
|
市場調査レポート
商品コード
1849871
セキュリティと脆弱性管理:市場シェア分析、産業動向、統計、成長予測(2025年~2030年)Security And Vulnerability Management - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
カスタマイズ可能
適宜更新あり
|
|||||||
| セキュリティと脆弱性管理:市場シェア分析、産業動向、統計、成長予測(2025年~2030年) |
|
出版日: 2025年06月30日
発行: Mordor Intelligence
ページ情報: 英文 100 Pages
納期: 2~3営業日
|
概要
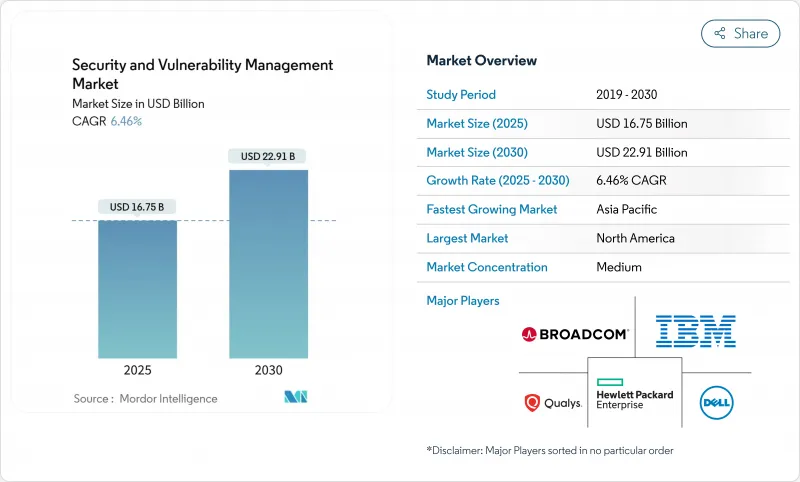
セキュリティと脆弱性管理市場規模は2025年に167億5,000万米ドルに達し、2030年には229億1,000万米ドルに拡大すると予測され、期間中のCAGRは6.5%です。
セキュリティと脆弱性管理市場は、サイバーリスク規制の義務化、取締役会の意識の高まり、ツールの乱立を抑制する統合暴露管理プラットフォームへの戦略的シフトなどの恩恵を受け続けています。急速なデジタル化、AIを活用した攻撃、ゼロトラストの採用は、マクロ経済の圧力にもかかわらず予算の伸びを維持し、セキュリティと脆弱性管理市場が企業のレジリエンスの中核的な柱であることを示しています。4分の3の企業がより少ないサプライヤーを求めているため、ベンダーの統合は依然として決定的な力となっており、プラットフォーム企業はスキャニングから自動修復への移行を進めています。リスクベースのアナリティクスは今や生の深刻度カウントを凌駕しており、セキュリティと脆弱性管理市場が引受判断のために継続的な可視化を求める保険会社とどのように整合しているかを反映しています。
世界のセキュリティと脆弱性管理市場の動向と洞察
サイバー攻撃の増加と高度化
IBMは、フィッシングによる情報窃取が前年比84%増加したことを記録し、ChatGPT-4は、識別子を提示された場合、1日限りのCVEの87%を悪用しました。製造業は、運用技術のギャップが恐喝者を誘惑するため、依然として最も狙われる業種となっています。アジア太平洋地域では、2024年にインシデントが13%増加し、セキュリティと脆弱性管理市場における優先順位がさらに高まりました。IDを中心とした侵入は現在、侵害の30%を占め、クレデンシャルの盗難が主なアクセス・ベクトルとなっています。そのため、セキュリティと脆弱性管理市場は、包括的なパッチ適用よりも、悪用可能性を重視した優先順位付けに軸足を移しています。
クラウドとDevOpsの急速な導入による攻撃対象の拡大
マイクロソフトが実施したマルチクラウドのリスク調査では、38%の組織が、重大な脆弱性を持つ、一般に公開され、高度に特権化されたワークロードを実行していることが判明しました。Palo Alto Networksは、エクスポージャーの80%がコンテナ化された環境に存在することを発見し、DevOpsがもたらす複雑性を浮き彫りにしました。小規模企業の68%はDevSecOpsを実践していると主張しているが、コミットごとにスキャンしているのはわずか12%であり、セキュリティと脆弱性管理市場が組み込みスキャンを提供する機会を創出しています。Google CloudのSecurity Command Centerに代表されるエージェントレスカバレッジは、導入時の摩擦をなくし、セキュリティと脆弱性管理市場での採用を加速します。
中小企業にとって高い総所有コスト
中小企業の経営幹部の93%がサイバーリスクを認識しているにもかかわらず、新しいツールに投資しているのはわずか36%です。欧州の調査では、侵害された中小企業の60%が6ヶ月以内に閉鎖しており、予算が逼迫していることが明らかになっています。ニューヨークの病院では、小規模な施設では年間5万米ドル、大規模なネットワークでは年間200万米ドルのコンプライアンス費用を見込んでいます。セキュリティと脆弱性管理市場は、スキャン、リスクスコアリング、ダッシュボード分析を単一のクラウドライセンスにバンドルしたサブスクリプションモデルで対応しています。
