|
|
市場調査レポート
商品コード
1800740
マネージドセキュリティサービス (MSS) の世界市場 (~2030年):サービスタイプ (セキュリティ運用&監視 (SOCaaS・SIEM-as-a-Service)・高度脅威検出 (MDR・MXDR)・ID&データ保護)・タイプ (フルマネージド・コマネージド) 別Managed Security Services (MSS) Market by Service Type (Security Operations & Monitoring (SOCaaS, SIEM-as-a-Service), Advanced Threat Detection (MDR, MXDR), Identity & Data Protection), Type (Fully Managed, Co-Managed) - Global Forecast to 2030 |
||||||
カスタマイズ可能
|
|||||||
| マネージドセキュリティサービス (MSS) の世界市場 (~2030年):サービスタイプ (セキュリティ運用&監視 (SOCaaS・SIEM-as-a-Service)・高度脅威検出 (MDR・MXDR)・ID&データ保護)・タイプ (フルマネージド・コマネージド) 別 |
|
出版日: 2025年08月05日
発行: MarketsandMarkets
ページ情報: 英文 417 Pages
納期: 即納可能
|
全表示
- 概要
- 図表
- 目次
世界のマネージドセキュリティサービス (MSS) の市場規模は、2025年の394億7,000万米ドルから、予測期間中はCAGR 11.1%で推移し、2030年には668億3,000万米ドルに成長すると予測されています。
| 調査範囲 | |
|---|---|
| 調査対象年 | 2019-2030年 |
| 基準年 | 2024年 |
| 予測期間 | 2025-2030年 |
| 単位 | 金額 (米ドル) |
| セグメント別 | サービスタイプ・タイプ・組織規模・産業・地域別 |
| 対象地域 | 北米・欧州・アジア太平洋・中東&アフリカ・ラテンアメリカ |
この成長の背景には、サイバー脅威の複雑化、クラウドおよびハイブリッドインフラの導入拡大、専門家主導による24時間365日のモニタリングとインシデント対応の緊急ニーズがあります。企業は、社内のスキルギャップを埋め、運用負荷を軽減し、分散環境全体で一貫したセキュリティを確保するために、MSSプロバイダーを利用するようになっています。

しかし、市場の成長は、データ主権への懸念、レガシーシステムとの統合課題、ベンダーロックインの可能性、アウトソースされたセキュリティ運用における可視性と管理の欠如によって制約されています。こうした懸念にもかかわらず、スケーラブルで成果志向型のサイバーセキュリティソリューションに対する需要の高まりが、BFSI (銀行・金融・保険) 、ヘルスケア、政府、製造業、重要インフラ分野におけるMSSの採用を後押ししている。
"タイプ別では、共同管理型セキュリティサービスの部門が予測期間中に最大のCAGRを記録"
同部門の急速な成長は、組織が内部統制と外部の専門知識との間でバランスの取れたアプローチを求めるようになっているためです。サイバー脅威の増大やITの複雑化に伴い、多くの企業が重要な業務を完全にアウトソースすることなくセキュリティ態勢を強化するために共同管理モデルを採用していす。このアプローチにより、社内チームはMSSプロバイダーと連携し、24時間365日の監視、迅速なインシデント対応、継続的なコンプライアンス支援を実現できます。
”地域別では、北米が最大のシェアを占める一方、アジア太平洋地域が予測期間中に最も急成長する見通し"
北米は、デジタルで成熟した企業の高い集中度、増大するサイバー脅威への曝露、強固な規制およびコンプライアンスポスチャにより、市場を引き続きリードしています。米国およびカナダでは、産業を問わず複雑化するIT環境の管理や、熟練したサイバーセキュリティ人材の慢性的な不足への対応が大きな課題となっています。これにより、24時間365日の監視、脅威検知、インシデント対応、コンプライアンス支援を提供するMSSの需要が急増しています。
一方、アジア太平洋地域は、予測期間中に最も高いCAGRで成長すると予測されています。この成長は、インド、中国、東南アジアといった新興経済国における急速なデジタル化、クラウド導入の拡大、サイバーインシデントの増加によって牽引されています。同地域の多くの中小・中堅企業は、内部インフラに多額の投資をすることなく、手頃でスケーラブルなサイバーセキュリティソリューションにアクセスするためにMSSPを活用しています。また、各国政府による国家的サイバーセキュリティポスチャ強化やコンプライアンス施行の取り組みが、同地域全域でのMSS採用をさらに加速させています。
当レポートでは、世界のマネージドセキュリティサービス (MSS) の市場を調査し、市場概要、市場成長への各種影響因子の分析、技術・特許の動向、法規制環境、ケーススタディ、市場規模の推移・予測、各種区分・地域/主要国別の詳細分析、競合情勢、主要企業のプロファイルなどをまとめています。
目次
第1章 イントロダクション
第2章 調査手法
第3章 エグゼクティブサマリー
第4章 重要考察
第5章 市場概要と業界動向
- 市場力学
- 促進要因
- 抑制要因
- 機会
- 課題
- ケーススタディ分析
- バリューチェーン分析
- エコシステム分析
- MSS市場における生成AIの影響
- ポーターのファイブフォース分析
- 主要な利害関係者と購入基準
- 価格分析
- 技術分析
- 特許分析
- 規制状況
- 2025年の米国関税の影響
- 顧客の事業に影響を与える動向/混乱
- MSS市場:ビジネスモデル
- 2025年の主な会議とイベント
- 投資と資金調達のシナリオ
第6章 マネージドセキュリティサービス (MSS) 市場:サービスタイプ別
- マネージドネットワークおよび境界セキュリティサービス
- マネージドファイアウォールサービス
- マネージド侵入検知・防止サービス
- マネージド統合脅威管理
- マネージドDDoS防御
- アセットディスカバリー&ネットワーク分割
- Web&DNSセキュリティゲートウェイサービス
- マネージドエンドポイント&アプリケーションセキュリティサービス
- マネージドエンドポイント検出&対応
- マネージドアンチマルウェア/アンチウイルス
- パッチ管理サービス (Patch Management-as-a-Service)
- アプリケーションホワイトリスティング&制御
- APIセキュリティ監視& 脅威防御
- OAuth& セッショントークン悪用検知
- CI/CDパイプラインセキュリティ監視
- マネージドバックアップとイミュータブルストレージ
- マネージドクラウドセキュリティサービス
- マネージドクラウドセキュリティポスチャ管理
- マネージドクラウドワークロード保護プラットフォーム
- マネージドクラウドアクセスセキュリティブローカーサービス
- SaaSセキュリティポスチャ管理
- コンテナ&Kubernetesのセキュリティ管理
- マネージドセキュリティ運用および監視サービス
- SOC-as-a-Service (セキュリティオペレーションセンターサービス)
- マネージドSIEMサービス
- マネージドインシデント対応サービス
- OT/ICS SOCモニタリング
- マネージド高度脅威検出サービス
- マネージド検出&対応
- マネージド拡張検出と対応
- Threat Intelligence-as-a-Service (脅威インテリジェンスサービス)
- Threat Hunting-as-a-Service (脅威ハンティングサービス)
- ランサムウェア復旧サービス
- Disaster Recovery & Business Continuity-as-a-Service (災害復旧 & 事業継続サービス)
- マネージド攻撃セキュリティおよび評価サービス
- マネージド侵入テストサービス
- 脆弱性評価と管理
- Red Teaming-as-a-Service (レッドチームサービス)
- セキュリティ侵入テスト (アプリ、ネットワーク、API)
- ICS/SCADAセキュリティテスト
- SOURCE CODE ANALYSIS-AS-A-SERVICE (ソースコード分析)
- マネージドIDおよびデータ保護サービス
- マネージドID&アクセス管理
- 多要素認証
- マネージドシングルサインオン
- データ損失防止
- マネージド暗号化とキーライフサイクル管理
- IDフェデレーションとロールプロビジョニングサービス
- マネージドリスク&コンプライアンス管理サービス
- コンプライアンス管理&報告
- リスクアドバイザリー&評価サービス
- ガバナンス、リスク、コンプライアンスプラットフォーム統合サービス
- フィッシングシミュレーションサービス
- 内部脅威監視と行動分析
- セキュリティ意識向上&トレーニングサービス
第7章 マネージドセキュリティサービス (MSS) 市場:タイプ別
- 完全管理型セキュリティサービス
- 共同管理セキュリティサービス
第8章 マネージドセキュリティサービス (MSS) 市場:組織規模別
- 大企業
- 中小企業
第9章 マネージドセキュリティサービス (MSS) 市場:産業別
- BFSI
- 政府
- ヘルスケア&ライフサイエンス
- 電気通信
- 情報技術および情報技術対応サービス
- 小売・Eコマース
- エネルギー&ユーティリティ
- 製造
- その他
第10章 マネージドセキュリティサービス (MSS) 市場:地域別
- 北米
- 市場促進要因
- マクロ経済見通し
- 規制状況
- 米国
- カナダ
- 欧州
- 市場促進要因
- マクロ経済見通し
- 規制状況
- 英国
- ドイツ
- フランス
- イタリア
- ロシア
- その他
- アジア太平洋
- 市場促進要因
- マクロ経済見通し
- 規制状況
- 中国
- 日本
- インド
- オーストラリア
- シンガポール
- マレーシア
- インドネシア
- タイ
- フィリピン
- その他
- 中東・アフリカ
- 市場促進要因
- マクロ経済見通し
- 規制状況
- 中東
- アフリカ
- ラテンアメリカ
- 市場促進要因
- マクロ経済見通し
- 規制状況
- ブラジル
- メキシコ
- その他
第11章 競合情勢
- 主要参入企業の戦略/強み
- 収益分析
- 市場シェア分析
- ブランド/製品比較
- 企業評価と財務指標
- 企業評価マトリックス:主要企業
- 企業評価マトリックス:スタートアップ/中小企業
- 競合シナリオ
第12章 企業プロファイル
- 主要企業
- IBM
- NTT
- LEVELBLUE
- ACCENTURE
- DXC TECHNOLOGY
- SECNAP
- DELOITTE
- SECUREWORKS
- TRUSTWAVE
- VERIZON
- FUJITSU
- HPE
- TCS
- ATOS
- ORANGE CYBERDEFENSE
- RAPID7
- TREND MICRO
- KUDELSKI SECURITY
- CROWDSTRIKE
- F5
- CAPGEMINI
- INFOSYS
- LUMEN TECHNOLOGIES
- KROLL
- その他の企業
- NETSURION
- ATLAS SYSTEMS
- CIPHER
- RSI SECURITY
- SECURITY HQ
- LIGHTEDGE
- LRQA NETTITUDE
- TECEZE
- CYFLARE
- ASCEND TECHNOLOGIES
- AVERTIUM
- DIGITALXRAID
- TRUSTNET
第13章 隣接市場
第14章 付録
List of Tables
- TABLE 1 USD EXCHANGE RATES, 2019-2024
- TABLE 2 FACTOR ANALYSIS
- TABLE 3 MANAGED SECURITY SERVICES MARKET SIZE AND GROWTH, 2019-2024 (USD MILLION)
- TABLE 4 MANAGED SECURITY SERVICES MARKET SIZE AND GROWTH, 2025-2030 (USD MILLION)
- TABLE 5 ROLE OF PLAYERS IN MANAGED SECURITY SERVICES ECOSYSTEM
- TABLE 6 PORTER'S FIVE FORCES' IMPACT ON MANAGED SECURITY SERVICES MARKET
- TABLE 7 IMPACT OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS
- TABLE 8 KEY BUYING CRITERIA FOR TOP THREE VERTICALS
- TABLE 9 AVERAGE SELLING PRICE OFFERED BY KEY PLAYERS, BY TYPE, 2024
- TABLE 10 INDICATIVE PRICING LEVELS OF MANAGED SECURITY SERVICES VENDORS, 2024
- TABLE 11 LIST OF FEW PATENTS IN MANAGED SECURITY SERVICES, 2024-2025
- TABLE 12 NORTH AMERICA: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 13 EUROPE: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 14 ASIA PACIFIC: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 15 MIDDLE EAST & AFRICA: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 16 LATIN AMERICA: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 17 KEY TARIFF RATES
- TABLE 18 EXPECTED CHANGE IN PRICES AND LIKELY IMPACT ON END-USE MARKET DUE TO TARIFF IMPACT
- TABLE 19 MANAGED SECURITY SERVICES MARKET: BUSINESS MODELS
- TABLE 20 MANAGED SECURITY SERVICES MARKET: LIST OF KEY CONFERENCES & EVENTS, 2025
- TABLE 21 MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 22 MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 23 MANAGED NETWORK & PERIMETER SECURITY SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 24 MANAGED NETWORK & PERIMETER SECURITY SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 25 MANAGED ENDPOINT & APPLICATION SECURITY SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 26 MANAGED ENDPOINT & APPLICATION SECURITY SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 27 MANAGED CLOUD SECURITY SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 28 MANAGED CLOUD SECURITY SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 29 MANAGED SECURITY OPERATIONS & MONITORING SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 30 MANAGED SECURITY OPERATIONS & MONITORING SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 31 MANAGED ADVANCED THREAT DETECTION SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 32 MANAGED ADVANCED THREAT DETECTION SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 33 MANAGED OFFENSIVE SECURITY & ASSESSMENT SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 34 MANAGED OFFENSIVE SECURITY & ASSESSMENT SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 35 MANAGED IDENTITY & DATA PROTECTION SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 36 MANAGED IDENTITY & DATA PROTECTION SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 37 MANAGED RISK & COMPLIANCE MANAGEMENT SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 38 MANAGED RISK & COMPLIANCE MANAGEMENT SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 39 MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 40 MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 41 FULLY MANAGED SECURITY SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 42 FULLY MANAGED SECURITY SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 43 CO-MANAGED SECURITY SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 44 CO-MANAGED SECURITY SERVICES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 45 MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 46 MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 47 LARGE ENTERPRISES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 48 LARGE ENTERPRISES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
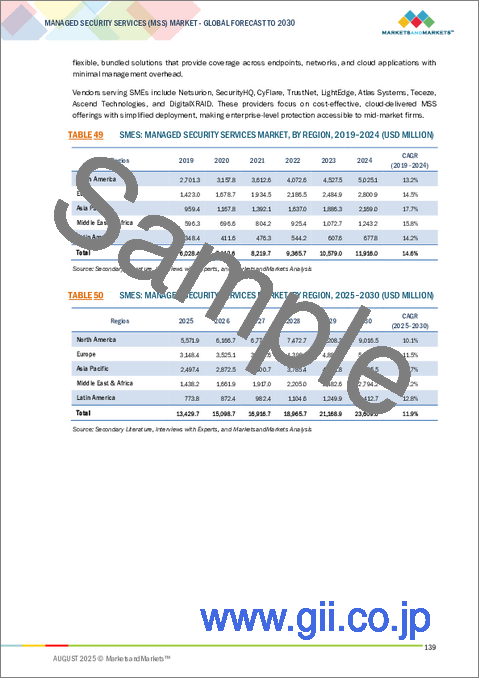
