|
|
市場調査レポート
商品コード
1718903
OTセキュリティの世界市場:サービス別、展開方式別、組織規模別、業界別 - 予測(~2030年)Operational Technology (OT) Security Market by Offering (Solutions and Services), Deployment Mode (On-premises and Cloud), Organization Size (SMEs and Large Enterprises), Vertical (Manufacturing, Oil & Gas, and Energy & Power) - Global Forecast to 2030 |
||||||
カスタマイズ可能
|
|||||||
| OTセキュリティの世界市場:サービス別、展開方式別、組織規模別、業界別 - 予測(~2030年) |
|
出版日: 2025年04月30日
発行: MarketsandMarkets
ページ情報: 英文 455 Pages
納期: 即納可能
|
全表示
- 概要
- 図表
- 目次
世界のOTセキュリティの市場規模は、2025年の234億7,000万米ドルから2030年までに502億9,000万米ドルに達すると予測され、予測期間にCAGRで16.5%の成長が見込まれます。
政府や産業団体が重要インフラを保護するためにサイバーセキュリティの強化を義務付けているため、規制圧力の高まりがOTセキュリティ市場の主な促進要因となっています。EUのNIS2指令、米国のサイバーセキュリティ行政命令、NISTやIECのような団体の標準などの規制は、エネルギー、製造、輸送などの部門の組織に堅牢なOTセキュリティ対策の実施を求めています。こうした規制への対応により、企業は運用環境を保護するための先進のソリューションへの投資を進めています。
| 調査範囲 | |
|---|---|
| 調査対象年 | 2019年~2030年 |
| 基準年 | 2024年 |
| 予測期間 | 2025年~2030年 |
| 単位 | 10億米ドル |
| セグメント | 提供、展開方式、組織規模、業界、地域 |
| 対象地域 | 北米、欧州、アジア太平洋、中東・アフリカ、ラテンアメリカ |
「業界別では、エネルギー・電力セグメントが予測期間にもっとも高いCAGRを記録する見込みです。」
エネルギー・電力セグメントは、その重要な役割とサイバー脅威への露出の増加により、OTセキュリティ市場でもっとも高いCAGRを記録すると予測されます。スマートグリッドやデジタルシステムの採用が増加しているため、攻撃のリスクが高まっています。例えば、インドのテランガナ州とアンドラプラデシュ州の相互接続された電力企業のシステムに対する近年のランサムウェア攻撃は、完全なシャットダウンにつながり、この部門における強固なOTサイバーセキュリティの緊急の必要性を浮き彫りにしました。
「地域別では、北米が2025年に最大の市場シェアを占めると推定されます。」
北米がOTセキュリティ市場で大きなシェアを占めているのは、先進技術の高い採用率や、サイバー脅威に対する意識の高まり、厳しい規制要件などに起因します。この地域のエネルギー、製造、輸送などの産業部門は、重要インフラを保護するためにOTセキュリティに多額の投資を行っています。さらに、Fortinet、Cisco、Trellixといった主要市場企業のプレゼンスと、サイバーセキュリティソリューションにおける継続的な技術革新が、世界のOTセキュリティ市場における北米の優位性をさらに高めています。
当レポートでは、世界のOTセキュリティ市場について調査分析し、主な促進要因と抑制要因、競合情勢、将来の動向などの情報を提供しています。
目次
第1章 イントロダクション
第2章 調査手法
第3章 エグゼクティブサマリー
第4章 主な調査結果
- OTセキュリティ市場の企業にとって魅力的な機会
- OTセキュリティ市場の予測
- OTセキュリティ市場:地域別
- OTセキュリティ市場:ソリューション別
- OTセキュリティ市場:サービス別
- OTセキュリティ市場:展開方式別
- OTセキュリティ市場:組織規模別
- OTセキュリティ市場:業界別
- 市場投資シナリオ
第5章 市場の概要と産業動向
- イントロダクション
- 市場力学
- 促進要因
- 抑制要因
- 機会
- 課題
- OTセキュリティの進化
- エコシステム分析
- バリューチェーン分析
- OTセキュリティのソリューションとツールのプロバイダー
- サービスプロバイダー
- システムインテグレーター
- 小売/流通
- エンドユーザー
- 技術分析
- 主要技術
- 補完技術
- 隣接技術
- 規制情勢
- 規制機関、政府機関、その他の組織
- 主な規制
- 特許分析
- 価格分析
- 主要企業の平均販売価格の動向:ソリューションタイプ別
- 主要OTセキュリティベンダーの参考価格分析:サービス別
- ポーターのファイブフォース分析
- 主なステークホルダーと購入基準
- OTセキュリティ攻撃(2023年~2024年)
- ケーススタディ
- カリフォルニア州水道局がFortinetのソリューションを活用し、ネットワーク管理を強化
- 国際プラスチックメーカーがOTの可視性を改良し、リスクを軽減
- ZSCALER、カリフォルニアの酪農場のクラウドベース環境への移行を支援
- ハウラキ地区議会がDarktraceのAIを活用して重要なインフラを保護し、サードパーティのリスクを管理
- Keysight、メキシコの鉱業大手に包括的なOTセキュリティを提供
- 顧客のビジネスに影響を与える動向と混乱
- 主な会議とイベント(2025年~2026年)
- 投資と資金調達シナリオ(2021年~2024年)
- NISTフレームワーク
- OTセキュリティ市場:技術ロードマップ
- OTセキュリティのビジネスモデル
- マネージドセキュリティサービス(MSS)
- セキュリティ、ソリューション
- セキュリティコンサルティング
- OTセキュリティ市場に対するAI/生成AIの影響
- OTセキュリティにおける生成AIのユースケース
- 相互接続された隣接エコシステムに対する生成AIの影響
第6章 2025年の米国の関税の影響 - OTセキュリティ市場
- イントロダクション
- 主要関税率
- 価格の影響の分析
- 国/地域に対する影響
- 北米
- 米国
- カナダ
- メキシコ
- 市場の課題
- 緩和策
- 欧州
- ドイツ
- フランス
- 英国
- 市場の課題
- 緩和策
- アジア太平洋
- 中国
- インド
- オーストラリア
- 市場の課題
- 緩和策
- 最終用途産業に対する影響
第7章 OTセキュリティ市場:提供別
- イントロダクション
- ソリューション
- SIEM
- 資産発見・管理
- ネットワークセキュリティ
- 脆弱性管理
- ID・アクセス管理(IAM)
- データセキュリティ
- その他の解決策
- サービス
- コンサルティング・統合サービス
- サポート・メンテナンスサービス
- トレーニング・開発サービス
- インシデント対応サービス
- マネージドセキュリティサービス
第8章 OTセキュリティ市場:展開方式別
- イントロダクション
- クラウド
- オンプレミス
第9章 OTセキュリティ市場:組織規模別
- イントロダクション
- 中小企業
- 大企業
第10章 OTセキュリティ市場:業界別
- イントロダクション
- 輸送・ロジスティクス
- 製造
- エネルギー・電力
- 石油・ガス
- その他の業界
第11章 OTセキュリティ市場:地域別
- イントロダクション
- 北米
- 北米のOTセキュリティ市場の促進要因
- 北米のマクロ経済の見通し
- 米国
- カナダ
- 欧州
- 欧州のOTセキュリティ市場の促進要因
- 欧州のマクロ経済の見通し
- 英国
- ドイツ
- イタリア
- フランス
- フィンランド
- スウェーデン
- ベネルクス
- スペイン
- ポルトガル
- デンマーク
- ノルウェー
- オーストリア
- スイス
- その他の欧州
- アジア太平洋
- アジア太平洋のOTセキュリティ市場の促進要因
- アジア太平洋のマクロ経済の見通し
- 中国
- 日本
- インド
- その他のアジア太平洋
- 中東・アフリカ
- 中東・アフリカのOTセキュリティ市場の促進要因
- 中東・アフリカのマクロ経済の見通し
- GCC
- 南アフリカ
- その他の中東・アフリカ
- ラテンアメリカ
- ラテンアメリカのOTセキュリティ市場の促進要因
- ラテンアメリカのマクロ経済の見通し
- メキシコ
- ブラジル
- その他のラテンアメリカ
第12章 競合情勢
- 主要参入企業の戦略/強み(2022年~2024年)
- 収益分析(2020年~2024年)
- 市場シェア分析(2024年)
- ブランドの比較
- CISCO
- TENABLE
- MICROSOFT
- FORCEPOINT
- PALO ALTO NETWORKS
- 企業の評価と財務指標
- 企業の評価(2024年)
- EV/EBIDTAを用いた財務指標
- 企業の評価マトリクス:主要企業(2024年)
- 企業の評価マトリクス:スタートアップ/中小企業(2024年)
- 競合シナリオ
第13章 企業プロファイル
- イントロダクション
- 主要企業
- CISCO
- TENABLE
- MICROSOFT
- FORCEPOINT
- PALO ALTO NETWORKS
- FORTINET
- FORESCOUT
- SECKIOT
- CHECK POINT
- BROADCOM
- TRELLIX
- OKTA
- QUALYS
- ZSCALER
- BEYONDTRUST
- CYBERARK
- RAPID7
- SOPHOS
- TRIPWIRE
- RADIFLOW
- KASPERSKY
- SENTINELONE
- THALES
- ARMIS
- DARKTRACE
- NOZOMI NETWORKS
- HONEYWELL
- SCHNEIDER ELECTRIC
- SIEMENS
- ABB
- TOSIBOX
- その他の企業
- RHEBO
- SHIELD-IOT
- CLAROTY
- DRAGOS
- CYDOME
- MISSION SECURE
- ORDR
- RUNZERO
- SIGA OT SOLUTIONS
- SECTRIO
- WATERFALL SECURITY
- OPSWAT
第14章 隣接市場
- 隣接市場のイントロダクション
- 制限事項
- ICSセキュリティ市場
- 重要インフラ保護市場
第15章 付録
List of Tables
- TABLE 1 USD EXCHANGE RATES, 2022-2024
- TABLE 2 FACTOR ANALYSIS
- TABLE 3 OPERATIONAL TECHNOLOGY SECURITY MARKET SIZE AND GROWTH, 2024-2030 (USD MILLION, Y-O-Y GROWTH)
- TABLE 4 ROLE OF COMPANIES IN ECOSYSTEM
- TABLE 5 NORTH AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 6 EUROPE: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 7 ASIA PACIFIC: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 8 REST OF THE WORLD: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 9 OPERATIONAL TECHNOLOGY SECURITY MARKET: LIST OF TOP PATENTS, 2024
- TABLE 10 AVERAGE SELLING PRICE TREND OF KEY PLAYERS, BY SOLUTION TYPE (USD)
- TABLE 11 IMPACT OF PORTER'S FIVE FORCES ON OPERATIONAL TECHNOLOGY SECURITY MARKET
- TABLE 12 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS
- TABLE 13 KEY BUYING CRITERIA FOR TOP THREE VERTICALS
- TABLE 14 OPERATIONAL TECHNOLOGY SECURITY MARKET: LIST OF KEY CONFERENCES AND EVENTS, 2025-2026
- TABLE 15 SHORT-TERM ROADMAP, 2023-2025
- TABLE 16 MID-TERM ROADMAP, 2026-2028
- TABLE 17 LONG-TERM ROADMAP, 2029-2030
- TABLE 18 US ADJUSTED RECIPROCAL TARIFF RATES
- TABLE 19 KEY PRODUCT-RELATED TARIFF EFFECTIVE FOR OT SECURITY HARDWARE
- TABLE 20 EXPECTED CHANGE IN PRICES AND LIKELY IMPACT ON END-USE MARKET DUE TO TARIFF IMPACT
- TABLE 21 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 22 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 23 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 24 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 25 SOLUTIONS: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 26 SOLUTIONS: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 27 SECURITY INFORMATION & EVENT MANAGEMENT (SIEM): OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 28 SECURITY INFORMATION & EVENT MANAGEMENT (SIEM): OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 29 ASSET DISCOVERY & MANAGEMENT: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 30 ASSET DISCOVERY & MANAGEMENT: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 31 NETWORK SECURITY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 32 NETWORK SECURITY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 33 VULNERABILITY MANAGEMENT: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 34 VULNERABILITY MANAGEMENT: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 35 IDENTITY & ACCESS MANAGEMENT (IAM): OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 36 IDENTITY & ACCESS MANAGEMENT (IAM): OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 37 DATA SECURITY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 38 DATA SECURITY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 39 OTHER SOLUTIONS: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 40 OTHER SOLUTIONS: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 41 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 42 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 43 SERVICES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 44 SERVICES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 45 CONSULTING & INTEGRATION SERVICES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 46 CONSULTING & INTEGRATION SERVICES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 47 SUPPORT & MAINTENANCE SERVICES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 48 SUPPORT & MAINTENANCE SERVICES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 49 TRAINING & DEVELOPMENT SERVICES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 50 TRAINING & DEVELOPMENT SERVICES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 51 INCIDENT RESPONSE SERVICES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 52 INCIDENT RESPONSE SERVICES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 53 MANAGED SECURITY SERVICES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 54 MANAGED SECURITY SERVICES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 55 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 56 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 57 CLOUD: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 58 CLOUD: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 59 ON-PREMISES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 60 ON-PREMISES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 61 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 62 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 63 SMES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 64 SMES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 65 LARGE ENTERPRISES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 66 LARGE ENTERPRISES: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 67 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 68 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 69 TRANSPORTATION & LOGISTICS: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 70 TRANSPORTATION & LOGISTICS: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 71 MANUFACTURING: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 72 MANUFACTURING: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 73 ENERGY & POWER: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 74 ENERGY & POWER OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 75 OIL & GAS: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 76 OIL & GAS: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 77 OTHER VERTICALS: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 78 OTHER VERTICALS: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 79 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 80 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 81 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 82 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 83 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 84 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 85 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 86 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 87 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 88 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 89 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 90 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 91 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 92 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 93 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 94 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 95 US: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 96 US: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 97 US: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 98 US: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 99 US: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 100 US: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 101 US: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 102 US: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 103 US: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 104 US: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 105 US: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 106 US: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 107 CANADA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 108 CANADA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 109 CANADA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 110 CANADA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 111 CANADA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 112 CANADA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 113 CANADA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 114 CANADA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 115 CANADA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 116 CANADA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 117 CANADA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 118 CANADA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 119 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 120 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 121 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 122 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 123 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 124 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 125 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 126 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 127 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 128 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 129 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 130 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 131 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 132 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 133 UK: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 134 UK: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 135 UK: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 136 UK: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 137 UK: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 138 UK: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 139 UK: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 140 UK: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 141 UK: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 142 UK: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 143 UK: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 144 UK: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 145 GERMANY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 146 GERMANY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 147 GERMANY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 148 GERMANY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 149 GERMANY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 150 GERMANY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 151 GERMANY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 152 GERMANY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 153 GERMANY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 154 GERMANY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 155 GERMANY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 156 GERMANY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 157 ITALY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 158 ITALY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 159 ITALY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 160 ITALY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 161 ITALY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 162 ITALY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 163 ITALY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 164 ITALY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 165 ITALY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 166 ITALY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 167 ITALY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 168 ITALY: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 169 FRANCE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 170 FRANCE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 171 FRANCE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 172 FRANCE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 173 FRANCE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 174 FRANCE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 175 FRANCE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 176 FRANCE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 177 FRANCE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 178 FRANCE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 179 FRANCE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 180 FRANCE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 181 REST OF EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 182 REST OF EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 183 REST OF EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 184 REST OF EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 185 REST OF EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 186 REST OF EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 187 REST OF EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 188 REST OF EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 189 REST OF EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 190 REST OF EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 191 REST OF EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 192 REST OF EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 193 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 194 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 195 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 196 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 197 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 198 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 199 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 200 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 201 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 202 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 203 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 204 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 205 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 206 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 207 CHINA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 208 CHINA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 209 CHINA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 210 CHINA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 211 CHINA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 212 CHINA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 213 CHINA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 214 CHINA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 215 CHINA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 216 CHINA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 217 CHINA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 218 CHINA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 219 JAPAN: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 220 JAPAN: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 221 JAPAN: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 222 JAPAN: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 223 JAPAN: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 224 JAPAN: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 225 JAPAN: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 226 JAPAN: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 227 JAPAN: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 228 JAPAN: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 229 JAPAN: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 230 JAPAN: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 231 INDIA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 232 INDIA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 233 INDIA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 234 INDIA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 235 INDIA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 236 INDIA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 237 INDIA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 