
|
市場調査レポート
商品コード
1849970
クラウドセキュリティソフトウェア:市場シェア分析、産業動向、統計、成長予測(2025年~2030年)Cloud Security Software - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
カスタマイズ可能
適宜更新あり
|
|||||||
| クラウドセキュリティソフトウェア:市場シェア分析、産業動向、統計、成長予測(2025年~2030年) |
|
出版日: 2025年06月18日
発行: Mordor Intelligence
ページ情報: 英文 120 Pages
納期: 2~3営業日
|
概要
クラウドセキュリティソフトウェア市場は現在、501億1,000万米ドルを生み出し、2030年には950億3,000万米ドルに達し、CAGR 13.7%で成長すると予測されています。
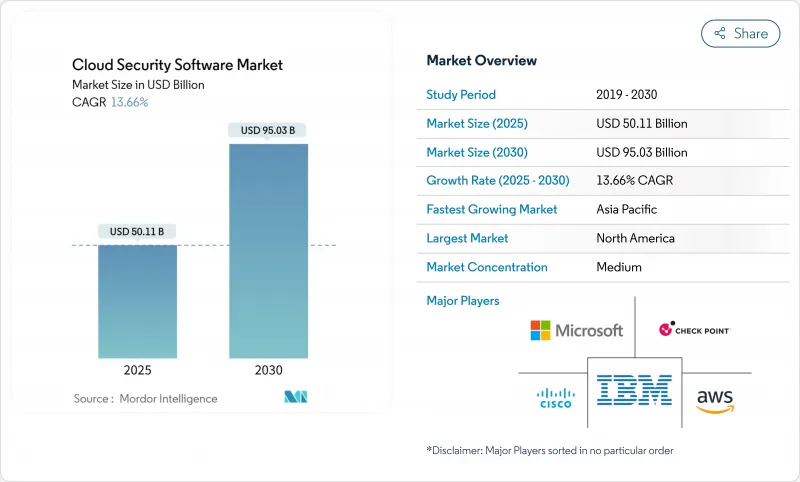
この成長軌道は、デジタルインフラストラクチャーの近代化を急ぐ規制産業、ゼロトラストフレームワークの採用、およびジェネレーティブAI主導の脅威の出現によって形成される強固なクラウドセキュリティソフトウェア市場規模を裏付けています。コンプライアンス義務の強化、ソブリン・クラウド・ポリシー、ハイパースケーラーによる設備投資により、マルチクラウドの展開全体で統一されたセキュリティ・オーケストレーションに対する需要が高まっています。企業は、重要なワークロードをパブリッククラウドに移行する際、リスク管理を合理化し、ビジネスのスピードを維持するために、アイデンティティ管理、ランタイム保護、自動化されたコンプライアンスレポートを優先します。ベンダー間の競争は、より迅速な検知、誤検知率の低減、多様なクラウド環境へのシームレスな統合を約束するプラットフォーム統合とネイティブAI機能が中心となっています。
世界のクラウドセキュリティソフトウェア市場の動向と洞察
規制産業におけるパブリッククラウドの急速な普及
監督機関がクラウドガイダンスを更新する中、規制対象企業はレガシーアーキテクチャの再構築を進めています。連邦金融機関審査委員会は現在、リアルタイムのサードパーティリスクモニタリングを強調しており、銀行や保険会社はコンプライアンスエビデンスを継続的に検証する自動化コントロールの採用を促しています。ヘルスケア・プロバイダーも同様に、単なる規制の枠にとらわれることなく、競争上のメリットをもたらすセキュリティ認証と近代化計画を整合させています。連邦リスク・権限管理プログラムの改革は、クラウド移行をさらに正当化し、請負業者やサプライヤ全体に採用の期待を連鎖させる。ベンダーは、オンボーディングに要する時間を短縮し、ポリシーをマルチクラウド施設全体のプログラム的なガードレールに変換する、あらかじめパッケージ化されたコンプライアンス・テンプレートで対応します。
マルチクラウドとハイブリッドクラウドの複雑性の急増
企業は通常、3.2社のクラウドプロバイダーでワークロードを実行し、ポリシーのサイロ化と統合の負債を増大させています。異なるAPIと多様なセキュリティモデルにより、基盤となるインフラストラクチャに依存せずに制御を正規化できる一元化されたオーケストレーションへの需要が高まっています。そのため、クラウドネイティブなアプリケーション保護プラットフォームは、コンテナやサーバーレス機能全体の誤設定や実行時の異常を検出することで支持を集めています。組織はもともと多様化のためにマルチクラウドを追求していたが、今ではコスト、パフォーマンス、管轄の要件が多様化する中で、運用の実行可能性を維持するためにオーケストレーションに依存しています。
レガシーセキュリティスタックとの統合負債
セキュリティ・リーダーは、クラウド制御がオンプレミス投資の上に重なるため、ツールの重複や一貫性のないポリシーに悩まされています。特にハブ&スポーク・ネットワークにゼロトラスト・モデルを後付けする場合、並列環境は攻撃経路を不明瞭にし、運用コストを増大させる。統合されたテレメトリがなければ、脅威インテリジェンスはサイロ化されたままとなり、修正サイクルが長期化し、セキュリティ費用に対するリターンが損なわれます。
セグメント分析