セグメント分析
セキュリティと脆弱性管理の市場規模は、脆弱性評価とレポーティングが2024年に56億米ドルに達し、総売上の33.5%に相当します。RBVMはCAGR 7.1%で拡大しているが、これは購入者が真のリスクをもたらす3%の欠陥をターゲットにしているためであり、これはTenableのVulcan Cyber買収によって検証された戦略です。コンテナとクラウドワークロードのスキャンは、Kubernetesの採用と連動して増加し、アプリケーションセキュリティテストは、コード、パイプライン、ランタイムの成果物をカバーする姿勢管理プラットフォームに統合されます。
RBVM製品は現在、脅威インテリジェンスフィード、資産の重要度スコア、エクスプロイトの可用性を取り込み、静的なリストではなくランク付けされたバックログを生成します。そのため、セキュリティと脆弱性管理市場は、検知から意思決定支援へと移行しています。パッチ&コンフィギュレーション・モジュールは、規制された垂直市場にとって、引き続き重要であり、IoT/OTスキャナは、ファームウェアの弱点を発見するために、独自のプロトコルを解析します。このようなモジュールの多様性は、企業の更新サイクルを支える単一のガラス・ビジョンの予兆です。
銀行、防衛プライム、公益事業が物理的境界内で機密データを保護するため、2024年のセキュリティと脆弱性管理市場の68.9%をオンプレミス展開が占めています。それにもかかわらず、クラウド導入は2030年までCAGR 8.1%で急増しています。Google Cloudのエージェントレス脆弱性スキャンは、ソフトウェアのロールアウトを不要にし、概念実証の取り組みを迅速化するため、SaaSデリバリーの魅力を高めています。
ハイブリッド・モデルは、内部ネットワークの低レイテンシ・スキャンと弾力的なクラウド分析を組み合わせるため、大企業のロードマップを支配しています。こうしてセキュリティと脆弱性管理市場は、オンプレミスのコレクター、プライベートクラウドのノード、ハイパースケールのアナリティクスのメッシュへと進化します。ポリシーフェデレーションにより、顧客はクラウドの利点を生かしながらNIS2やCMMCの義務を満たすことができ、どの展開モデルだけでもすべての制御フレームワークを満足させることができます。
地域分析
2024年のセキュリティと脆弱性管理市場は、北米が37.4%のシェアを占めました。CMMC 2.0や大統領令14144のような連邦政府の指令により、継続的な脆弱性ガバナンスが調達ルールに組み込まれています。カナダとメキシコは、国境を越えた重要インフラプロジェクトに同様のベースラインを採用し、支出の継続性を確保しています。高い侵害コスト、大規模な技術ベンダー基盤、活発なサイバー保険市場がリーダーシップを維持。
アジア太平洋地域の今後のCAGRは7.5%と最も高いです。PwCは、世界のサイバーインシデントの31%に対応するため、2027年の地域のサイバーセキュリティ支出を520億米ドルと予測しています。オーストラリアのサイバーセキュリティ法2024は、スマートデバイスのベースラインを施行し、ランサムウェアの支払いに関する情報開示を義務付けており、ニュージーランドのNCSCは公共部門の管理を実施しています。中国、日本、インド、韓国は製造業主導の需要を牽引し、セキュリティと脆弱性管理市場を工場フロアやクラウドスタックに押し上げます。
欧州では、NIS2が27の加盟国で施行され、エネルギー、運輸、金融、ヘルスケアの事業者に1,000万ユーロ(1,160万米ドル)に達する罰則が課されます。ドイツ、フランス、イタリア、スペイン、英国は、この指令に合わせて国内法を改正し、着実なプロジェクトパイプラインを構築しています。南米と中東・アフリカは、デジタルサービスの成長によって新たな攻撃対象が出現し、各国がEUや米国の枠組みを参考にした戦略を立案するようになったため、新たな勢いを記録しています。