238 INDIA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 239 INDIA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 240 INDIA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 241 INDIA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 242 INDIA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 243 REST OF ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 244 REST OF ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 245 REST OF ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 246 REST OF ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 247 REST OF ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 248 REST OF ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 249 REST OF ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 250 REST OF ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 251 REST OF ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 252 REST OF ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 253 REST OF ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 254 REST OF ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 255 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 256 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 257 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 258 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 259 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 260 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 261 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 262 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 263 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 264 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 265 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 266 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 267 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 268 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 269 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 270 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 271 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 272 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 273 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 274 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 275 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 276 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 277 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 278 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 279 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 280 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 281 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 282 GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 283 KSA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 284 KSA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 285 KSA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 286 KSA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 287 KSA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 288 KSA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 289 KSA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 290 KSA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 291 KSA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 292 KSA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 293 KSA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 294 KSA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 295 UAE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 296 UAE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 297 UAE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 298 UAE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 299 UAE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 300 UAE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 301 UAE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 302 UAE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 303 UAE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 304 UAE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 305 UAE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 306 UAE: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 307 REST OF GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 308 REST OF GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 309 REST OF GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 310 REST OF GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 311 REST OF GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 312 REST OF GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 313 REST OF GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 314 REST OF GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 315 REST OF GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 316 REST OF GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 317 REST OF GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 318 REST OF GCC: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 319 SOUTH AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 320 SOUTH AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 321 SOUTH AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 322 SOUTH AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 323 SOUTH AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 324 SOUTH AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 325 SOUTH AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 326 SOUTH AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 327 SOUTH AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 328 SOUTH AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 329 SOUTH AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 330 SOUTH AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 331 REST OF MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 332 REST OF MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 333 REST OF MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 334 REST OF MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 335 REST OF MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 336 REST OF MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 337 REST OF MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 338 REST OF MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 339 REST OF MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 340 REST OF MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 341 REST OF MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 342 REST OF MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 343 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 344 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 345 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 346 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 347 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 348 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 349 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 350 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 351 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 352 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 353 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 354 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 355 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 356 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 357 MEXICO: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 358 MEXICO: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 359 MEXICO: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 360 MEXICO: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 361 MEXICO: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 362 MEXICO: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 363 MEXICO: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 364 MEXICO: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 365 MEXICO: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 366 MEXICO: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 367 MEXICO: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 368 MEXICO: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 369 BRAZIL: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 370 BRAZIL: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 371 BRAZIL: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 372 BRAZIL: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 373 BRAZIL: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 374 BRAZIL: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 375 BRAZIL: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 376 BRAZIL: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 377 BRAZIL: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 378 BRAZIL: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 379 BRAZIL: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 380 BRAZIL: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 381 REST OF LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 382 REST OF LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 383 REST OF LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2019-2024 (USD MILLION)
- TABLE 384 REST OF LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION, 2025-2030 (USD MILLION)
- TABLE 385 REST OF LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 386 REST OF LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 387 REST OF LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 388 REST OF LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 389 REST OF LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2019-2024 (USD MILLION)
- TABLE 390 REST OF LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE, 2025-2030 (USD MILLION)
- TABLE 391 REST OF LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 392 REST OF LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 393 OVERVIEW OF STRATEGIES ADOPTED BY KEY MARKET PLAYERS, 2022-2024