クラウドID/アクセス管理は、ゼロトラスト展開の要としての役割を反映し、2024年のクラウドセキュリティソフトウェア市場シェア34.8%を占めました。このセグメントの確固たる地位は、組織が横移動リスクを軽減するために最小特権ポリシーを優先していることから、より広範なクラウドセキュリティソフトウェア市場を下支えしています。同時に、Cloud-Native Application Protection PlatformsとCloud Workload Protection Platformsは、2030年までのCAGRが14.5%に達し、ランタイムセーフガードを必要とするコンテナ化されたワークロードの急増を反映しています。クラウド・アクセス・セキュリティ・ブローカーや脆弱性スキャナは、DevSecOpsパイプラインに統合され、開発と実運用にわたって継続的な評価を提供します。
統合されたロギングの需要は、機械学習を活用してクラウドスケールのテレメトリを解析し、平均検出時間を短縮するプラットフォームによって、セキュリティ情報とイベント管理の近代化を促進します。ベンダーは、SEALSQのCrystal KyberとCrystal Dilithiumのショーケースで実証されたように、耐量子アルゴリズムをさらに試行し、暗号化境界の長期的な進化を示します。このような技術革新はカテゴリー境界を再編成し、プラットフォーム・ベンダーが隣接する機能を統合スイートとしてまとめ、調達と運用を簡素化することを後押ししています。
パブリッククラウドは、2025年に2,150億米ドルに達するハイパースケーラ投資に後押しされ、2024年のクラウドセキュリティソフトウェア市場規模の65.4%のシェアを維持した。アマゾンだけでも750億米ドル以上を割り当て、ネイティブ・セキュリティ・サービスと地理的冗長性を強化しています。パブリッククラウドのスケールメリットにもかかわらず、ハイブリッドおよびマルチクラウド環境のCAGRは最速の15.2%に達しています。
ハイブリッドの複雑性はポリシーの抽象化の必要性を高め、セキュリティプロバイダーはKubernetesクラスタ、SaaSアプリケーション、オンプレミス資産にまたがる統一ルールをプッシュする中央ダッシュボードを提供するよう促しています。プライベート・クラウドの採用は、機密性の高い知的財産やレイテンシが重要なワークロードを抱える業界の間で根強く残っていますが、多くの企業はプライベート環境を、コンプライアンスのハードルが緩和されれば、より広範なパブリック導入に向けた過渡的な通過点として扱っています。
クラウドセキュリティソフトウェア市場レポートは、ソフトウェア(クラウドIAM、CASB、CNAPP/CWPPなど)、導入形態(パブリッククラウド、プライベートクラウド、ハイブリッド/マルチクラウド)、組織規模(大企業および中小企業)、エンドユーザー業界(BFSI、ITおよびテレコム、ヘルスケアおよびライフサイエンスなど)、地域別に分類されています。
地域分析
北米は2024年に41.3%の収益シェアを維持し、クラウドセキュリティソフトウェア市場で最大の地域スライスを示します。連邦リスク・権限管理プログラムの近代化により、民間機関、請負業者、規制の厳しい業界におけるクラウド管理への信頼が高まっています。同時に、米国司法省のデータ・セキュリティ・プログラムは、海外のデータ・トラフィックを扱う通信会社に新たなコンプライアンス層を導入し、重複するルール・セットを調整する自動ポリシー・マッピング・ツールの機会を生み出しています。
アジア太平洋地域は、2030年までのCAGRが14.7%と最も急速に成長している地域であり、主権クラウド指令、5Gの展開、広範なデジタル化に支えられています。しかし、深刻な人材不足が実行スケジュールを脅かしています。日本のスキル不足はトレーニングの必要性を強調しており、大学、クラウドプロバイダー、セキュリティベンダーがパートナーシップを結んで資格取得の機会を拡大することに拍車をかけています。中国は、主権に関する義務に対応するために国内調達のセキュリティ・スタックを推進し、インドは、多様な企業基盤に対応するために低コストでスケーラブルなソリューションを重視しています。オーストラリア、ニュージーランド、韓国は、先進的なネットワークインフラを活用し、金融取引やスマートファクトリー環境向けに低遅延での保護を実現するリアルタイムの脅威検知プラットフォームを採用しています。