その他の特典:
- エクセル形式の市場予測(ME)シート
- 3ヶ月間のアナリストサポート
よくあるご質問
目次
第1章 イントロダクション
- 調査の前提条件と市場の定義
- 調査範囲
第2章 調査手法
第3章 エグゼクティブサマリー
第4章 市場情勢
- 市場概要
- 市場促進要因
- サイバー攻撃の増加と巧妙化
- クラウドとDevOpsの急速な導入により攻撃対象領域が拡大
- 規制遵守とデータ主権の義務
- 重要インフラにおけるIoT/OT資産の急増
- サイバー保険の引受には継続的な脆弱性の可視化が必要
- サプライチェーン全体にわたるソフトウェア部品表(SBOM)の義務
- 市場抑制要因
- 中小企業にとって総所有コストが高め
- 熟練したサイバーセキュリティ人材の不足
- 脆弱性データの過負荷によるアラート疲れ
- ベンダー統合とプラットフォームロックインの懸念
- バリューチェーン分析
- 規制情勢
- テクノロジーの展望
- ポーターのファイブフォース分析
- 供給企業の交渉力
- 買い手の交渉力
- 新規参入業者の脅威
- 代替品の脅威
- 競争企業間の敵対関係
- マクロ経済動向の市場への影響評価
第5章 市場規模と成長予測
- タイプ別
- 脆弱性評価と報告
- パッチと構成管理
- リスクベースの脆弱性管理(RBVM)
- コンテナとクラウドワークロードのスキャン
- アプリケーションセキュリティテスト
- IoT/OT脆弱性管理
- 展開モード別
- オンプレミス
- クラウド
- 組織規模別
- 大企業
- 中小企業
- エンドユーザー別
- BFSI
- ヘルスケアとライフサイエンス
- 政府と防衛
- ITおよび通信
- 製造業と産業
- 小売業とeコマース
- エネルギーと公益事業
- その他
- 地域別
- 北米
- 米国
- カナダ
- メキシコ
- 欧州
- ドイツ
- 英国
- フランス
- イタリア
- スペイン
- その他欧州地域
- アジア太平洋地域
- 中国
- 日本
- インド
- 韓国
- オーストラリア
- その他アジア太平洋地域
- 南米
- ブラジル
- アルゼンチン
- その他南米
- 中東・アフリカ
- 中東
- サウジアラビア
- アラブ首長国連邦
- トルコ
- その他中東
- アフリカ
- 南アフリカ
- エジプト
- ナイジェリア
- その他アフリカ
- 北米
第6章 競合情勢
- 市場集中度
- 戦略的動向
- 市場シェア分析
- 企業プロファイル
- Tenable Holdings Inc.
- Qualys Inc.
- Rapid7 Inc.
- IBM Corporation
- Cisco Systems Inc.
- Microsoft Corporation
- Broadcom Inc.(Symantec)
- Hewlett Packard Enterprise Company
- Dell Technologies Inc.
- Trend Micro Inc.
- Palo Alto Networks Inc.
- Check Point Software Technologies Ltd.
- CrowdStrike Holdings Inc.
- Fortinet Inc.
- McAfee Corp.
- Tripwire Inc.(Belden)
- Ivanti
- ServiceNow Inc.
- ATandT Cybersecurity(AlienVault)
- Skybox Security Inc.
- F-Secure Corporation
- Flexera Software LLC(Secunia Research)
- Netskope Inc.