- TABLE 394 OPERATIONAL TECHNOLOGY SECURITY MARKET: DEGREE OF COMPETITION
- TABLE 395 OPERATIONAL TECHNOLOGY SECURITY MARKET: REGION FOOTPRINT
- TABLE 396 OPERATIONAL TECHNOLOGY SECURITY MARKET: OFFERING FOOTPRINT
- TABLE 397 OPERATIONAL TECHNOLOGY SECURITY MARKET: ORGANIZATION SIZE FOOTPRINT
- TABLE 398 OPERATIONAL TECHNOLOGY SECURITY MARKET: VERTICAL FOOTPRINT
- TABLE 399 OPERATIONAL TECHNOLOGY SECURITY MARKET: KEY STARTUPS/SMES
- TABLE 400 OPERATIONAL TECHNOLOGY SECURITY MARKET: COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES
- TABLE 401 OPERATIONAL TECHNOLOGY SECURITY MARKET: PRODUCT LAUNCHES/ENHANCEMENTS, JANUARY 2021-APRIL 2025
- TABLE 402 OPERATIONAL TECHNOLOGY SECURITY MARKET: DEALS, JANUARY 2021-APRIL 2025
- TABLE 403 CISCO: COMPANY OVERVIEW
- TABLE 404 CISCO: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 405 CISCO: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 406 CISCO: DEALS
- TABLE 407 TENABLE: COMPANY OVERVIEW
- TABLE 408 TENABLE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 409 TENABLE: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 410 TENABLE: DEALS
- TABLE 411 MICROSOFT: COMPANY OVERVIEW
- TABLE 412 MICROSOFT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 413 MICROSOFT: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 414 MICROSOFT: DEALS
- TABLE 415 FORCEPOINT: COMPANY OVERVIEW
- TABLE 416 FORCEPOINT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 417 FORCEPOINT: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 418 FORCEPOINT: DEALS
- TABLE 419 FORCEPOINT: OTHER DEVELOPMENTS
- TABLE 420 PALO ALTO NETWORKS: COMPANY OVERVIEW
- TABLE 421 PALO ALTO NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 422 PALO ALTO NETWORKS: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 423 PALO ALTO NETWORKS: DEALS
- TABLE 424 FORTINET: COMPANY OVERVIEW
- TABLE 425 FORTINET: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 426 FORTINET: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 427 FORTINET: DEALS
- TABLE 428 FORESCOUT: COMPANY OVERVIEW
- TABLE 429 FORESCOUT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 430 FORESCOUT: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 431 FORESCOUT: DEALS
- TABLE 432 SECKIOT: COMPANY OVERVIEW
- TABLE 433 SECKIOT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 434 CHECK POINT: COMPANY OVERVIEW
- TABLE 435 CHECK POINT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 436 CHECK POINT: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 437 CHECK POINT: DEALS
- TABLE 438 BROADCOM: COMPANY OVERVIEW
- TABLE 439 BROADCOM: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 440 BROADCOM: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 441 BROADCOM: DEALS
- TABLE 442 TRELLIX: COMPANY OVERVIEW
- TABLE 443 TRELLIX: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 444 TRELLIX: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 445 TRELLIX: DEALS
- TABLE 446 OKTA: COMPANY OVERVIEW
- TABLE 447 OKTA: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 448 OKTA: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 449 OKTA: DEALS
- TABLE 450 QUALYS: COMPANY OVERVIEW
- TABLE 451 QUALYS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 452 QUALYS: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 453 QUALYS: DEALS
- TABLE 454 ZSCALER: COMPANY OVERVIEW
- TABLE 455 ZSCALER: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 456 ZSCALER: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 457 ZSCALER: DEALS
- TABLE 458 BEYONDTRUST: COMPANY OVERVIEW
- TABLE 459 BEYONDTRUST: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 460 BEYONDTRUST: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 461 BEYONDTRUST: DEALS
- TABLE 462 CYBERARK: COMPANY OVERVIEW
- TABLE 463 CYBERARK: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 464 CYBERARK: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 465 CYBERARK: DEALS
- TABLE 466 RAPID7: COMPANY OVERVIEW
- TABLE 467 RAPID7: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 468 RAPID7: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 469 RAPID7: DEALS
- TABLE 470 SOPHOS: COMPANY OVERVIEW
- TABLE 471 SOPHOS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 472 SOPHOS: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 473 SOPHOS: DEALS
- TABLE 474 TRIPWIRE: COMPANY OVERVIEW
- TABLE 475 TRIPWIRE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 476 TRIPWIRE: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 477 TRIPWIRE: DEALS
- TABLE 478 RADIFLOW: COMPANY OVERVIEW
- TABLE 479 RADIFLOW: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 480 RADIFLOW: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 481 RADIFLOW: DEALS
- TABLE 482 KASPERSKY: COMPANY OVERVIEW
- TABLE 483 KASPERSKY: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 484 KASPERSKY: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 485 KASPERSKY: DEALS
- TABLE 486 SENTINELONE: COMPANY OVERVIEW
- TABLE 487 SENTINELONE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 488 SENTINELONE: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 489 SENTINELONE: DEALS
- TABLE 490 THALES: COMPANY OVERVIEW
- TABLE 491 THALES: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 492 THALES: DEALS
- TABLE 493 ARMIS: COMPANY OVERVIEW
- TABLE 494 ARMIS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 495 ARMIS: DEALS
- TABLE 496 DARKTRACE: COMPANY OVERVIEW
- TABLE 497 DARKTRACE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 498 DARKTRACE: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 499 DARKTRACE: DEALS
- TABLE 500 NOZOMI NETWORKS: COMPANY OVERVIEW
- TABLE 501 NOZOMI NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 502 NOZOMI NETWORKS: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 503 NOZOMI NETWORKS: DEALS
- TABLE 504 HONEYWELL: COMPANY OVERVIEW
- TABLE 505 HONEYWELL: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 506 HONEYWELL: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 507 HONEYWELL: DEALS
- TABLE 508 SCHNEIDER ELECTRIC: COMPANY OVERVIEW
- TABLE 509 SCHNEIDER ELECTRIC: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 510 SCHNEIDER ELECTRIC: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 511 SCHNEIDER ELECTRIC: DEALS
- TABLE 512 SIEMENS: COMPANY OVERVIEW
- TABLE 513 SIEMENS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 514 SIEMENS: DEALS
- TABLE 515 ABB: COMPANY OVERVIEW
- TABLE 516 ABB: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 517 ABB: DEALS
- TABLE 518 TOSIBOX: COMPANY OVERVIEW
- TABLE 519 TOSIBOX: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 520 TOSIBOX: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 521 TOSIBOX: DEALS
- TABLE 522 TOSIBOX: EXPANSIONS
- TABLE 523 MARKETS ADJACENT TO OPERATIONAL TECHNOLOGY SECURITY
- TABLE 524 ICS SECURITY MARKET, BY COMPONENT, 2017-2022 (USD MILLION)
- TABLE 525 ICS SECURITY MARKET, BY COMPONENT, 2023-2028 (USD MILLION)
- TABLE 526 ICS SECURITY MARKET, BY SOLUTION, 2017-2022 (USD MILLION)
- TABLE 527 ICS SECURITY MARKET, BY SOLUTION, 2023-2028 (USD MILLION)
- TABLE 528 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY OFFERING, 2018-2023 (USD MILLION)
- TABLE 529 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY OFFERING, 2024-2029 (USD MILLION)
- TABLE 530 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SOLUTION, 2018-2023 (USD MILLION)
- TABLE 531 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SOLUTION, 2024-2029 (USD MILLION)
- TABLE 532 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY HARDWARE, 2018-2023 (USD MILLION)
- TABLE 533 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY HARDWARE, 2024-2029 (USD MILLION)
- TABLE 534 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SERVICE, 2018-2023 (USD MILLION)
- TABLE 535 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SERVICE, 2024-2029 (USD MILLION)
- TABLE 536 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SECURITY TYPE, 2018-2023 (USD MILLION)
- TABLE 537 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY SECURITY TYPE, 2024-2029 (USD MILLION)
- TABLE 538 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY VERTICAL, 2018-2023 (USD MILLION)
- TABLE 539 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY VERTICAL, 2024-2029 (USD MILLION)
- TABLE 540 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY REGION, 2018-2023 (USD BILLION)
- TABLE 541 CRITICAL INFRASTRUCTURE PROTECTION MARKET, BY REGION, 2024-2029 (USD BILLION)
List of Figures
- FIGURE 1 OPERATIONAL TECHNOLOGY SECURITY MARKET SEGMENTATION
- FIGURE 2 OPERATIONAL TECHNOLOGY SECURITY MARKET SEGMENTATION, BY REGION
- FIGURE 3 OPERATIONAL TECHNOLOGY SECURITY MARKET: RESEARCH DESIGN
- FIGURE 4 BREAKUP OF PRIMARY PROFILES, BY COMPANY TYPE, DESIGNATION, AND REGION
- FIGURE 5 KEY INSIGHTS FROM INDUSTRY EXPERTS
- FIGURE 6 OPERATIONAL TECHNOLOGY SECURITY MARKET ESTIMATION: RESEARCH FLOW
- FIGURE 7 APPROACH 1 (SUPPLY SIDE): REVENUE FROM SOLUTIONS/ SERVICES OF OPERATIONAL TECHNOLOGY SECURITY VENDORS
- FIGURE 8 APPROACH 2 (SUPPLY-SIDE ANALYSIS)
- FIGURE 9 APPROACH 2 (DEMAND SIDE): MARKET SIZE ESTIMATION METHODOLOGY (BOTTOM-UP) - PRODUCTS/SOLUTIONS/SERVICES
- FIGURE 10 DATA TRIANGULATION
- FIGURE 11 RESEARCH LIMITATIONS
- FIGURE 12 TIMELINE OF CYBERATTACKS ON OPERATIONAL TECHNOLOGY SYSTEMS, 2010-2023
- FIGURE 13 OPERATIONAL TECHNOLOGY SECURITY MARKET TO WITNESS SIGNIFICANT GROWTH DURING FORECAST PERIOD
- FIGURE 14 NORTH AMERICA TO ACCOUNT FOR LARGEST MARKET SHARE IN 2025
- FIGURE 15 INCREASING CYBER RISKS, REGULATORY PRESSURE, AND DIGITAL TRANSFORMATION ACROSS INDUSTRIES TO DRIVE MARKET
- FIGURE 16 OPERATIONAL TECHNOLOGY SECURITY MARKET: SEGMENTAL FORECAST
- FIGURE 17 NORTH AMERICA TO BE LARGEST MARKET DURING FORECAST PERIOD
- FIGURE 18 ASSET DISCOVERY & MANAGEMENT SEGMENT TO ACCOUNT FOR LARGEST MARKET SIZE DURING FORECAST PERIOD
- FIGURE 19 CONSULTING & INTEGRATION SEGMENT TO LEAD MARKET DURING FORECAST PERIOD
- FIGURE 20 ON-PREMISES SEGMENT TO LEAD MARKET DURING FORECAST PERIOD