- TABLE 49 SMES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 50 SMES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 51 MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 52 MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 53 BFSI: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 54 BFSI: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 55 GOVERNMENT: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 56 GOVERNMENT: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 57 HEALTHCARE & LIFE SCIENCES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 58 HEALTHCARE & LIFE SCIENCES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 59 TELECOMMUNICATIONS: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 60 TELECOMMUNICATIONS: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 61 IT & ITES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 62 IT & ITES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 63 RETAIL & ECOMMERCE: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 64 RETAIL & ECOMMERCE: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 65 ENERGY & UTILITIES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 66 ENERGY & UTILITIES: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 67 MANUFACTURING: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 68 MANUFACTURING: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 69 OTHER VERTICALS: MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 70 OTHER VERTICALS: MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 71 MANAGED SECURITY SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 72 MANAGED SECURITY SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 73 NORTH AMERICA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 74 NORTH AMERICA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 75 NORTH AMERICA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 76 NORTH AMERICA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 77 NORTH AMERICA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 78 NORTH AMERICA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 79 NORTH AMERICA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 80 NORTH AMERICA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 81 NORTH AMERICA: MANAGED SECURITY SERVICES MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 82 NORTH AMERICA: MANAGED SECURITY SERVICES MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 83 US: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 84 US: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 85 US: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 86 US: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 87 US: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 88 US: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 89 US: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 90 US: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 91 CANADA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 92 CANADA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 93 CANADA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 94 CANADA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 95 CANADA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 96 CANADA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 97 CANADA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 98 CANADA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 99 EUROPE: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 100 EUROPE: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 101 EUROPE: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 102 EUROPE: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 103 EUROPE: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 104 EUROPE: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 105 EUROPE: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 106 EUROPE: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 107 EUROPE: MANAGED SECURITY SERVICES MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 108 EUROPE: MANAGED SECURITY SERVICES MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 109 UK: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 110 UK: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 111 UK: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 112 UK: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 113 UK: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 114 UK: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 115 UK: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 116 UK: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 117 GERMANY: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 118 GERMANY: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 119 GERMANY: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 120 GERMANY: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 121 GERMANY: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 122 GERMANY: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 123 GERMANY: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 124 GERMANY: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 125 FRANCE: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 126 FRANCE: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 127 FRANCE: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 128 FRANCE: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 129 FRANCE: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 130 FRANCE: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 131 FRANCE: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 132 FRANCE: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 133 ITALY: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 134 ITALY: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 135 ITALY: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 136 ITALY: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 137 ITALY: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 138 ITALY: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 139 ITALY: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 140 ITALY: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 141 RUSSIA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 142 RUSSIA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 143 RUSSIA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 144 RUSSIA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 145 RUSSIA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 146 RUSSIA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 147 RUSSIA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 148 RUSSIA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 149 ASIA PACIFIC: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 150 ASIA PACIFIC: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 151 ASIA PACIFIC: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 152 ASIA PACIFIC: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 153 ASIA PACIFIC: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 154 ASIA PACIFIC: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 155 ASIA PACIFIC: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 156 ASIA PACIFIC: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 157 ASIA PACIFIC: MANAGED SECURITY SERVICES MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 158 ASIA PACIFIC: MANAGED SECURITY SERVICES MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 159 CHINA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 160 CHINA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 161 CHINA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 162 CHINA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 163 CHINA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 164 CHINA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 165 CHINA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 166 CHINA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 167 JAPAN: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 168 JAPAN: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 169 JAPAN: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 170 JAPAN: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 171 JAPAN: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 172 JAPAN: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 173 JAPAN: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 174 JAPAN: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 175 INDIA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 176 INDIA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 177 INDIA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 178 INDIA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 179 INDIA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 180 INDIA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 181 INDIA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 182 INDIA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 183 AUSTRALIA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 184 AUSTRALIA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 185 AUSTRALIA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 186 AUSTRALIA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 187 AUSTRALIA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 188 AUSTRALIA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 189 AUSTRALIA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 190 AUSTRALIA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 191 SINGAPORE: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 192 SINGAPORE: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 193 SINGAPORE: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 194 SINGAPORE: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 195 SINGAPORE: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 196 SINGAPORE: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 197 SINGAPORE: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 198 SINGAPORE: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 199 MALAYSIA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 200 MALAYSIA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 201 MALAYSIA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 202 MALAYSIA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 203 MALAYSIA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 204 MALAYSIA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 205 MALAYSIA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 206 MALAYSIA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 207 INDONESIA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 208 INDONESIA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 209 INDONESIA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 210 INDONESIA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 211 INDONESIA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 212 