欧州は、イノベーションと主権の微妙なバランスをうまく調整しています。一般データ保護規則(General Data Protection Regulation)と進化するネットワーク・情報セキュリティ指令(Network and Information Security Directive)は、データのローカライゼーション・オプションと透明な監査証跡を提供するプロバイダーを優遇する調達基準を形成しています。ドイツは製造業での採用をリードし、フランスは重要なインフラプロジェクトを支えるため、国ごとにホスティングされたクラウドゾーンに投資しています。ブレグジット後の英国は、独自のデータ・セキュリティ・スタンスを構築しながらも、国境を越えた移転を促進するために緊密に連携しています。地域的なハーモナイゼーションの努力により、ベンダーの参入は簡素化されているが、指令の移行のスケジュールが国によって異なるため、統一された展開戦略は依然として複雑です。
その他の特典:
- エクセル形式の市場予測(ME)シート
- 3ヶ月間のアナリストサポート
よくあるご質問
目次
第1章 イントロダクション
- 調査の前提条件と市場の定義
- 調査範囲
第2章 調査手法
第3章 エグゼクティブサマリー
第4章 市場情勢
- 市場概要
- 市場促進要因
- 規制産業におけるパブリッククラウドの導入が急増
- マルチクラウドとハイブリッドクラウドの複雑さの急増
- ゼロトラストアーキテクチャの要件
- 生成AIによる脅威ベクトル
- サイバー保険料インセンティブ
- EUとAPACにおけるソブリンクラウドの取り組み
- 市場抑制要因
- レガシーセキュリティスタックとの統合負債
- クラウドネイティブスキルの不足
- 管轄区域をまたぐコンプライアンス上の矛盾
- 永続的なシャドーITとBYODの行動
- バリューチェーン分析
- 規制とコンプライアンスの情勢
- テクノロジーの展望
- ポーターのファイブフォース分析
- 供給企業の交渉力
- 買い手の交渉力
- 新規参入業者の脅威
- 代替品の脅威
- 競争企業間の敵対関係
第5章 市場規模と成長予測
- ソフトウェア別
- クラウドIAM
- CASB
- CNAPP/CWPP
- 脆弱性とリスク管理
- Web、メール、DNSセキュリティ
- SIEMとログ管理
- 展開モード別
- パブリッククラウド
- プライベートクラウド
- ハイブリッド/マルチクラウド
- 組織規模別
- 大企業
- 中小企業
- エンドユーザー業界別
- BFSI
- ITおよび通信
- ヘルスケアとライフサイエンス
- 小売・消費財
- 製造業
- その他
- 地域別
- 北米
- 米国
- カナダ
- メキシコ
- 欧州
- ドイツ
- 英国
- フランス
- イタリア
- スペイン
- ロシア
- その他欧州地域
- アジア太平洋地域
- 中国
- 日本
- インド
- 韓国
- オーストラリアとニュージーランド
- その他アジア太平洋地域
- 南米
- ブラジル
- アルゼンチン
- その他南米
- 中東・アフリカ
- 中東
- サウジアラビア
- アラブ首長国連邦
- トルコ
- その他中東
- アフリカ
- 南アフリカ
- ナイジェリア
- その他アフリカ
- 北米
第6章 競合情勢
- 市場集中度
- 戦略的動向
- 市場シェア分析
- 企業プロファイル
- Palo Alto Networks
- Cisco Systems
- Fortinet
- Zscaler
- Check Point Software
- IBM
- Broadcom(CA Technologies)
- Microsoft
- Trend Micro
- Okta
- CrowdStrike
- Rapid7
- Amazon Web Services(Security services)
- Google Cloud Security
- HPE(Aruba)
- Proofpoint
- Sophos
- Imperva
- Netskope
- Qualys
- F5 Networks