- FIGURE 21 LARGE ENTERPRISES SEGMENT TO DOMINATE MARKET DURING FORECAST PERIOD
- FIGURE 22 MANUFACTURING SEGMENT TO LEAD MARKET DURING FORECAST PERIOD
- FIGURE 23 ASIA PACIFIC TO EMERGE AS BEST MARKET FOR INVESTMENTS IN NEXT FIVE YEARS
- FIGURE 24 OPERATIONAL TECHNOLOGY SECURITY MARKET: DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES
- FIGURE 25 EVOLUTION OF OPERATIONAL TECHNOLOGY SECURITY
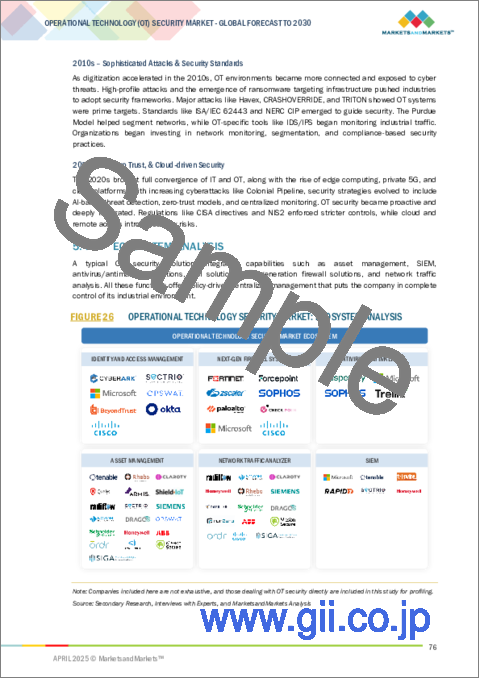
- FIGURE 26 OPERATIONAL TECHNOLOGY SECURITY MARKET: ECOSYSTEM ANALYSIS
- FIGURE 27 OPERATIONAL TECHNOLOGY SECURITY MARKET: VALUE CHAIN ANALYSIS
- FIGURE 28 OPERATIONAL TECHNOLOGY SECURITY MARKET: PATENTS APPLIED AND GRANTED, 2015-2025
- FIGURE 29 AVERAGE SELLING PRICE TREND OF KEY PLAYERS, BY SOLUTION TYPE (USD)
- FIGURE 30 OPERATIONAL TECHNOLOGY SECURITY MARKET: PORTER'S FIVE FORCES ANALYSIS
- FIGURE 31 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS
- FIGURE 32 KEY BUYING CRITERIA FOR TOP THREE VERTICALS
- FIGURE 33 OPERATIONAL TECHNOLOGY SECURITY MARKET: TRENDS AND DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- FIGURE 34 INVESTMENT IN LEADING GLOBAL OT SECURITY STARTUPS/SMES, BY NUMBER OF INVESTORS AND FUNDING (USD MILLION)
- FIGURE 35 NIST FRAMEWORK
- FIGURE 36 USE CASES OF GENERATIVE AI IN OPERATIONAL TECHNOLOGY SECURITY
- FIGURE 37 IMPACT OF GENERATIVE AI ON INTERCONNECTED AND ADJACENT ECOSYSTEMS
- FIGURE 38 SOLUTIONS SEGMENT TO DOMINATE MARKET DURING FORECAST PERIOD
- FIGURE 39 ASSET DISCOVERY & MANAGEMENT SEGMENT TO LEAD MARKET DURING FORECAST PERIOD
- FIGURE 40 CONSULTING & INTEGRATION SERVICES SEGMENT TO LEAD MARKET DURING FORECAST PERIOD
- FIGURE 41 ON-PREMISES SEGMENT TO DOMINATE MARKET DURING FORECAST PERIOD
- FIGURE 42 LARGE ENTERPRISES SEGMENT TO DOMINATE MARKET DURING FORECAST PERIOD
- FIGURE 43 MANUFACTURING SEGMENT TO LEAD MARKET DURING FORECAST PERIOD
- FIGURE 44 ASIA PACIFIC TO REGISTER HIGHEST GARD DURING FORECAST PERIOD
- FIGURE 45 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET SNAPSHOT
- FIGURE 46 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET SNAPSHOT
- FIGURE 47 SEGMENTAL REVENUE ANALYSIS OF TOP FIVE MARKET PLAYERS, 2020-2024 (USD MILLION)
- FIGURE 48 SHARE OF LEADING COMPANIES IN OPERATIONAL TECHNOLOGY SECURITY MARKET, 2024
- FIGURE 49 OPERATIONAL TECHNOLOGY SECURITY MARKET: COMPARISON OF VENDOR BRANDS
- FIGURE 50 COMPANY VALUATION OF KEY VENDORS, 2024 (USD BILLION)
- FIGURE 51 EV/EBIDTA, 2025
- FIGURE 52 OPERATIONAL TECHNOLOGY SECURITY MARKET: COMPANY EVALUATION MATRIX (KEY PLAYERS), 2024
- FIGURE 53 OPERATIONAL TECHNOLOGY SECURITY MARKET: COMPANY FOOTPRINT
- FIGURE 54 OPERATIONAL TECHNOLOGY SECURITY MARKET: COMPANY EVALUATION MATRIX (STARTUPS/SMES), 2024
- FIGURE 55 CISCO: COMPANY SNAPSHOT
- FIGURE 56 TENABLE: COMPANY SNAPSHOT
- FIGURE 57 MICROSOFT: COMPANY SNAPSHOT
- FIGURE 58 PALO ALTO NETWORKS: COMPANY SNAPSHOT
- FIGURE 59 FORTINET: COMPANY SNAPSHOT
- FIGURE 60 CHECK POINT: COMPANY SNAPSHOT
- FIGURE 61 BROADCOM: COMPANY SNAPSHOT
- FIGURE 62 OKTA: COMPANY SNAPSHOT
- FIGURE 63 QUALYS: COMPANY SNAPSHOT
- FIGURE 64 ZSCALER: COMPANY SNAPSHOT
- FIGURE 65 CYBERARK: COMPANY SNAPSHOT
- FIGURE 66 RAPID7: COMPANY SNAPSHOT
- FIGURE 67 SENTINELONE: COMPANY SNAPSHOT
- FIGURE 68 THALES: COMPANY SNAPSHOT
- FIGURE 69 HONEYWELL: COMPANY SNAPSHOT
- FIGURE 70 SCHNEIDER ELECTRIC: COMPANY SNAPSHOT
- FIGURE 71 SIEMENS: COMPANY SNAPSHOT
- FIGURE 72 ABB: COMPANY SNAPSHOT
The operational technology (OT) security market is projected to grow from USD 23.47 billion in 2025 to USD 50.29 billion by 2030 at a CAGR of 16.5% during the forecast period. Growing regulatory pressure is a major driver of the OT security market, as governments and industry bodies enforce stricter cybersecurity mandates to protect critical infrastructure. Regulations such as the NIS2 Directive in the EU, the US Cybersecurity Executive Order, and standards from bodies like NIST and IEC require organizations in sectors like energy, manufacturing, and transportation to implement robust OT security measures. Compliance with these regulations is pushing enterprises to invest in advanced solutions to secure their operational environments.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | USD (Billion) |
| Segments | By Offering, Deployment Mode, Organization Size, Vertical, and Region. |
| Regions covered | North America, Europe, Asia Pacific, Middle East & Africa, and Latin America |
"By vertical, the energy & power segment is projected to register the highest CAGR during the forecast period"
The energy & power sector is projected to register the highest CAGR in the OT security market due to its critical role and growing exposure to cyber threats. Increasing adoption of smart grids and digital systems raises the risk of attacks. For example, a recent ransomware attack on the interlinked power utility systems of Telangana and Andhra Pradesh in India led to a complete shutdown, highlighting the urgent need for robust OT cybersecurity in this sector.
"By region, North America is estimated to account for the largest market share in 2025"
North America accounts for a larger share of the OT security market due to the high adoption of advanced technologies, increased cyber threat awareness, and stringent regulatory requirements. The region's industrial sectors, including energy, manufacturing, and transportation, are heavily investing in OT security to protect critical infrastructure. Additionally, the presence of key market players such as Fortinet, Cisco, and Trellix and continuous innovation in cybersecurity solutions further contribute to North America's dominant position in the global OT security market.
Breakdown of primaries
The study contains insights from various industry experts, from component suppliers to Tier 1 companies and OEMs. The break-up of the primaries is as follows:
- By Company Type: Tier 1 - 40%, Tier 2 - 35%, and Tier 3 - 25%
- By Designation: C-level - 45%, Directors - 35%, and Managers - 20%
- By Region: North America - 55%, Europe - 25%, Asia Pacific - 15%, RoW - 5%
The key players in the OT security market include Fortinet (US), Forcepoint (US), Cisco (US), Tenable (US), Forescout (US), Check Point (Israel), Broadcom (US), Trellix (US), Microsoft (US), Okta (US), Palo Alto Networks (US), Tosibox (Finland), Zscaler (US), Rapid7 (US), and others.
The study includes an in-depth competitive analysis of the key players in the OT security market, their company profiles, recent developments, and key market strategies.
Research Coverage
The report segments the OT security market and forecasts its size by Offering [Solutions (Security Information & Event Management (SIEM), Asset Discovery & Management, Network Security, Vulnerability Management, Identity & Access Management (IAM), Data Security, and Other Solutions) and Services (Consulting & Integration, Support & Maintenance, Training & Development Services, Incident Response Services, and Managed Security Services)], Deployment Mode [Cloud and On-premises], Organization Size [Large Enterprises and SMEs], Vertical [Transportation & Logistics, Manufacturing, Energy & Power, Oil & Gas, and Other Verticals], and Region [North America, Europe, Asia Pacific, Middle East & Africa, and Latin America].
The study also includes an in-depth competitive analysis of the market's key players, their company profiles, key observations related to product and business offerings, recent developments, and key market strategies.
Key Benefits of Buying the Report
The report will help the market leaders/new entrants with information on the closest approximations of the revenue numbers for the overall OT security market and the subsegments. This report will help stakeholders understand the competitive landscape and gain more insights to position their businesses better and plan suitable go-to-market strategies. The report also helps stakeholders understand the market pulse and provides information on key market drivers, restraints, challenges, and opportunities.
The report provides insights on the following pointers:
- Analysis of key drivers (increase in threats to OT environments, organizations embracing digital transformation, stringent government regulations related to adoption of OT systems, and convergence of OT and IT networks), restraints (high procurement costs, emerging challenges related to maintenance and upgrades, and interoperability and standardization challenges), opportunities (increase in adoption of AI-powered security solutions, technological advancements in cybersecurity, and need for secure OT networks), and challenges (lack of trained security analysts, lack of awareness about OT security techniques, and complexity pertaining to OT environments)
- Product Development/Innovation: Detailed insights on upcoming technologies, research & development activities, and new product & service launches in the OT security market.
- Market Development: Comprehensive information about lucrative markets - the report analyses the OT security market across varied regions.
- Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the OT security market.
- Competitive Assessment: In-depth assessment of market shares, growth strategies, and service offerings of leading players such as Fortinet (US), Forcepoint (US), Cisco (US), Tenable (US), Forescout (US), Seckiot (France), Check Point (Israel), Broadcom (US), Trellix (US), Microsoft (US), Okta (US), Palo Alto Networks (US), Qualys (US), Zscaler (US), BeyondTrust (US), CyberArk (US), Rapid7 (US), Sophos (UK), Tripwire (US), Radiflow (Israel), Kaspersky (Russia), SentinelOne (US), Thales (France), Armis (US), Darktrace (UK), Nozomi Networks (US), Honeywell (US), Schneider Electric (France), Siemens (Germany), ABB (Switzerland), Tosibox (Finland), Rhebo (Germany), Shield-IoT (Israel), Claroty (US), Dragos (US), Cydome (Israel), Ordr (US), Mission Secure (US), runZero (US), SIGA OT Solutions (US), Sectrio (US), Waterfall Security Solutions (Israel), and Opswat (US) among others, in the OT security market strategies.