INDONESIA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 213 INDONESIA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 214 INDONESIA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 215 THAILAND: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 216 THAILAND: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 217 THAILAND: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 218 THAILAND: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 219 THAILAND: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 220 THAILAND: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 221 THAILAND: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 222 THAILAND: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 223 PHILIPPINES: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 224 PHILIPPINES: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 225 PHILIPPINES: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 226 PHILIPPINES: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 227 PHILIPPINES: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 228 PHILIPPINES: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 229 PHILIPPINES: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 230 PHILIPPINES: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 231 MIDDLE EAST & AFRICA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 232 MIDDLE EAST & AFRICA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 233 MIDDLE EAST & AFRICA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 234 MIDDLE EAST & AFRICA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 235 MIDDLE EAST & AFRICA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 236 MIDDLE EAST & AFRICA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 237 MIDDLE EAST & AFRICA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 238 MIDDLE EAST & AFRICA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 239 MIDDLE EAST & AFRICA: MANAGED SECURITY SERVICES MARKET, BY SUB-REGION, 2019-2024 (USD MILLION)
- TABLE 240 MIDDLE EAST & AFRICA: MANAGED SECURITY SERVICES MARKET, BY SUB-REGION, 2025-2030 (USD MILLION)
- TABLE 241 MIDDLE EAST: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 242 MIDDLE EAST: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 243 MIDDLE EAST: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 244 MIDDLE EAST: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 245 MIDDLE EAST: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 246 MIDDLE EAST: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 247 MIDDLE EAST: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 248 MIDDLE EAST: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 249 MIDDLE EAST: MANAGED SECURITY SERVICES MARKET, BY SUB-REGION, 2019-2024 (USD MILLION)
- TABLE 250 MIDDLE EAST: MANAGED SECURITY SERVICES MARKET, BY SUB-REGION, 2025-2030 (USD MILLION)
- TABLE 251 GCC COUNTRIES: MANAGED SECURITY SERVICES MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 252 GCC COUNTRIES: MANAGED SECURITY SERVICES MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 253 AFRICA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 254 AFRICA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 255 AFRICA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 256 AFRICA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 257 AFRICA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 258 AFRICA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 259 AFRICA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 260 AFRICA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 261 LATIN AMERICA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 262 LATIN AMERICA: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 263 LATIN AMERICA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 264 LATIN AMERICA: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 265 LATIN AMERICA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 266 LATIN AMERICA: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 267 LATIN AMERICA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 268 LATIN AMERICA: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 269 LATIN AMERICA: MANAGED SECURITY SERVICES MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 270 LATIN AMERICA: MANAGED SECURITY SERVICES MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 271 BRAZIL: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 272 BRAZIL: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 273 BRAZIL: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 274 BRAZIL: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 275 BRAZIL: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 276 BRAZIL: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 277 BRAZIL: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 278 BRAZIL: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 279 MEXICO: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2019-2024 (USD MILLION)
- TABLE 280 MEXICO: MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE, 2025-2030 (USD MILLION)
- TABLE 281 MEXICO: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 282 MEXICO: MANAGED SECURITY SERVICES MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 283 MEXICO: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 284 MEXICO: MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 285 MEXICO: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 286 MEXICO: MANAGED SECURITY SERVICES MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 287 OVERVIEW OF STRATEGIES ADOPTED BY KEY MANAGED SECURITY SERVICES VENDORS
- TABLE 288 MANAGED SECURITY SERVICES MARKET: DEGREE OF COMPETITION
- TABLE 289 MANAGED SECURITY SERVICES MARKET: REGIONAL FOOTPRINT
- TABLE 290 MANAGED SECURITY SERVICES MARKET: TYPE FOOTPRINT
- TABLE 291 MANAGED SECURITY SERVICES MARKET: VERTICAL FOOTPRINT
- TABLE 292 MANAGED SECURITY SERVICES MARKET: KEY STARTUPS/SMES
- TABLE 293 MANAGED SECURITY SERVICES MARKET: COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES
- TABLE 294 MANAGED SECURITY SERVICES MARKET: PRODUCT LAUNCHES & DEVELOPMENTS, JANUARY 2023-JULY 2025
- TABLE 295 MANAGED SECURITY SERVICES MARKET: DEALS, JANUARY 2023-JULY 2025
- TABLE 296 IBM: COMPANY OVERVIEW
- TABLE 297 IBM: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 298 IBM: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 299 IBM: DEALS, JANUARY 2023-JUNE 2025
- TABLE 300 NTT: COMPANY OVERVIEW
- TABLE 301 NTT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 302 NTT: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 303 NTT: DEALS, JANUARY 2023-JUNE 2025
- TABLE 304 LEVELBLUE: COMPANY OVERVIEW
- TABLE 305 LEVELBLUE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 306 LEVELBLUE: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 307 ACCENTURE: COMPANY OVERVIEW
- TABLE 308 ACCENTURE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 309 ACCENTURE: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 310 ACCENTURE: DEALS, JANUARY 2023-JUNE 2025
- TABLE 311 ACCENTURE: EXPANSIONS, JANUARY 2023-JUNE 2025
- TABLE 312 DXC TECHNOLOGY: COMPANY OVERVIEW
- TABLE 313 DXC TECHNOLOGY: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 314 DXC TECHNOLOGY: DEALS, JANUARY 2023-JUNE 2025
- TABLE 315 SECNAP: COMPANY OVERVIEW
- TABLE 316 SECNAP: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 317 SECNAP: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 318 SECNAP: DEALS, JANUARY 2023-JUNE 2025
- TABLE 319 DELOITTE: COMPANY OVERVIEW
- TABLE 320 DELOITTE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 321 DELOITTE: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 322 DELOITTE: DEALS, JANUARY 2023-JUNE 2025
- TABLE 323 DELOITTE: EXPANSIONS, JANUARY 2023-JUNE 2025
- TABLE 324 SECUREWORKS: COMPANY OVERVIEW
- TABLE 325 SECUREWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 326 SECUREWORKS: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 327 SECUREWORKS: DEALS, JANUARY 2023-JUNE 2025
- TABLE 328 SECUREWORKS: EXPANSIONS, JANUARY 2023-JUNE 2025
- TABLE 329 TRUSTWAVE: COMPANY OVERVIEW
- TABLE 330 TRUSTWAVE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 331 TRUSTWAVE: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 332 TRUSTWAVE: DEALS, JANUARY 2023-JUNE 2025
- TABLE 333 VERIZON: COMPANY OVERVIEW
- TABLE 334 VERIZON: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 335 VERIZON: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 336 VERIZON: DEALS, JANUARY 2023-JUNE 2025
- TABLE 337 FUJITSU: COMPANY OVERVIEW
- TABLE 338 FUJITSU: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 339 FUJITSU: DEALS, JANUARY 2023-JUNE 2025
- TABLE 340 FUJITSU: EXPANSIONS, JANUARY 2023-JUNE 2025
- TABLE 341 HPE: COMPANY OVERVIEW
- TABLE 342 HPE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 343 HPE: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 344 HPE: DEALS, JANUARY 2023-JUNE 2025
- TABLE 345 TCS: COMPANY OVERVIEW
- TABLE 346 TCS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 347 TCS: DEALS, JANUARY 2023-JUNE 2025
- TABLE 348 ATOS: COMPANY OVERVIEW
- TABLE 349 ATOS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 350 ATOS: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 351 ATOS: DEALS, JANUARY 2023-JUNE 2025
- TABLE 352 ORANGE CYBERDEFENSE: COMPANY OVERVIEW
- TABLE 353 ORANGE CYBERDEFENSE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 354 ORANGE CYBERDEFENSE: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 355 ORANGE CYBERDEFENSE: DEALS, JANUARY 2023-JUNE 2025
- TABLE 356 RAPID7: COMPANY OVERVIEW
- TABLE 357 RAPID7: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 358 RAPID7: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 359 RAPID7: DEALS, JANUARY 2023-JUNE 2025
- TABLE 360 RAPID7: EXPANSIONS, JANUARY 2023-JUNE 2025
- TABLE 361 TREND MICRO: COMPANY OVERVIEW
- TABLE 362 TREND MICRO: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 363 TREND MICRO: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 364 TREND MICRO: DEALS, JANUARY 2023-JUNE 2025
