colonial Pipeline, the Massachusetts Steamship Authority, JBS (the world's largest meatpacker), and the Washington DC Metropolitan Police Department in 2022. These attacks on US organizations and firms had caused various key infrastructures to be shut down, resulting in shortages, higher prices of goods & services, and financial losses resulting from activities being halted.
- The increased adoption of machine-to-machine (M2M) technologies in the aerospace domain and the government's increasing focus on expanding cybersecurity to counter cyberterrorism have led to the cybersecurity market's growth over the past decade.
- The possible threat of cyberterrorism has sparked widespread concern. According to several security professionals, legislators, and others, cyberterrorists have hacked into government and commercial computer networks, crippling industrialized countries' financial, military, and service sectors.
- Moreover, the surge in data breaches throughout the globe acts as one of the key drivers for the counter-cyberterrorism market. Hence, the rising cases of data breaches will create various growth opportunities in the counter-cyberterrorism market. According to SurfShark, during the first quarter of 2022, worldwide Internet users saw approximately 18.1 million data breaches.
North America Accounts for Significant Market Share
- The United States is the most vital country targeted by cyberterrorism and countering such attacks. Moreover, the country also faces significant criticism from other nations for its state-sponsored cyber attacks; however, no such incident can fully claim the involvement of American security agencies or government in conducting such attacks.
- In February 2022, A Beijing-based cybersecurity firm accused the U.S. National Security Agency of creating a backdoor to spy on businesses and governments in more than 45 nations. According to a representative for China's Foreign Ministry, actions like this could jeopardize the security of China's essential infrastructure and compromise trade secrets.
- According to the United States Institute of Peace, even before 9/11, several exercises revealed apparent vulnerabilities in the military and energy industries' computer networks. Following 9/11, the security and terrorism narrative quickly shifted to include cyberterrorism, which interested political, corporate, and security actors encouraged.
- President Biden has made cybersecurity a high priority for the Biden-Harris Administration at all levels of government since it is a critical component of the Department of Homeland Security's (DHS) mission. In a virtual address hosted by the RSA Conference in partnership with Hampton University and the Girl Scouts of the USA, Secretary Mayorkas outlined his broader vision and a roadmap for the Department's cybersecurity activities.
- In February 2023, The U.S. Marshals Service is investigating a significant ransomware attack that has compromised some of its most important information, including law enforcement materials, employees' personal information, and potential targets of federal investigations. The cyberattack was considered a "major incident" impacting a stand-alone system within the service.
Counter Cyberterrorism Industry Overview
The counter-cyberterrorism market is slightly competitive, owing to various players operating on a global scale. Some of the market's top players are Cisco Systems, Palo Alto Networks, and IBM Corporation.
In January 2023, The National Counter Ransomware Taskforce (NCRT) was introduced after the November All India Institute of Medical Science (AIIMS) attack. The central government worked on a task force to prevent such attacks in the future. The government was particularly concerned about cyber terrorism, cyber espionage, and ransomware, especially since the likely involvement of China and Pakistan has come to the name during investigations into the AIIMS attack.
In May 2022, Several Italian institutional websites, including the Italian Senate, the Ministry of Defense, and the National Institute of Health, were taken offline and unreachable for a few hours. This was a multiday cyber attack on day one, which targeted other Italian websites and other countries. The pro-Russian hacker groups Killnet and Legion claimed the attacks through their Telegram channels, killnet_channel and legion_russia. They used the Mirai malware to perform their DDoS (distributed denial-of-service) attacks on Italian websites.
In January 2022, The Belgian Defense Ministry detected a cyberattack and isolated the affected parts of its network. Belgium's Defense Ministry shut down parts of its computer network, including the ministry's mail system, for many days. The attackers used the Log4j vulnerability to gain access to the network.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Bargaining Power of Suppliers
- 4.3.2 Bargaining Power of Consumers
- 4.3.3 Threat of New Entrants
- 4.3.4 Competitive Rivalry Within the Industry
- 4.3.5 Threat of Substitutes
- 4.4 Industry Guidelines and Policies
- 4.5 Assessment of the Impact of COVID-19 on the Market
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Increasing Concerns Regarding National Security
- 5.1.2 Increasing Government Initiatives to Secure Critical Data
- 5.2 Market Restraints
- 5.2.1 Lack of Cyber Warfare Professionals
6 MARKET SEGMENTATION
- 6.1 By End-user Industry
- 6.1.1 Defense
- 6.1.2 Aerospace
- 6.1.3 BFSI
- 6.1.4 Corporate
- 6.1.5 Power and Utilities
- 6.1.6 Government
- 6.1.7 Other End-user Industries
- 6.2 By Geography
- 6.2.1 North America
- 6.2.2 Europe
- 6.2.3 Asia
- 6.2.4 Latin America
- 6.2.5 Middle East and Africa
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 AO Kaspersky Lab
- 7.1.2 Cisco Systems
- 7.1.3 Dell Inc.
- 7.1.4 DXC Technology Company
- 7.1.5 International Intelligence Limited
- 7.1.6 Palo Alto Networks
- 7.1.7 Nexusguard Limited
- 7.1.8 Leidos
- 7.1.9 IBM Corporation
- 7.1.10 Raytheon Company
- 7.1.11 Symantec Corporation
- 7.1.12 SAP SE