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.2.1 INCLUSIONS AND EXCLUSIONS
- 1.3 MARKET SCOPE
- 1.3.1 MARKET COVERED
- 1.3.2 REGIONS COVERED
- 1.3.3 YEARS CONSIDERED
- 1.4 CURRENCY CONSIDERED
- 1.5 STAKEHOLDERS
- 1.6 SUMMARY OF CHANGES
2 RESEARCH METHODOLOGY
- 2.1 RESEARCH DATA
- 2.1.1 SECONDARY DATA
- 2.1.2 PRIMARY DATA
- 2.1.2.1 Breakup of primary profiles
- 2.1.2.2 Key industry insights
- 2.2 MARKET SIZE ESTIMATION
- 2.2.1 TOP-DOWN APPROACH
- 2.2.2 BOTTOM-UP APPROACH
- 2.3 DATA TRIANGULATION
- 2.4 MARKET FORECAST
- 2.5 RESEARCH ASSUMPTIONS
- 2.6 RESEARCH LIMITATIONS
3 EXECUTIVE SUMMARY
4 PREMIUM INSIGHTS
- 4.1 ATTRACTIVE OPPORTUNITIES FOR PLAYERS IN OPERATIONAL TECHNOLOGY SECURITY MARKET
- 4.2 OPERATIONAL TECHNOLOGY SECURITY MARKET FORECAST
- 4.3 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION
- 4.4 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SOLUTION
- 4.5 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY SERVICE
- 4.6 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE
- 4.7 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE
- 4.8 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL
- 4.9 MARKET INVESTMENT SCENARIO
5 MARKET OVERVIEW AND INDUSTRY TRENDS
- 5.1 INTRODUCTION
- 5.2 MARKET DYNAMICS
- 5.2.1 DRIVERS
- 5.2.1.1 Increased threats to OT environments
- 5.2.1.2 Stringent government regulations related to OT systems adoption
- 5.2.1.3 Convergence of OT and IT networks
- 5.2.1.4 Need for secure OT networks
- 5.2.2 RESTRAINTS
- 5.2.2.1 High procurement costs
- 5.2.2.2 Emerging challenges related to maintenance and upgrades
- 5.2.2.3 Interoperability and standardization challenges
- 5.2.3 OPPORTUNITIES
- 5.2.3.1 Increasing adoption of AI-powered security solutions
- 5.2.3.2 Technological advancements in cybersecurity
- 5.2.3.3 Digital transformation across organizations
- 5.2.3.4 Rising demand for Industry 4.0 and smart infrastructure
- 5.2.4 CHALLENGES
- 5.2.4.1 Lack of trained security analysts
- 5.2.4.2 Lack of awareness about OT security techniques
- 5.2.4.3 Complexity pertaining to OT environments
- 5.2.1 DRIVERS
- 5.3 EVOLUTION OF OPERATIONAL TECHNOLOGY SECURITY
- 5.4 ECOSYSTEM ANALYSIS
- 5.5 VALUE CHAIN ANALYSIS
- 5.5.1 PROVIDERS OF OT SECURITY SOLUTIONS AND TOOLS
- 5.5.2 SERVICE PROVIDERS
- 5.5.3 SYSTEM INTEGRATORS
- 5.5.4 RETAIL/DISTRIBUTION
- 5.5.5 END USERS
- 5.6 TECHNOLOGY ANALYSIS
- 5.6.1 KEY TECHNOLOGIES
- 5.6.1.1 Network security
- 5.6.1.2 Endpoint security
- 5.6.1.3 Identity and access management (IAM)
- 5.6.2 COMPLEMENTARY TECHNOLOGIES
- 5.6.2.1 Security information and event management (SIEM)
- 5.6.2.2 Vulnerability management
- 5.6.3 ADJACENT TECHNOLOGIES
- 5.6.3.1 Artificial intelligence (AI) and machine learning (ML)
- 5.6.3.2 Blockchain
- 5.6.3.3 Internet of Things (IoT)
- 5.6.1 KEY TECHNOLOGIES
- 5.7 REGULATORY LANDSCAPE
- 5.7.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- 5.7.2 KEY REGULATIONS
- 5.7.2.1 Payment Card Industry Data Security Standard (PCI-DSS)
- 5.7.2.2 Health Insurance Portability and Accountability Act (HIPAA)
- 5.7.2.3 Federal Information Security Management Act (FISMA)
- 5.7.2.4 Gramm-Leach-Bliley Act (GLBA)
- 5.7.2.5 California's Privacy Rights Act (CPRA)
- 5.7.2.6 ISO 27001
- 5.7.2.7 General Data Protection Regulation
- 5.7.2.8 Sarbanes-Oxley ACT
- 5.7.2.9 SOC 2
- 5.8 PATENT ANALYSIS
- 5.9 PRICING ANALYSIS
- 5.9.1 AVERAGE SELLING PRICE TREND OF KEY PLAYERS, BY SOLUTION TYPE
- 5.9.2 INDICATIVE PRICING ANALYSIS OF KEY OT SECURITY VENDORS, BY OFFERING
- 5.10 PORTER'S FIVE FORCES ANALYSIS
- 5.10.1 THREAT OF NEW ENTRANTS
- 5.10.2 THREAT OF SUBSTITUTES
- 5.10.3 BARGAINING POWER OF SUPPLIERS
- 5.10.4 BARGAINING POWER OF BUYERS
- 5.10.5 INTENSITY OF COMPETITIVE RIVALRY
- 5.11 KEY STAKEHOLDERS AND BUYING CRITERIA
- 5.11.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 5.11.2 BUYING CRITERIA
- 5.12 OPERATIONAL TECHNOLOGY SECURITY ATTACKS, 2023-2024
- 5.13 CASE STUDIES
- 5.13.1 CALIFORNIA WATER AND WASTEWATER DISTRICT LEVERAGED FORTINET SOLUTIONS FOR BETTER NETWORK MANAGEMENT
- 5.13.2 INTERNATIONAL PLASTICS MANUFACTURER IMPROVED OT VISIBILITY AND REDUCED RISK
- 5.13.3 ZSCALER HELPED CALIFORNIA DAIRIES TRANSITION TO CLOUD-BASED ENVIRONMENT
- 5.13.4 HAURAKI DISTRICT COUNCIL SECURES CRITICAL INFRASTRUCTURE AND MANAGES THIRD-PARTY RISK WITH DARKTRACE AI
- 5.13.5 KEYSIGHT ENABLES COMPREHENSIVE OT SECURITY FOR MEXICAN MINING LEADER
- 5.14 TRENDS AND DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- 5.15 KEY CONFERENCES AND EVENTS, 2025-2026
- 5.16 INVESTMENT AND FUNDING SCENARIO, 2021-2024
- 5.17 NIST FRAMEWORK
- 5.17.1 INTRODUCTION TO NIST FRAMEWORK
- 5.17.2 IDENTITY
- 5.17.3 PROTECT
- 5.17.4 DEFEND
- 5.17.5 DETECT
- 5.17.6 RESPOND & RECOVER
- 5.18 OPERATIONAL TECHNOLOGY SECURITY MARKET: TECHNOLOGY ROADMAP
- 5.19 BUSINESS MODELS OF OPERATIONAL TECHNOLOGY SECURITY
- 5.19.1 MANAGED SECURITY SERVICES (MSS)
- 5.19.2 SECURITY AND SOLUTIONS
- 5.19.3 SECURITY CONSULTING
- 5.20 IMPACT OF AI/GENERATIVE AI ON OPERATIONAL TECHNOLOGY SECURITY MARKET
- 5.20.1 USE CASES OF GENERATIVE AI IN OPERATIONAL TECHNOLOGY SECURITY
- 5.20.2 IMPACT OF GENERATIVE AI ON INTERCONNECTED AND ADJACENT ECOSYSTEMS
- 5.20.2.1 Enhanced Threat Detection and Response Across IT/OT Boundaries
- 5.20.2.2 Securing the Expanding Attack Surface of IIoT and Smart Infrastructure
- 5.20.2.3 Strengthening Supply Chain Security in OT
- 5.20.2.4 Addressing the IT/OT Skills Gap Through AI Augmentation
- 5.20.2.5 Impact on Adjacent Cybersecurity Markets
- 5.20.2.6 Evolving Threat Landscape
6 IMPACT OF 2025 US TARIFF - OPERATIONAL TECHNOLOGY SECURITY MARKET
- 6.1 INTRODUCTION
- 6.2 KEY TARIFF RATES
- 6.3 PRICE IMPACT ANALYSIS
- 6.4 IMPACT ON COUNTRY/REGION
- 6.4.1 NORTH AMERICA
- 6.4.2 US
- 6.4.3 CANADA
- 6.4.4 MEXICO
- 6.4.5 MARKET CHALLENGES:
- 6.4.6 MITIGATION MEASURES:
- 6.4.7 EUROPE
- 6.4.8 GERMANY
- 6.4.9 FRANCE
- 6.4.10 UK
- 6.4.11 MARKET CHALLENGES:
- 6.4.12 MITIGATION MEASURES:
- 6.4.13 ASIA PACIFIC
- 6.4.14 CHINA
- 6.4.15 INDIA
- 6.4.16 AUSTRALIA
- 6.4.17 MARKET CHALLENGES:
- 6.4.18 MITIGATION MEASURES:
- 6.5 IMPACT ON END-USE INDUSTRIES
7 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY OFFERING
- 7.1 INTRODUCTION
- 7.1.1 OFFERING: OPERATIONAL TECHNOLOGY SECURITY MARKET DRIVERS
- 7.2 SOLUTIONS
- 7.2.1 SECURITY INFORMATION & EVENT MANAGEMENT (SIEM)
- 7.2.1.1 Growth in threat landscape targeting industrial systems to drive demand
- 7.2.2 ASSET DISCOVERY & MANAGEMENT
- 7.2.2.1 Increasingly interconnected and digitized OT environments to drive demand
- 7.2.3 NETWORK SECURITY
- 7.2.3.1 Need to protect critical infrastructure to drive demand
- 7.2.4 VULNERABILITY MANAGEMENT
- 7.2.4.1 Increasing connectivity and digitization of industrial processes to drive demand