- TABLE 365 TREND MICRO: EXPANSIONS, JANUARY 2023-JUNE 2025
- TABLE 366 KUDELSKI SECURITY: COMPANY OVERVIEW
- TABLE 367 KUDELSKI SECURITY: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 368 KUDELSKI SECURITY: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 369 KUDELSKI SECURITY: DEALS, JANUARY 2023-JUNE 2025
- TABLE 370 CROWDSTRIKE: COMPANY OVERVIEW
- TABLE 371 CROWDSTRIKE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 372 CROWDSTRIKE: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 373 CROWDSTRIKE: DEALS, JANUARY 2023-JUNE 2025
- TABLE 374 CROWDSTRIKE: EXPANSIONS, JANUARY 2023-JUNE 2025
- TABLE 375 F5: COMPANY OVERVIEW
- TABLE 376 F5: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 377 F5: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 378 F5: DEALS, JANUARY 2023-JUNE 2025
- TABLE 379 CAPGEMINI: COMPANY OVERVIEW
- TABLE 380 CAPGEMINI: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 381 INFOSYS: COMPANY OVERVIEW
- TABLE 382 INFOSYS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 383 INFOSYS: DEALS, JANUARY 2023-JUNE 2025
- TABLE 384 LUMEN TECHNOLOGIES: COMPANY OVERVIEW
- TABLE 385 LUMEN TECHNOLOGIES: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 386 LUMEN TECHNOLOGIES: PRODUCT LAUNCHES/DEVELOPMENTS, JANUARY 2023-JUNE 2025
- TABLE 387 LUMEN TECHNOLOGIES: DEALS, JANUARY 2023-JUNE 2025
- TABLE 388 LUMEN TECHNOLOGIES: EXPANSIONS, JANUARY 2023-JUNE 2025
- TABLE 389 KROLL: COMPANY OVERVIEW
- TABLE 390 KROLL: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 391 KROLL: DEALS, JANUARY 2023-JUNE 2025
- TABLE 392 KROLL: EXPANSIONS, JANUARY 2023-JUNE 2025
- TABLE 393 ADJACENT MARKETS AND FORECASTS
- TABLE 394 CYBERSECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 395 CYBERSECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 396 CYBERSECURITY MARKET, BY SOLUTION TYPE, 2019-2024 (USD MILLION)
- TABLE 397 CYBERSECURITY MARKET, BY SOLUTION TYPE, 2025-2030 (USD MILLION)
- TABLE 398 CYBERSECURITY MARKET, BY SECURITY TYPE, 2019-2024 (USD MILLION)
- TABLE 399 CYBERSECURITY MARKET, BY SECURITY TYPE, 2025-2030 (USD MILLION)
- TABLE 400 CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 401 CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 402 CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 403 CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 404 CYBERSECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 405 CYBERSECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 406 CYBERSECURITY MARKET, BY REGION, 2019-2024 (USD BILLION)
- TABLE 407 CYBERSECURITY MARKET, BY REGION, 2025-2030 (USD BILLION)
- TABLE 408 SOC-AS-A-SERVICE MARKET, BY SERVICE TYPE, 2018-2023 (USD MILLION)
- TABLE 409 SOC-AS-A-SERVICE MARKET, BY SERVICE TYPE, 2024-2030 (USD MILLION)
- TABLE 410 SOC-AS-A-SERVICE MARKET, BY OFFERING, 2018-2023 (USD MILLION)
- TABLE 411 SOC-AS-A-SERVICE MARKET, BY OFFERING, 2024-2030 (USD MILLION)
- TABLE 412 SOC-AS-A-SERVICE MARKET, BY ORGANIZATION SIZE, 2018-2023 (USD MILLION)
- TABLE 413 SOC-AS-A-SERVICE MARKET, BY ORGANIZATION SIZE, 2024-2030 (USD MILLION)
- TABLE 414 SOC-AS-A-SERVICE MARKET, BY SECURITY TYPE, 2018-2023 (USD MILLION)
- TABLE 415 SOC-AS-A-SERVICE MARKET, BY SECURITY TYPE, 2024-2030 (USD MILLION)
- TABLE 416 SOC-AS-A-SERVICE MARKET, BY SECTOR, 2018-2023 (USD MILLION)
- TABLE 417 SOC-AS-A-SERVICE MARKET, BY SECTOR, 2024-2030 (USD MILLION)
- TABLE 418 SOC-AS-A-SERVICE MARKET, BY VERTICAL, 2018-2023 (USD MILLION)
- TABLE 419 SOC-AS-A-SERVICE MARKET, BY VERTICAL, 2024-2030 (USD MILLION)
- TABLE 420 SOC-AS-A-SERVICE MARKET, BY REGION, 2018-2023 (USD MILLION)
- TABLE 421 SOC-AS-A-SERVICE MARKET, BY REGION, 2024-2030 (USD MILLION)
List of Figures
- FIGURE 1 MANAGED SECURITY SERVICES MARKET: RESEARCH DESIGN
- FIGURE 2 RESEARCH FLOW
- FIGURE 3 APPROACH 1 (SUPPLY SIDE): REVENUE FROM SOLUTIONS AND SERVICES OF MANAGED SECURITY SERVICES VENDORS
- FIGURE 4 APPROACH 2: BOTTOM-UP (DEMAND SIDE): MANAGED SECURITY SERVICES MARKET
- FIGURE 5 TOP-DOWN AND BOTTOM-UP APPROACHES
- FIGURE 6 MANAGED SECURITY SERVICES MARKET: DATA TRIANGULATION
- FIGURE 7 MANAGED SECURITY SERVICES MARKET: SEGMENTAL SNAPSHOT
- FIGURE 8 MANAGED SECURITY SERVICES MARKET: REGIONAL SNAPSHOT
- FIGURE 9 INCREASED SECURITY BREACHES AND SOPHISTICATED CYBERATTACKS TO DRIVE MANAGED SECURITY SERVICES MARKET
- FIGURE 10 MANAGED ENDPOINT & APPLICATION SECURITY SERVICES SEGMENT TO ACCOUNT FOR LARGEST MARKET BY 2030
- FIGURE 11 FULLY MANAGED SECURITY SERVICE TYPE SEGMENT TO LEAD MARKET DURING FORECAST PERIOD
- FIGURE 12 SMES SEGMENT TO RECORD HIGHER CAGR DURING FORECAST PERIOD
- FIGURE 13 BFSI SEGMENT TO ACCOUNT FOR LARGEST MARKET DURING FORECAST PERIOD
- FIGURE 14 NORTH AMERICA TO ACCOUNT FOR LARGEST MARKET DURING FORECAST PERIOD
- FIGURE 15 ASIA PACIFIC TO EMERGE AS LUCRATIVE MARKET FOR INVESTMENTS IN NEXT FIVE YEARS
- FIGURE 16 MANAGED SECURITY SERVICES MARKET: MARKET DYNAMICS
- FIGURE 17 DETECTED SECURITY INCIDENTS OVER A 24-HOUR PERIOD
- FIGURE 18 GLOBAL CYBERSECURITY WORKFORCE GAP (2015-2024)
- FIGURE 19 MANAGED SECURITY SERVICES MARKET: VALUE CHAIN ANALYSIS
- FIGURE 20 MANAGED SECURITY SERVICES MARKET ECOSYSTEM
- FIGURE 21 POTENTIAL OF GENERATIVE AI IN MANAGED SECURITY SERVICES MARKET ACROSS INDUSTRIES
- FIGURE 22 IMPACT OF GENERATIVE AI/AI ON INTERCONNECTED AND ADJACENT ECOSYSTEMS
- FIGURE 23 MANAGED SECURITY SERVICES MARKET: PORTER'S FIVE FORCES ANALYSIS
- FIGURE 24 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS
- FIGURE 25 KEY BUYING CRITERIA FOR TOP THREE VERTICALS
- FIGURE 26 AVERAGE SELLING PRICE OFFERED BY KEY PLAYERS, BY TYPE, 2024
- FIGURE 27 NUMBER OF PATENTS GRANTED FOR MANAGED SECURITY SERVICES MARKET, 2015-2025
- FIGURE 28 REGIONAL ANALYSIS OF PATENTS GRANTED FOR MANAGED SECURITY SERVICES MARKET
- FIGURE 29 MANAGED SECURITY SERVICES MARKET: TRENDS/DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- FIGURE 30 NUMBER OF INVESTORS AND FUNDING ROUNDS BY LEADING GLOBAL MANAGED SECURITY SERVICES STARTUPS AND SMES, 2021-2025
- FIGURE 31 MANAGED ENDPOINT & APPLICATION SECURITY SERVICES SEGMENT TO ACCOUNT FOR LARGEST SHARE BY 2030
- FIGURE 32 FULLY MANAGED SECURITY SERVICES SEGMENT TO GROW AT HIGHER CAGR DURING FORECAST PERIOD
- FIGURE 33 SMES SEGMENT TO RECORD HIGHER CAGR DURING FORECAST PERIOD
- FIGURE 34 HEALTHCARE & LIFE SCIENCES SEGMENT TO RECORD HIGHEST GROWTH DURING FORECAST PERIOD
- FIGURE 35 ASIA PACIFIC TO REGISTER HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 36 NORTH AMERICA: MANAGED SECURITY SERVICES MARKET SNAPSHOT
- FIGURE 37 ASIA PACIFIC: MANAGED SECURITY SERVICES MARKET SNAPSHOT
- FIGURE 38 REVENUE ANALYSIS OF TOP FIVE PLAYERS, 2020-2024 (USD MILLION)
- FIGURE 39 MANAGED SECURITY SERVICES MARKET: SHARE OF LEADING COMPANIES, 2024
- FIGURE 40 MANAGED SECURITY SERVICES MARKET: COMPARISON OF VENDOR BRANDS
- FIGURE 41 MANAGED SECURITY SERVICES MARKET: COMPANY VALUATION OF KEY VENDORS (USD BILLION), 2025
- FIGURE 42 MANAGED SECURITY SERVICES MARKET: FINANCIAL METRICS OF KEY VENDORS, 2025
- FIGURE 43 MANAGED SECURITY SERVICES MARKET: COMPANY EVALUATION MATRIX (KEY PLAYERS), 2024
- FIGURE 44 MANAGED SECURITY SERVICES MARKET: COMPANY FOOTPRINT
- FIGURE 45 MANAGED SECURITY SERVICES MARKET: COMPANY EVALUATION MATRIX (STARTUPS/SMES), 2024
- FIGURE 46 IBM: COMPANY SNAPSHOT
- FIGURE 47 NTT: COMPANY SNAPSHOT
- FIGURE 48 ACCENTURE: COMPANY SNAPSHOT
- FIGURE 49 DXC TECHNOLOGY: COMPANY SNAPSHOT
- FIGURE 50 SECUREWORKS: COMPANY SNAPSHOT
- FIGURE 51 VERIZON: COMPANY SNAPSHOT
- FIGURE 52 FUJITSU: COMPANY SNAPSHOT
- FIGURE 53 HPE: COMPANY SNAPSHOT
- FIGURE 54 TCS: COMPANY SNAPSHOT
- FIGURE 55 ATOS: COMPANY SNAPSHOT
- FIGURE 56 RAPID7: COMPANY SNAPSHOT
- FIGURE 57 TREND MICRO: COMPANY SNAPSHOT
- FIGURE 58 KUDELSKI SECURITY: COMPANY SNAPSHOT
- FIGURE 59 CROWDSTRIKE: COMPANY SNAPSHOT
- FIGURE 60 F5: COMPANY SNAPSHOT
- FIGURE 61 CAPGEMINI: COMPANY SNAPSHOT
- FIGURE 62 INFOSYS: COMPANY SNAPSHOT
- FIGURE 63 LUMEN TECHNOLOGIES: COMPANY SNAPSHOT
The global managed security services (MSS) market size is projected to grow from 39.47 billion in 2025 to USD 66.83 billion by 2030 at a compound annual growth rate (CAGR) of 11.1% during the forecast period.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | Value (USD Million/USD Billion) |
| Segments | By Service Type, Type, Organization size, Vertical, and Region |
| Regions covered | North America, Europe, Asia Pacific, Middle East & Africa, and Latin America |
This growth is driven by the rising complexity of cyber threats, increasing cloud and hybrid infrastructure adoption, and the urgent need for 24/7 expert-led monitoring and incident response. Organizations are turning to MSS providers to bridge internal skill gaps, reduce operational overhead, and ensure consistent security across distributed environments.

However, market growth is restrained by data sovereignty concerns, integration issues with legacy systems, potential vendor lock-in, and the lack of visibility and control in outsourced security operations. Despite these concerns, the growing need for scalable, outcome-based cybersecurity solutions is fueling MSS adoption across the BFSI, healthcare, government, manufacturing, and critical infrastructure sectors.
"By type, the co-managed security services segment accounts for the highest CAGR during the forecast period"
The co-managed security services segment is witnessing rapid growth in the market as organizations increasingly seek a balanced approach between internal control and external expertise. With rising cyber threats and growing IT complexity, many enterprises are turning to co-managed models to strengthen their security posture without fully outsourcing critical operations. This approach allows in-house teams to work alongside managed security service providers (MSSPs) to ensure 24/7 monitoring, faster incident response, and continuous compliance support.