- 7.2.5 IDENTITY & ACCESS MANAGEMENT (IAM)
- 7.2.5.1 Need to prevent unauthorized access to critical OT assets to drive demand
- 7.2.6 DATA SECURITY
- 7.2.6.1 Need to protect sensitive OT data while ensuring operational continuity, safety, and regulatory compliance to drive demand
- 7.2.7 OTHER SOLUTIONS
- 7.2.1 SECURITY INFORMATION & EVENT MANAGEMENT (SIEM)
- 7.3 SERVICES
- 7.3.1 CONSULTING & INTEGRATION SERVICES
- 7.3.1.1 Emergence of advanced threats and shortage of cloud computing security skills to drive demand
- 7.3.2 SUPPORT & MAINTENANCE SERVICES
- 7.3.2.1 Rising adoption of complex security solutions to drive demand
- 7.3.3 TRAINING & DEVELOPMENT SERVICES
- 7.3.3.1 Rising convergence of IT and OT systems to drive demand
- 7.3.4 INCIDENT RESPONSE SERVICES
- 7.3.4.1 Focus on identifying and preventing attacks on OT security systems to drive demand
- 7.3.5 MANAGED SECURITY SERVICES
- 7.3.5.1 Requirement for network assessment, vulnerability analysis, and live monitoring to drive demand
- 7.3.1 CONSULTING & INTEGRATION SERVICES
8 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY DEPLOYMENT MODE
- 8.1 INTRODUCTION
- 8.1.1 DEPLOYMENT MODE: OPERATIONAL TECHNOLOGY SECURITY MARKET DRIVERS
- 8.2 CLOUD
- 8.2.1 REQUIREMENT FOR FLEXIBILITY, SCALABILITY, AND COST REDUCTION TO DRIVE DEMAND
- 8.3 ON-PREMISES
- 8.3.1 PREFERENCE FOR HIGH SECURITY AND CONTROL OVER DATA TO DRIVE DEMAND
9 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY ORGANIZATION SIZE
- 9.1 INTRODUCTION
- 9.1.1 ORGANIZATION SIZE: OPERATIONAL TECHNOLOGY SECURITY MARKET DRIVERS
- 9.2 SMES
- 9.2.1 HIGHER VULNERABILITY TO CYBERATTACKS TO DRIVE INVESTMENTS IN DIGITAL SECURITY SYSTEMS
- 9.3 LARGE ENTERPRISES
- 9.3.1 AMPLE BUDGETS AND INCREASING FOCUS ON SECURING DATA MOVEMENT AND STORAGE TO DRIVE MARKET
10 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY VERTICAL
- 10.1 INTRODUCTION
- 10.1.1 VERTICAL: OPERATIONAL TECHNOLOGY SECURITY MARKET DRIVERS
- 10.2 TRANSPORTATION & LOGISTICS
- 10.2.1 INCREASING RELIANCE ON DIGITAL SYSTEMS FOR ENHANCED EFFICIENCY AND CUSTOMER SATISFACTION TO DRIVE MARKET
- 10.2.2 TRANSPORTATION & LOGISTICS: OPERATIONAL TECHNOLOGY SECURITY USE CASES
- 10.2.2.1 Supervisory control and data acquisition (SCADA) security
- 10.2.2.2 Fleet management security
- 10.2.2.3 Logistics automation security
- 10.2.2.4 Supply chain security
- 10.2.2.5 Port and terminal security
- 10.2.2.6 Aviation security
- 10.3 MANUFACTURING
- 10.3.1 NEED TO PREVENT PRODUCTION DISRUPTIONS AND DATA BREACHES TO DRIVE MARKET
- 10.3.2 MANUFACTURING: OPERATIONAL TECHNOLOGY SECURITY USE CASES
- 10.3.2.1 Supervisory control and data acquisition (SCADA) security
- 10.3.2.2 Industrial IoT (IIoT) devices security
- 10.3.2.3 Manufacturing execution systems (MES) security
- 10.3.2.4 Robotics and automation security
- 10.3.2.5 Supply chain integration security
- 10.3.2.6 Plant floor network security
- 10.4 ENERGY & POWER
- 10.4.1 NEED TO SAFEGUARD CRITICAL INFRASTRUCTURE AND MINIMIZE DISRUPTIONS TO DRIVE MARKET
- 10.4.2 ENERGY & POWER: OPERATIONAL TECHNOLOGY SECURITY USE CASES
- 10.4.2.1 Supervisory control and data acquisition(SCADA) security
- 10.4.2.2 Industrial control systems (ICS) security
- 10.4.2.3 Smart grid security
- 10.4.2.4 Renewable energy systems security
- 10.4.2.5 Energy management systems (EMS) security
- 10.5 OIL & GAS
- 10.5.1 FOCUS ON ENHANCING DIGITAL RESILIENCE AND REDUCING CYBER THREATS TO DRIVE MARKET
- 10.5.2 OIL & GAS: OPERATIONAL TECHNOLOGY SECURITY USE CASES
- 10.5.2.1 Supervisory control and data acquisition (SCADA) security
- 10.5.2.2 Industrial control systems (ICS) security
- 10.5.2.3 Pipeline monitoring and control security
- 10.5.2.4 Terminal automation security
- 10.6 OTHER VERTICALS
11 OPERATIONAL TECHNOLOGY SECURITY MARKET, BY REGION
- 11.1 INTRODUCTION
- 11.2 NORTH AMERICA
- 11.2.1 NORTH AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET DRIVERS
- 11.2.2 NORTH AMERICA: MACROECONOMIC OUTLOOK
- 11.2.3 US
- 11.2.3.1 High digitalization and significant investment in modernizing legacy infrastructure to drive market
- 11.2.4 CANADA
- 11.2.4.1 Surge in cyberattacks and increasing focus on OT security investment to drive market
- 11.3 EUROPE
- 11.3.1 EUROPE: OPERATIONAL TECHNOLOGY SECURITY MARKET DRIVERS
- 11.3.2 EUROPE: MACROECONOMIC OUTLOOK
- 11.3.3 UK
- 11.3.3.1 Emphasis on strong regulatory enforcement to spur OT security adoption
- 11.3.4 GERMANY
- 11.3.4.1 IT-SiG 2.0 law mandating stricter compliance and cyber hygiene to elevate demand for OT security solutions
- 11.3.5 ITALY
- 11.3.5.1 Increasing focus on safeguarding interconnected industrial operations to drive market
- 11.3.6 FRANCE
- 11.3.6.1 Rising cyber threats targeting and convergence of IT and OT environments to boost market
- 11.3.7 FINLAND
- 11.3.7.1 Smart grid expansion to drive demand for OT security solutions
- 11.3.8 SWEDEN
- 11.3.8.1 Smart city projects to trigger investment in OT security
- 11.3.9 BENELUX
- 11.3.9.1 Increasing cyber threats targeting port operations, public infrastructure, and finance-related industrial systems to drive market
- 11.3.10 SPAIN
- 11.3.10.1 Rising infrastructure threats to trigger OT modernization
- 11.3.11 PORTUGAL
- 11.3.11.1 Government-led cyber strategy to expand OT awareness
- 11.3.12 DENMARK
- 11.3.12.1 Focus on smart energy and offshore wind power to drive OT security demand
- 11.3.13 NORWAY
- 11.3.13.1 Rising oil & gas cyber threats to spur national OT defense strategy
- 11.3.14 AUSTRIA
- 11.3.14.1 Increasing cyberattacks on healthcare and transportation infrastructure to drive market
- 11.3.15 SWITZERLAND
- 11.3.15.1 Infrastructure modernization in industrial automation, energy distribution, and smart factories to drive market
- 11.3.16 REST OF EUROPE
- 11.4 ASIA PACIFIC
- 11.4.1 ASIA PACIFIC: OPERATIONAL TECHNOLOGY SECURITY MARKET DRIVERS
- 11.4.2 ASIA PACIFIC: MACROECONOMIC OUTLOOK
- 11.4.3 CHINA
- 11.4.3.1 Stricter government guidelines for industrial control systems to drive market
- 11.4.4 JAPAN
- 11.4.4.1 Financial incentives and tax exemptions to encourage investment and propel market expansion
- 11.4.5 INDIA
- 11.4.5.1 Increasing adoption of connected devices and systems to drive market
- 11.4.6 REST OF ASIA PACIFIC
- 11.5 MIDDLE EAST & AFRICA
- 11.5.1 MIDDLE EAST & AFRICA: OPERATIONAL TECHNOLOGY SECURITY MARKET DRIVERS
- 11.5.2 MIDDLE EAST & AFRICA: MACROECONOMIC OUTLOOK
- 11.5.3 GULF COOPERATION COUNCIL (GCC)
- 11.5.3.1 KSA
- 11.5.3.1.1 Vision 2030 and push for smart infrastructure to drive market
- 11.5.3.2 UAE
- 11.5.3.2.1 Strategic public-private partnerships to fuel cyber innovation and drive OT security demand
- 11.5.3.3 Rest of GCC
- 11.5.3.1 KSA
- 11.5.4 SOUTH AFRICA