"By organization size, the SMEs segment is expected to register the highest CAGR during the forecast period"
SMEs are rapidly becoming prominent adopters of MSS due to the growing frequency of cyberattacks targeting smaller organizations with limited internal security capabilities. As digital transformation accelerates across the SME landscape, many are adopting cloud, mobile, and hybrid IT environments, which significantly expand their attack surfaces. However, constrained cybersecurity budgets and a lack of skilled resources often make it challenging for SMEs to build robust in-house security operations.
MSSPs offer an ideal solution by providing cost-effective, subscription-based access to advanced threat detection, continuous monitoring, and incident response capabilities. Rising awareness of regulatory compliance obligations, increasing risks of ransomware attacks, and the need for business continuity are prompting SMEs to invest in MSS offerings such as SOC-as-a-Service, SIEM-as-a-Service, and MDR. MSS's flexibility, scalability, and affordability make it particularly attractive to SMEs seeking to strengthen their security posture while focusing on core business operations.
"North America to hold the largest market share, while Asia Pacific is expected to witness the fastest growth during the forecast period"
North America continues to dominate the managed security services landscape due to its high concentration of digitally mature enterprises, increasing cyber threat exposure, and strong regulatory and compliance frameworks. In the US and Canada, organizations across industries face growing challenges in managing complex IT environments and addressing the persistent shortage of skilled cybersecurity professionals. This has led to a surge in demand for managed security services that offer 24/7 monitoring, threat detection, incident response, and compliance support.
Meanwhile, the Asia Pacific (APAC) region is projected to grow at the highest CAGR during the forecast period. This growth is fueled by rapid digitalization, expanding cloud adoption, and increasing cyber incidents across emerging economies such as India, China, and Southeast Asia. Many SMEs and mid-sized enterprises in the region are turning to MSSPs to access affordable, scalable cybersecurity solutions without investing heavily in internal infrastructure. Government initiatives to strengthen national cybersecurity postures and compliance enforcement are further accelerating MSS adoption across APAC.
Breakdown of primaries
The study contains insights from various industry experts, from component suppliers to Tier 1 companies and OEMs. The break-up of the primaries is as follows:
- By Company Type: Tier 1 - 35%, Tier 2 - 45%, and Tier 3 - 20%
- By Designation: C-level - 40%, Managerial & Other Levels - 60%
- By Region: North America - 40%, Europe - 25%, Asia Pacific - 35%
The key players in the MSS market include IBM (US), NTT (Japan), LevelBlue (US), Accenture (Ireland), DXC Technology (US), Secnap (US), Deloitte (US), Secureworks (US), Trustwave (US), Verizon (US), Fujitsu (Japan), HPE (US), TCS (India), Atos (France), Orange Cyberdefense (France), Rapid7 (US), TrendMicro (Japan), Kudelski Security (Switzerland), CrowdStrike (US), F5 (US), Capgemini (France), Infosys (India), Lumen (US), Kroll (US), Netsurion (US), Atlas Systems (US), Cipher (US), RSI Security (US), SecurityHQ (UK), Lightedge (US), LRQA (UK), Teceze (UK), CyFlare (US), Ascend Technologies (US), Avertium (US), DigitalXRAID (UK), and TrustNet (US). The study includes an in-depth competitive analysis of the key players in the MSS market, their company profiles, recent developments, and key market strategies.
Research Coverage
The report segments the MSS market and forecasts its size by service type (managed network & perimeter security services, managed endpoint & application security services, managed cloud security services, managed security operations & monitoring services, managed advanced threat detection services, managed offensive security & assessment services, managed identity and data protection services), by type (fully managed security services, co-managed security services), by organization size (large enterprises, and small and medium sized enterprises (SMEs)), by vertical (banking, financial services, and insurance (BFSI), government, retail & ecommerce, healthcare & life sciences, IT & ITeS, telecommunications, energy & utilities, manufacturing, other verticals (education, travel & hospitality, media & entertainment) and by region (North America, Europe, Asia Pacific, Middle East & Africa, and Latin America).
The study also includes an in-depth competitive analysis of the market's key players, their company profiles, key observations related to product and business offerings, recent developments, and key market strategies.
Key Benefits of Buying the Report
The report will help market leaders and new entrants with information on the closest approximations of the revenue numbers for the overall MSS market and the subsegments. It will also help stakeholders understand the competitive landscape and gain more insights to better position their businesses and plan suitable go-to-market strategies. The report also helps stakeholders understand the market pulse and provides information on key market drivers, restraints, challenges, and opportunities.
The report provides insights into the following pointers:
- Analysis of key drivers (Increasing need for 24/7 security monitoring and incident response, Intensifying complexity of cyber threats, Evolving regulatory landscape and stringent government regulations, Surge in cloud adoption and prevalence of hybrid environments), restraints (Lack of visibility and control over outsourced security functions, Limited capabilities for threat-hunting and incident-response services, Enterprises' reluctance to outsource operations), opportunities (Emergence of industry-specific MSS offerings, Growing adoption of cloud technology and IoT devices, Rising demand for advanced cybersecurity measures), and challenges (Balancing scalability with operational efficiency, Rising cyberattacks on infrastructure of managed security service providers, Shortage of security professionals, Limited capital funding in emerging economies)
- Product Development/Innovation: Detailed insights on upcoming technologies, research & development activities, and new product & service launches in the MSS market
- Market Development: Comprehensive information about lucrative markets - analysis of the MSS market across varied regions
- Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the MSS market
- Competitive Assessment: In-depth assessment of market shares, growth strategies, and service offerings of leading players such as IBM (US), NTT (Japan), LevelBlue (US), Accenture (Ireland), DXC Technology (US), Secnap (US), Deloitte (US), Secureworks (US), Trustwave (US), Verizon (US), Fujitsu (Japan), HPE (US), TCS (India), Atos (France), Orange Cyberdefense (France), Rapid7 (US), TrendMicro (Japan), Kudelski Security (Switzerland), CrowdStrike (US), F5 (US), Capgemini (France), Infosys (India), Lumen (US), Kroll (US), Netsurion (US), Atlas Systems (US), Cipher (US), RSI Security (US), SecurityHQ (UK), Lightedge (US), LRQA (UK), Teceze (UK), CyFlare (US), Ascend Technologies (US), Avertium (US), DigitalXRAID (UK), and TrustNet (US)
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.3 STUDY SCOPE
- 1.3.1 MARKET SEGMENTATION AND REGIONAL SCOPE
- 1.3.2 INCLUSIONS AND EXCLUSIONS
- 1.4 YEARS CONSIDERED
- 1.5 CURRENCY CONSIDERED
- 1.6 STAKEHOLDERS
- 1.7 SUMMARY OF CHANGES
2 RESEARCH METHODOLOGY
- 2.1 RESEARCH DATA
- 2.1.1 SECONDARY DATA
- 2.1.2 PRIMARY DATA
- 2.1.2.1 Breakup of primary interviews
- 2.1.2.2 Key insights from industry experts
- 2.2 MARKET SIZE ESTIMATION
- 2.2.1 TOP-DOWN APPROACH
- 2.2.2 BOTTOM-UP APPROACH
- 2.3 DATA TRIANGULATION
- 2.4 MARKET FORECAST
- 2.5 RESEARCH ASSUMPTIONS
- 2.6 RESEARCH LIMITATIONS
3 EXECUTIVE SUMMARY
4 PREMIUM INSIGHTS
- 4.1 ATTRACTIVE OPPORTUNITIES FOR PLAYERS IN MANAGED SECURITY SERVICES MARKET
- 4.2 MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE
- 4.3 MANAGED SECURITY SERVICES MARKET, BY TYPE
- 4.4 MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE
- 4.5 MANAGED SECURITY SERVICES MARKET, BY VERTICAL
- 4.6 MANAGED SECURITY SERVICES MARKET, BY REGION
- 4.7 MARKET INVESTMENT SCENARIO
5 MARKET OVERVIEW AND INDUSTRY TRENDS (STRATEGIC DRIVERS WITH QUANTITATIVE IMPLICATIONS)
Unpacking the Forces Shaping Managed Security Services (MSS) Adoption & Future Growth Opportunities
- 5.1 INTRODUCTION
- 5.2 MARKET DYNAMICS
- 5.2.1 DRIVERS
- 5.2.1.1 Increasing need for continuous security monitoring and incident response
- 5.2.1.2 Intensifying complexity of cyber threats
- 5.2.1.3 Evolving regulatory landscape and stringent government regulations
- 5.2.1.4 Surge in cloud adoption and prevalence of hybrid environments
- 5.2.2 RESTRAINTS
- 5.2.2.1 Lack of visibility and control over outsourced security functions
- 5.2.2.2 Limited capabilities for threat-hunting and incident-response services
- 5.2.2.3 Reluctance of enterprises to outsource operations
- 5.2.3 OPPORTUNITIES
- 5.2.3.1 Emergence of industry-specific MSS offerings
- 5.2.3.2 Growing adoption of cloud technology and IoT devices
- 5.2.3.3 Rising demand for advanced cybersecurity measures
- 5.2.4 CHALLENGES
- 5.2.4.1 Balancing scalability with operational efficiency
- 5.2.4.2 Rising cyberattacks on infrastructure of managed security service providers
- 5.2.4.3 Shortage of security professionals
- 5.2.4.4 Limited capital funding in emerging economies
- 5.2.1 DRIVERS
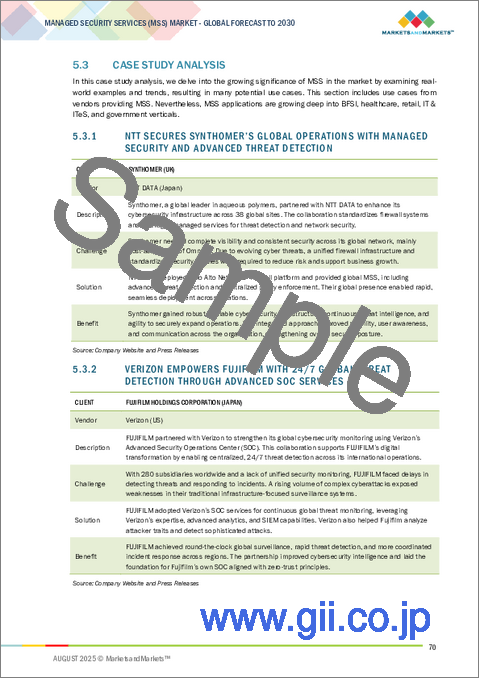
- 5.3 CASE STUDY ANALYSIS
- 5.3.1 NTT SECURES SYNTHOMER'S GLOBAL OPERATIONS WITH MANAGED SECURITY AND ADVANCED THREAT DETECTION
- 5.3.2 VERIZON EMPOWERS FUJIFILM WITH 24/7 GLOBAL THREAT DETECTION THROUGH ADVANCED SOC SERVICES
- 5.3.3 DXC TECHNOLOGY HELPED INAIL ENCOUNTER CYBER THREATS WITH AUTOMATION AND ML
- 5.3.4 LUMEN TECHNOLOGIES HELPED NET PROTECTIONS SECURE ITS NETWORK
- 5.3.5 TRUSTWAVE HELPED AUGMEDIX PROTECT VITAL HEALTHCARE INFORMATION
- 5.4 VALUE CHAIN ANALYSIS
- 5.4.1 ASSESSING SECURITY & ARCHITECTURE PLANNING
- 5.4.2 SERVICE DESIGN & OFFERING
- 5.4.3 CHANNEL PARTNERS/MSS DISTRIBUTORS
- 5.4.4 END USER GROUP
- 5.4.5 SECURITY MONITORING & THREAT DETECTION
- 5.4.6 INCIDENT RESPONSE
- 5.4.7 MEASURES FOR REMEDIATION
- 5.5 ECOSYSTEM ANALYSIS
- 5.6 IMPACT OF GENERATIVE AI ON MANAGED SECURITY SERVICES MARKET
- 5.6.1 GENERATIVE AI
- 5.6.2 TOP USE CASES AND MARKET POTENTIAL IN MANAGED SECURITY SERVICES MARKET
- 5.6.3 IMPACT OF GENERATIVE AI ON INTERCONNECTED AND ADJACENT ECOSYSTEMS
- 5.6.3.1 SIEM & XDR Platforms
- 5.6.3.2 Soar Systems
- 5.6.3.3 Cloud Security
- 5.6.3.4 Artificial Intelligence (AI)/Machine Learning (ML) Analytics
- 5.6.3.5 IoT & Managed Security Services
- 5.7 PORTER'S FIVE FORCES ANALYSIS
- 5.7.1 THREAT OF NEW ENTRANTS
- 5.7.2 THREAT OF SUBSTITUTES
- 5.7.3 BARGAINING POWER OF SUPPLIERS
- 5.7.4 BARGAINING POWER OF BUYERS
- 5.7.5 INTENSITY OF COMPETITIVE RIVALRY
- 5.8 KEY STAKEHOLDERS AND BUYING CRITERIA
- 5.8.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 5.8.2 BUYING CRITERIA
- 5.9 PRICING ANALYSIS
- 5.9.1 AVERAGE SELLING PRICE OFFERED BY KEY PLAYERS, BY TYPE, 2024
- 5.9.2 INDICATIVE PRICING ANALYSIS, 2024
- 5.10 TECHNOLOGY ANALYSIS
- 5.10.1 KEY TECHNOLOGIES
- 5.10.1.1 AI/ML and managed security services
- 5.10.1.2 Cloud-based security solutions
- 5.10.1.3 Security information and event management
- 5.10.1.4 Security orchestration, automation, and response
- 5.10.2 COMPLEMENTARY TECHNOLOGIES
- 5.10.2.1 Threat intelligence platforms
- 5.10.2.2 Identity threat detection and response
- 5.10.3 ADJACENT TECHNOLOGIES
- 5.10.3.1 Zero-trust architecture
- 5.10.3.2 IoT and managed security services
- 5.10.3.3 Extended and detection response
- 5.10.1 KEY TECHNOLOGIES
- 5.11 PATENT ANALYSIS
- 5.12 REGULATORY LANDSCAPE
- 5.12.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- 5.12.2 KEY REGULATIONS
- 5.12.2.1 Payment Card Industry Data Security Standard (PCI-DSS)
- 5.12.2.2 General Data Protection Regulation (GDPR)
- 5.12.2.3 California Consumer Privacy Act (CCPA)
- 5.12.2.4 Gramm-Leach-Bliley Act of 1999 (GLBA)
- 5.12.2.5 Personal Information Protection and Electronic Documents Act (PIPEDA)
- 5.12.2.6 Federal Information Security Management Act (FISMA)
- 5.12.2.7 Health Insurance Portability and Accountability Act (HIPAA)
- 5.12.2.8 Sarbanes-Oxley Act (SOX)
- 5.12.2.9 International Organization for Standardization (ISO) - Standard 27001
- 5.13 IMPACT OF 2025 US TARIFF - MANAGED SECURITY SERVICES MARKET
- 5.13.1 INTRODUCTION
- 5.13.2 KEY TARIFF RATES
- 5.13.3 PRICE IMPACT ANALYSIS
- 5.13.4 IMPACT ON COUNTRY/REGION
- 5.13.4.1 North America
- 5.13.4.2 Europe
- 5.13.4.3 Asia Pacific
- 5.13.5 IMPACT ON END-USE INDUSTRIES
- 5.14 TRENDS/DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- 5.15 MANAGED SECURITY SERVICES MARKET: BUSINESS MODELS
- 5.16 KEY CONFERENCES & EVENTS IN 2025
- 5.17 INVESTMENT AND FUNDING SCENARIO
6 MANAGED SECURITY SERVICES MARKET, BY SERVICE TYPE (MARKET SIZE & FORECAST TO 2030 - IN VALUE (USD))
Detailed breakdown of market share and growth across service type
- 6.1 INTRODUCTION
- 6.1.1 SERVICE TYPE: MANAGED SECURITY SERVICE MARKET DRIVERS
- 6.2 MANAGED NETWORK & PERIMETER SECURITY SERVICES
- 6.2.1 GROWING HYBRID AND MULTI-CLOUD ENVIRONMENTS TO DRIVE DEMAND FOR MANAGED NETWORK DEFENSE
- 6.2.2 MANAGED FIREWALL SERVICES
- 6.2.3 MANAGED INTRUSION DETECTION & PREVENTION SERVICES
- 6.2.4 MANAGED UNIFIED THREAT MANAGEMENT
- 6.2.5 MANAGED DISTRIBUTED DENIAL OF SERVICE PROTECTION
- 6.2.6 ASSET DISCOVERY & NETWORK SEGMENTATION
- 6.2.7 WEB AND DNS SECURITY GATEWAY SERVICES
- 6.3 MANAGED ENDPOINT & APPLICATION SECURITY SERVICES
- 6.3.1 INCREASING ENDPOINT PROLIFERATION AND SOPHISTICATED MALWARE TO FUEL DEMAND FOR ENDPOINT & APPLICATION SECURITY
- 6.3.2 MANAGED ENDPOINT DETECTION AND RESPONSE
- 6.3.3 MANAGED ANTI-MALWARE/ANTIVIRUS
- 6.3.4 PATCH MANAGEMENT-AS-A-SERVICE
- 6.3.5 APPLICATION WHITELISTING AND CONTROL
- 6.3.6 API SECURITY MONITORING & THREAT PROTECTION
- 6.3.7 OAUTH & SESSION TOKEN ABUSE DETECTION
- 6.3.8 CI/CD PIPELINE SECURITY MONITORING
- 6.3.9 MANAGED BACKUP & IMMUTABLE STORAGE
- 6.4 MANAGED CLOUD SECURITY SERVICES
- 6.4.1 CLOUD MIGRATION AND SHARED RESPONSIBILITY CHALLENGES TO ACCELERATE ADOPTION OF MANAGED CLOUD SECURITY
- 6.4.2 MANAGED CLOUD SECURITY POSTURE MANAGEMENT
- 6.4.3 MANAGED CLOUD WORKLOAD PROTECTION PLATFORM
- 6.4.4 MANAGED CLOUD ACCESS SECURITY BROKER SERVICES
- 6.4.5 SAAS SECURITY POSTURE MANAGEMENT
- 6.4.6 CONTAINER & KUBERNETES SECURITY MANAGEMENT
- 6.5 MANAGED SECURITY OPERATIONS & MONITORING SERVICES
- 6.5.1 RISING NEED FOR RAPID INCIDENT RESPONSE TO BOOST DEMAND FOR SOC-AS-A-SERVICE AND SIEM-AS-A-SERVICE
- 6.5.2 SECURITY OPERATIONS CENTER-AS-A-SERVICE
- 6.5.3 MANAGED SIEM-AS-A-SERVICE
- 6.5.4 MANAGED INCIDENT RESPONSE SERVICES
- 6.5.5 OT/ICS SOC MONITORING
- 6.6 MANAGED ADVANCED THREAT DETECTION SERVICES
- 6.6.1 EVOLVING THREAT LANDSCAPE AND SURGE IN RANSOMWARE ATTACKS TO BOOST DEMAND FOR THREAT DETECTION & RECOVERY SERVICES
- 6.6.2 MANAGED DETECTION AND RESPONSE
- 6.6.3 MANAGED EXTENDED DETECTION AND RESPONSE
- 6.6.4 THREAT INTELLIGENCE-AS-A-SERVICE
- 6.6.5 THREAT HUNTING-AS-A-SERVICE
- 6.6.6 RANSOMWARE RECOVERY SERVICES
- 6.6.7 DISASTER RECOVERY & BUSINESS CONTINUITY-AS-A-SERVICE
- 6.7 MANAGED OFFENSIVE SECURITY & ASSESSMENT SERVICES
- 6.7.1 PROACTIVE CYBER DEFENSE AND COMPLIANCE TO BOOST ADOPTION OF SECURITY TESTING & RED TEAMING
- 6.7.2 MANAGED PENETRATION TESTING SERVICES
- 6.7.3 VULNERABILITY ASSESSMENT & MANAGEMENT
- 6.7.4 RED TEAMING-AS-A-SERVICE
- 6.7.5 SECURITY EXPLOITATION TESTING (APP, NETWORK, API)
- 6.7.6 ICS/SCADA SECURITY TESTING
- 6.7.7 SOURCE CODE ANALYSIS-AS-A-SERVICE
- 6.8 MANAGED IDENTITY & DATA PROTECTION SERVICES
- 6.8.1 GROWING IDENTITY-BASED ATTACKS AND ZERO-TRUST MODELS TO FUEL DEMAND FOR MANAGED IAM & DATA PROTECTION
- 6.8.2 MANAGED IDENTITY & ACCESS MANAGEMENT
- 6.8.3 MULTI-FACTOR AUTHENTICATION
- 6.8.4 MANAGED SINGLE SIGN-ON
- 6.8.5 DATA LOSS PREVENTION
- 6.8.6 MANAGED ENCRYPTION & KEY LIFECYCLE MANAGEMENT
- 6.8.7 IDENTITY FEDERATION AND ROLE PROVISIONING SERVICES
- 6.9 MANAGED RISK & COMPLIANCE MANAGEMENT SERVICES
- 6.9.1 EXPANDING ESG COMPLIANCE REQUIREMENTS TO FUEL DEMAND FOR RISK & COMPLIANCE-AS-A-SERVICE
- 6.9.2 COMPLIANCE MANAGEMENT & REPORTING
- 6.9.3 RISK ADVISORY & ASSESSMENT SERVICES
- 6.9.4 GOVERNANCE, RISK & COMPLIANCE PLATFORM INTEGRATION SERVICES
- 6.9.5 PHISHING SIMULATION-AS-A-SERVICE
- 6.9.6 INSIDER THREAT MONITORING & BEHAVIORAL ANALYTICS
- 6.9.7 SECURITY AWARENESS & TRAINING-AS-A-SERVICE
7 MANAGED SECURITY SERVICES MARKET, BY TYPE (MARKET SIZE & FORECAST TO 2030 - IN VALUE (USD))
Detailed breakdown of market share and growth across type
- 7.1 INTRODUCTION
- 7.1.1 TYPE: MANAGED SECURITY SERVICE MARKET DRIVERS
- 7.2 FULLY MANAGED SECURITY SERVICES
- 7.2.1 SHORTAGE OF SKILLED CYBERSECURITY PROFESSIONALS TO DRIVE SHIFT TOWARD FULLY OUTSOURCED SECURITY MODELS
- 7.3 CO-MANAGED SECURITY SERVICES
- 7.3.1 ENTERPRISES SEEKING HYBRID CONTROL MODELS TO FUEL DEMAND FOR CO-MANAGED SERVICES
8 MANAGED SECURITY SERVICES MARKET, BY ORGANIZATION SIZE (MARKET SIZE & FORECAST TO 2030 - IN VALUE (USD))
Detailed breakdown of market share and growth across organization sizes
- 8.1 INTRODUCTION
- 8.1.1 ORGANIZATION SIZE: MANAGED SECURITY SERVICE MARKET DRIVERS
- 8.2 LARGE ENTERPRISES
- 8.2.1 COMPLEX IT ECOSYSTEMS AND HIGHER COMPLIANCE BURDENS TO DRIVE LARGE ENTERPRISE MSS ADOPTION
- 8.3 SMALL AND MEDIUM-SIZED ENTERPRISES
- 8.3.1 RISING CYBER THREAT EXPOSURE AND COST EFFICIENCY NEEDS TO ACCELERATE MSS ADOPTION AMONG SMES
9 MANAGED SECURITY SERVICES MARKET, BY VERTICAL (MARKET SIZE & FORECAST TO 2030 - IN VALUE (USD))
Industry-specific market sizing, growth, and key trends
- 9.1 INTRODUCTION
- 9.1.1 VERTICAL: MANAGED SECURITY SERVICE MARKET DRIVERS
- 9.2 BFSI
- 9.2.1 RISE IN CYBER THREATS AND REGULATORY PRESSURE TO DRIVE ADOPTION OF MANAGED SECURITY SERVICES
- 9.3 GOVERNMENT
- 9.3.1 NATIONAL SECURITY IMPERATIVES TO FUEL GOVERNMENT INVESTMENT IN MANAGED SECURITY SERVICES
- 9.4 HEALTHCARE & LIFE SCIENCES
- 9.4.1 STRINGENT COMPLIANCE REQUIREMENTS TO SPUR DEMAND FOR MANAGED SECURITY SERVICES
- 9.5 TELECOMMUNICATIONS
- 9.5.1 RISING DIGITAL RELIANCE DRIVES TELECOM COMPANIES TO INVEST IN MANAGED SECURITY SOLUTIONS
- 9.6 INFORMATION TECHNOLOGY & INFORMATION TECHNOLOGY-ENABLED SERVICES
- 9.6.1 ESCALATING CYBER THREATS TO PROMPT IT & ITES SECTOR TO EMBRACE SECURITY SERVICES
- 9.7 RETAIL & ECOMMERCE
- 9.7.1 DATA BREACHES TO FUEL RELIANCE ON ROBUST SECURITY SERVICES
- 9.8 ENERGY & UTILITIES
- 9.8.1 NEED FOR CRITICAL INFRASTRUCTURE PROTECTION TO DRIVE ADOPTION OF SECURITY SERVICES
- 9.9 MANUFACTURING
- 9.9.1 INDUSTRY 4.0 CHALLENGES TO BOOST DEMAND FOR REAL-TIME SYSTEMS
- 9.10 OTHER VERTICALS
10 MANAGED SECURITY SERVICES MARKET, BY REGION (MARKET SIZE & FORECAST TO 2030 - IN VALUE (USD))
Regional market sizing, forecasts, and regulatory landscapes
- 10.1 INTRODUCTION
- 10.2 NORTH AMERICA
- 10.2.1 NORTH AMERICA: MANAGED SECURITY SERVICES MARKET DRIVERS
- 10.2.2 NORTH AMERICA: MACROECONOMIC OUTLOOK
- 10.2.3 NORTH AMERICA: REGULATORY LANDSCAPE
- 10.2.4 US
- 10.2.4.1 Rapid technological innovations and presence of large numbers of vendors to fuel demand for MSS solutions
- 10.2.5 CANADA
- 10.2.5.1 Increased cyberattacks, growth in digital infrastructure, and prevalence of internet to drive market
- 10.3 EUROPE
- 10.3.1 EUROPE: MANAGED SECURITY SERVICES MARKET DRIVERS
- 10.3.2 EUROPE: MACROECONOMIC OUTLOOK
- 10.3.3 EUROPE: REGULATORY LANDSCAPE
- 10.3.4 UK
- 10.3.4.1 Increased government regulations and rising number of security breaches to boost demand for managed security services
- 10.3.5 GERMANY
- 10.3.5.1 Rising incidents of cyberattacks and demand for innovative and customized security solutions to drive market
- 10.3.6 FRANCE
- 10.3.6.1 Stringent government regulations and increasing rate of security incidents to propel market
- 10.3.7 ITALY
- 10.3.7.1 Increasing sophisticated cyberattacks and presence of international vendors to fuel demand for security services
- 10.3.8 RUSSIA
- 10.3.8.1 Rising cyber warfare and regulatory directives are reshaping managed security services landscape
- 10.3.9 REST OF EUROPE
- 10.4 ASIA PACIFIC
- 10.4.1 ASIA PACIFIC: MANAGED SECURITY SERVICES MARKET DRIVERS
- 10.4.2 ASIA PACIFIC: MACROECONOMIC OUTLOOK
- 10.4.3 ASIA PACIFIC: REGULATORY LANDSCAPE
- 10.4.4 CHINA
- 10.4.4.1 Increasing investments in IoT projects, rising cybercrime rates, and implementation of new amendments to drive market
- 10.4.5 JAPAN
- 10.4.5.1 Surge in security breaches and government initiatives to safeguard economic security to propel market
- 10.4.6 INDIA
- 10.4.6.1 Fast adoption of cloud technology, thriving fintech sector, and increased digitalization to boost demand for MSS
- 10.4.7 AUSTRALIA
- 10.4.7.1 Rising cyberattacks, strict government regulations, and the need for scalability and cost-effective solutions to drive market
- 10.4.8 SINGAPORE
- 10.4.8.1 Initiatives such as Cybersecurity Strategy and Cyber Security Agency to promote MSS adoption
- 10.4.9 MALAYSIA
- 10.4.9.1 Need for scalability and cost-effectiveness to drive market
- 10.4.10 INDONESIA
- 10.4.10.1 Rising threat landscape, regulatory push, and cloud adoption to boost MSS demand
- 10.4.11 THAILAND
- 10.4.11.1 Digital transformation and rising cybercrime to boost MSS adoption
- 10.4.12 PHILIPPINES
- 10.4.12.1 Digital adoption surge, regulatory enforcement, and cyber threats to drive MSS adoption
- 10.4.13 REST OF ASIA PACIFIC
- 10.5 MIDDLE EAST & AFRICA
- 10.5.1 MIDDLE EAST & AFRICA: MANAGED SECURITY SERVICES MARKET DRIVERS
- 10.5.2 MIDDLE EAST & AFRICA: MACROECONOMIC OUTLOOK
- 10.5.3 MIDDLE EAST & AFRICA: REGULATORY LANDSCAPE
- 10.5.4 MIDDLE EAST
- 10.5.4.1 Implementation of National Cybersecurity Strategy to assess cybersecurity risks to drive market
- 10.5.4.2 GCC Countries
- 10.5.4.2.1 Rising cyber risk maturity and digital-first mandates to drive market growth
- 10.5.4.2.2 KSA
- 10.5.4.2.3 UAE
- 10.5.4.2.4 Rest of GCC countries
- 10.5.4.3 Rest of Middle East
- 10.5.5 AFRICA
- 10.5.5.1 Need for strong cyber defense governance policy and increased public awareness regarding cyber threats to propel market
- 10.6 LATIN AMERICA
- 10.6.1 LATIN AMERICA: MANAGED SECURITY SERVICES MARKET DRIVERS
- 10.6.2 LATIN AMERICA: MACROECONOMIC OUTLOOK
- 10.6.3 LATIN AMERICA: REGULATORY LANDSCAPE
- 10.6.4 BRAZIL
- 10.6.4.1 Rising cybercrimes and need to secure and improve endpoints, networks, and applications to propel market
- 10.6.5 MEXICO
- 10.6.5.1 Government initiatives to fight against increasing cybercrimes to drive market
- 10.6.6 REST OF LATIN AMERICA
11 COMPETITIVE LANDSCAPE
Strategic Profiles of Leading Players & Their Playbooks for Market Dominance
- 11.1 KEY PLAYER STRATEGIES/RIGHT TO WIN
- 11.2 REVENUE ANALYSIS, 2020-2024
- 11.3 MARKET SHARE ANALYSIS, 2024
- 11.4 BRAND/PRODUCT COMPARISON
- 11.5 COMPANY VALUATION AND FINANCIAL METRICS
- 11.5.1 COMPANY VALUATION
- 11.5.2 FINANCIAL METRICS OF KEY VENDORS
- 11.6 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 11.6.1 STARS
- 11.6.2 EMERGING LEADERS
- 11.6.3 PERVASIVE PLAYERS
- 11.6.4 PARTICIPANTS
- 11.6.5 COMPANY FOOTPRINT: KEY PLAYERS, 2024
- 11.6.5.1 Company footprint
- 11.6.5.2 Regional footprint
- 11.6.5.3 Type footprint
- 11.6.5.4 Vertical footprint
- 11.7 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 11.7.1 PROGRESSIVE COMPANIES
- 11.7.2 RESPONSIVE COMPANIES
- 11.7.3 DYNAMIC COMPANIES
- 11.7.4 STARTING BLOCKS
- 11.7.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
- 11.7.5.1 Detailed list of key startups/SMEs
- 11.7.5.2 Competitive benchmarking of key startups/SMEs
- 11.8 COMPETITIVE SCENARIO
- 11.8.1 PRODUCT LAUNCHES & DEVELOPMENTS
- 11.8.2 DEALS
12 COMPANY PROFILES
In-depth look at their Strengths, Weaknesses, Product Portfolios, Recent Developments, and Strategic Moves
- 12.1 KEY PLAYERS
- 12.1.1 IBM
- 12.1.1.1 Business overview
- 12.1.1.2 Products/Solutions/Services offered
- 12.1.1.3 Recent developments
- 12.1.1.3.1 Product launches/developments
- 12.1.1.3.2 Deals
- 12.1.1.4 MnM view
- 12.1.1.4.1 Right to win
- 12.1.1.4.2 Strategic choices
- 12.1.1.4.3 Weaknesses and competitive threats
- 12.1.2 NTT
- 12.1.2.1 Business overview
- 12.1.2.2 Products/Solutions/Services offered
- 12.1.2.3 Recent developments
- 12.1.2.3.1 Product launches/developments
- 12.1.2.3.2 Deals
- 12.1.2.4 MnM view
- 12.1.2.4.1 Right to win
- 12.1.2.4.2 Strategic choices
- 12.1.2.4.3 Weaknesses and competitive threats
- 12.1.3 LEVELBLUE
- 12.1.3.1 Business overview
- 12.1.3.2 Products/Solutions/Services offered
- 12.1.3.3 Recent developments
- 12.1.3.3.1 Product launches/developments
- 12.1.3.4 MnM view
- 12.1.3.4.1 Right to win
- 12.1.3.4.2 Strategic choices
- 12.1.3.4.3 Weaknesses and competitive threats
- 12.1.4 ACCENTURE
- 12.1.4.1 Business overview
- 12.1.4.2 Products/Solutions/Services offered
- 12.1.4.3 Recent developments
- 12.1.4.3.1 Product launches/developments
- 12.1.4.3.2 Deals
- 12.1.4.3.3 Expansions
- 12.1.4.4 MnM view
- 12.1.4.4.1 Right to win
- 12.1.4.4.2 Strategic choices
- 12.1.4.4.3 Weaknesses and competitive threats
- 12.1.5 DXC TECHNOLOGY
- 12.1.5.1 Business overview
- 12.1.5.2 Products/Solutions/Services offered
- 12.1.5.3 Recent developments
- 12.1.5.3.1 Deals
- 12.1.5.4 MnM view
- 12.1.5.4.1 Right to win
- 12.1.5.4.2 Strategic choices
- 12.1.5.4.3 Weaknesses and competitive threats
- 12.1.6 SECNAP
- 12.1.6.1 Business overview
- 12.1.6.2 Products/Solutions/Services offered
- 12.1.6.3 Recent developments
- 12.1.6.3.1 Product launches/developments
- 12.1.6.3.2 Deals
- 12.1.7 DELOITTE
- 12.1.7.1 Business overview
- 12.1.7.2 Products/Solutions/Services offered
- 12.1.7.3 Recent developments
- 12.1.7.3.1 Product launches/developments
- 12.1.7.3.2 Deals
- 12.1.7.3.3 Expansions
- 12.1.8 SECUREWORKS
- 12.1.8.1 Business overview
- 12.1.8.2 Products/Solutions/Services offered
- 12.1.8.3 Recent developments
- 12.1.8.3.1 Product launches/developments
- 12.1.8.3.2 Deals
- 12.1.8.3.3 Expansions
- 12.1.9 TRUSTWAVE
- 12.1.9.1 Business overview
- 12.1.9.2 Products/Solutions/Services offered
- 12.1.9.3 Recent developments
- 12.1.9.3.1 Product launches/developments
- 12.1.9.3.2 Deals
- 12.1.10 VERIZON
- 12.1.10.1 Business overview
- 12.1.10.2 Products/Solutions/Services offered
- 12.1.10.3 Recent developments
- 12.1.10.3.1 Product launches/developments
- 12.1.10.3.2 Deals
- 12.1.11 FUJITSU
- 12.1.11.1 Business overview
- 12.1.11.2 Products/Solutions/Services offered
- 12.1.11.3 Recent developments
- 12.1.11.3.1 Deals
- 12.1.11.3.2 Expansions
- 12.1.12 HPE
- 12.1.12.1 Business overview
- 12.1.12.2 Products/Solutions/Services offered
- 12.1.12.3 Recent developments
- 12.1.12.3.1 Product launches/developments
- 12.1.12.3.2 Deals
- 12.1.13 TCS
- 12.1.13.1 Business overview
- 12.1.13.2 Products/Solutions/Services offered
- 12.1.13.3 Recent developments
- 12.1.13.3.1 Deals
- 12.1.14 ATOS
- 12.1.14.1 Business overview
- 12.1.14.2 Products/Solutions/Services offered
- 12.1.14.3 Recent developments
- 12.1.14.3.1 Product launches/developments
- 12.1.14.3.2 Deals
- 12.1.15 ORANGE CYBERDEFENSE
- 12.1.15.1 Business overview
- 12.1.15.2 Products/Solutions/Services offered
- 12.1.15.3 Recent developments
- 12.1.15.3.1 Product launches/developments
- 12.1.15.3.2 Deals
- 12.1.16 RAPID7
- 12.1.16.1 Business overview
- 12.1.16.2 Products/Solutions/Services offered
- 12.1.16.3 Recent developments
- 12.1.16.3.1 Product launches/developments
- 12.1.16.3.2 Deals
- 12.1.16.3.3 Expansions
- 12.1.17 TREND MICRO
- 12.1.17.1 Business overview
- 12.1.17.2 Products/Solutions/Services offered
- 12.1.17.3 Recent developments
- 12.1.17.3.1 Product launches/developments
- 12.1.17.3.2 Deals
- 12.1.17.3.3 Expansions
- 12.1.18 KUDELSKI SECURITY
- 12.1.18.1 Business overview
- 12.1.18.2 Products/Solutions/Services offered
- 12.1.18.3 Recent developments
- 12.1.18.3.1 Product launches/developments
- 12.1.18.3.2 Deals
- 12.1.19 CROWDSTRIKE
- 12.1.19.1 Business overview
- 12.1.19.2 Products/Solutions/Services offered
- 12.1.19.3 Recent developments
- 12.1.19.3.1 Product launches/developments
- 12.1.19.3.2 Deals
- 12.1.19.3.3 Expansions
- 12.1.20 F5
- 12.1.20.1 Business overview
- 12.1.20.2 Products/Solutions/Services offered
- 12.1.20.3 Recent developments
- 12.1.20.3.1 Product launches/developments
- 12.1.20.3.2 Deals
- 12.1.21 CAPGEMINI
- 12.1.21.1 Business overview
- 12.1.21.2 Products/Solutions/Services offered
- 12.1.22 INFOSYS
- 12.1.22.1 Business overview
- 12.1.22.2 Products/Solutions/Services offered
- 12.1.22.3 Recent developments
- 12.1.22.3.1 Deals
- 12.1.23 LUMEN TECHNOLOGIES
- 12.1.23.1 Business overview
- 12.1.23.2 Products/Solutions/Services offered
- 12.1.23.3 Recent developments
- 12.1.23.3.1 Product launches/developments
- 12.1.23.3.2 Deals
- 12.1.23.3.3 Expansions
- 12.1.24 KROLL
- 12.1.24.1 Business overview
- 12.1.24.2 Products/Solutions/Services offered
- 12.1.24.3 Recent developments
- 12.1.24.3.1 Deals
- 12.1.24.3.2 Expansions
- 12.1.1 IBM
- 12.2 OTHER PLAYERS
- 12.2.1 NETSURION
- 12.2.2 ATLAS SYSTEMS
- 12.2.3 CIPHER
- 12.2.4 RSI SECURITY
- 12.2.5 SECURITY HQ
- 12.2.6 LIGHTEDGE
- 12.2.7 LRQA NETTITUDE
- 12.2.8 TECEZE
- 12.2.9 CYFLARE
- 12.2.10 ASCEND TECHNOLOGIES
- 12.2.11 AVERTIUM
- 12.2.12 DIGITALXRAID
- 12.2.13 TRUSTNET
13 ADJACENT MARKETS
- 13.1 INTRODUCTION TO ADJACENT MARKETS
- 13.2 LIMITATIONS
- 13.3 ADJACENT MARKETS
- 13.3.1 CYBERSECURITY MARKET
- 13.3.2 SOC-AS-A-SERVICE MARKET
14 APPENDIX
- 14.1 DISCUSSION GUIDE
- 14.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 14.3 CUSTOMIZATION OPTIONS
- 14.4 RELATED REPORTS
- 14.5 AUTHOR DETAILS