- 11.5.4.1 Active promotion of cybersecurity standards and guidelines by regulatory bodies and government agencies to drive market
- 11.5.5 REST OF MIDDLE EAST & AFRICA
- 11.6 LATIN AMERICA
- 11.6.1 LATIN AMERICA: OPERATIONAL TECHNOLOGY SECURITY MARKET DRIVERS
- 11.6.2 LATIN AMERICA: MACROECONOMIC OUTLOOK
- 11.6.3 MEXICO
- 11.6.3.1 Strategic investment in industrial SOCs and incident response to drive market
- 11.6.4 BRAZIL
- 11.6.4.1 Rising ICS malware threats to drive market
- 11.6.5 REST OF LATIN AMERICA
12 COMPETITIVE LANDSCAPE
- 12.1 KEY PLAYER STRATEGIES/RIGHT TO WIN, 2022-2024
- 12.2 REVENUE ANALYSIS, 2020-2024
- 12.3 MARKET SHARE ANALYSIS, 2024
- 12.4 BRAND COMPARISON
- 12.4.1 CISCO
- 12.4.2 TENABLE
- 12.4.3 MICROSOFT
- 12.4.4 FORCEPOINT
- 12.4.5 PALO ALTO NETWORKS
- 12.5 COMPANY VALUATION AND FINANCIAL METRICS
- 12.5.1 COMPANY VALUATION, 2024
- 12.5.2 FINANCIAL METRICS USING EV/EBIDTA
- 12.6 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 12.6.1 STARS
- 12.6.2 EMERGING LEADERS
- 12.6.3 PERVASIVE PLAYERS
- 12.6.4 PARTICIPANTS
- 12.6.5 COMPANY FOOTPRINT: KEY PLAYERS, 2024
- 12.6.5.1 Company footprint
- 12.6.5.2 Region footprint
- 12.6.5.3 Offering footprint
- 12.6.5.4 Vertical footprint
- 12.7 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 12.7.1 PROGRESSIVE COMPANIES
- 12.7.2 RESPONSIVE COMPANIES
- 12.7.3 DYNAMIC COMPANIES
- 12.7.4 STARTING BLOCKS
- 12.7.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES, 2024
- 12.7.5.1 Detailed list of key startups/SMEs
- 12.7.5.2 Competitive benchmarking of key startups
- 12.8 COMPETITIVE SCENARIO
- 12.8.1 PRODUCT LAUNCHES/ENHANCEMENTS
- 12.8.2 DEALS
13 COMPANY PROFILES
- 13.1 INTRODUCTION
- 13.2 KEY PLAYERS
- 13.2.1 CISCO
- 13.2.1.1 Business overview
- 13.2.1.2 Products/Solutions/Services offered
- 13.2.1.3 Recent developments
- 13.2.1.3.1 Product launches/enhancements
- 13.2.1.3.2 Deals
- 13.2.1.4 MnM view
- 13.2.1.4.1 Key strengths
- 13.2.1.4.2 Strategic choices
- 13.2.1.4.3 Weaknesses and competitive threats
- 13.2.2 TENABLE
- 13.2.2.1 Business overview
- 13.2.2.2 Products/Solutions/Services offered
- 13.2.2.3 Recent developments
- 13.2.2.3.1 Product launches/enhancements
- 13.2.2.3.2 Deals
- 13.2.2.4 MnM view
- 13.2.2.4.1 Key strengths
- 13.2.2.4.2 Strategic choices
- 13.2.2.4.3 Weaknesses and competitive threats
- 13.2.3 MICROSOFT
- 13.2.3.1 Business overview
- 13.2.3.2 Products/Solutions/Services offered
- 13.2.3.3 Recent developments
- 13.2.3.3.1 Product launches/enhancements
- 13.2.3.3.2 Deals
- 13.2.3.4 MnM view
- 13.2.3.4.1 Key strengths
- 13.2.3.4.2 Strategic choices
- 13.2.3.4.3 Weaknesses and competitive threats
- 13.2.4 FORCEPOINT
- 13.2.4.1 Business overview
- 13.2.4.2 Products/Solutions/Services offered
- 13.2.4.3 Recent developments
- 13.2.4.3.1 Product launches/enhancements
- 13.2.4.3.2 Deals
- 13.2.4.3.3 Other developments
- 13.2.4.4 MnM view
- 13.2.4.4.1 Key strengths
- 13.2.4.4.2 Strategic choices
- 13.2.4.4.3 Weaknesses and competitive threats
- 13.2.5 PALO ALTO NETWORKS
- 13.2.5.1 Business overview
- 13.2.5.2 Products/Solutions/Services offered
- 13.2.5.3 Recent developments
- 13.2.5.3.1 Product launches/enhancements
- 13.2.5.3.2 Deals
- 13.2.5.4 MnM view
- 13.2.5.4.1 Key strengths
- 13.2.5.4.2 Strategic choices
- 13.2.5.4.3 Weaknesses and competitive threats
- 13.2.6 FORTINET
- 13.2.6.1 Business overview
- 13.2.6.2 Products/Solutions/Services offered
- 13.2.6.3 Recent developments
- 13.2.6.3.1 Product launches/enhancements
- 13.2.6.3.2 Deals
- 13.2.7 FORESCOUT
- 13.2.7.1 Business overview
- 13.2.7.2 Products/Solutions/Services offered
- 13.2.7.3 Recent developments
- 13.2.7.3.1 Product launches/enhancements
- 13.2.7.3.2 Deals
- 13.2.8 SECKIOT
- 13.2.8.1 Business overview
- 13.2.8.2 Products/Solutions/Services offered
- 13.2.9 CHECK POINT
- 13.2.9.1 Business overview
- 13.2.9.2 Products/Solutions/Services offered
- 13.2.9.3 Recent developments
- 13.2.9.3.1 Product launches/enhancements
- 13.2.9.3.2 Deals
- 13.2.10 BROADCOM
- 13.2.10.1 Business overview
- 13.2.10.2 Products/Solutions/Services offered
- 13.2.10.3 Recent developments
- 13.2.10.3.1 Product launches/enhancements
- 13.2.10.3.2 Deals
- 13.2.11 TRELLIX
- 13.2.11.1 Business overview
- 13.2.11.2 Products/Solutions/Services offered
- 13.2.11.3 Recent developments
- 13.2.11.3.1 Product launches/enhancements
- 13.2.11.3.2 Deals
- 13.2.12 OKTA
- 13.2.12.1 Business overview
- 13.2.12.2 Products/Solutions/Services offered
- 13.2.12.3 Recent developments
- 13.2.12.3.1 Product launches/enhancements
- 13.2.12.3.2 Deals
- 13.2.13 QUALYS
- 13.2.13.1 Business overview
- 13.2.13.2 Products/Solutions/Services offered
- 13.2.13.3 Recent developments
- 13.2.13.3.1 Product launches/enhancements
- 13.2.13.3.2 Deals
- 13.2.14 ZSCALER
- 13.2.14.1 Business overview
- 13.2.14.2 Products/Solutions/Services offered
- 13.2.14.3 Recent developments
- 13.2.14.3.1 Product launches/enhancements
- 13.2.14.3.2 Deals
- 13.2.15 BEYONDTRUST
- 13.2.15.1 Business overview
- 13.2.15.2 Products/Solutions/Services offered
- 13.2.15.3 Recent developments
- 13.2.15.3.1 Product launches/enhancements
- 13.2.15.3.2 Deals
- 13.2.16 CYBERARK
- 13.2.16.1 Business overview
- 13.2.16.2 Products/Solutions/Services offered
- 13.2.16.3 Recent developments
- 13.2.16.3.1 Product launches/enhancements
- 13.2.16.3.2 Deals
- 13.2.17 RAPID7
- 13.2.17.1 Business overview
- 13.2.17.2 Products/Solutions/Services offered
- 13.2.17.3 Recent developments
- 13.2.17.3.1 Product launches/enhancements
- 13.2.17.3.2 Deals
- 13.2.18 SOPHOS
- 13.2.18.1 Business overview
- 13.2.18.2 Products/Solutions/Services offered
- 13.2.18.3 Recent developments
- 13.2.18.3.1 Product launches/enhancements
- 13.2.18.3.2 Deals
- 13.2.19 TRIPWIRE
- 13.2.19.1 Business overview
- 13.2.19.2 Products/Solutions/Services offered
- 13.2.19.3 Recent developments
- 13.2.19.3.1 Product launches/enhancements
- 13.2.19.3.2 Deals
- 13.2.20 RADIFLOW
- 13.2.20.1 Business overview
- 13.2.20.2 Products/Solutions/Services offered
- 13.2.20.3 Recent developments
- 13.2.20.3.1 Product launches/enhancements
- 13.2.20.3.2 Deals
- 13.2.21 KASPERSKY
- 13.2.21.1 Business overview
- 13.2.21.2 Products/Solutions/Services offered
- 13.2.21.3 Recent developments
- 13.2.21.3.1 Product launches/enhancements
- 13.2.21.3.2 Deals
- 13.2.22 SENTINELONE
- 13.2.22.1 Business overview
- 13.2.22.2 Products/Solutions/Services offered
- 13.2.22.3 Recent developments
- 13.2.22.3.1 Product launches/enhancements
- 13.2.22.3.2 Deals
- 13.2.23 THALES
- 13.2.23.1 Business overview
- 13.2.23.2 Products/Solutions/Services offered
- 13.2.23.3 Recent developments
- 13.2.23.3.1 Deals
- 13.2.24 ARMIS
- 13.2.24.1 Business overview
- 13.2.24.2 Products/Solutions/Services offered
- 13.2.24.3 Recent developments
- 13.2.24.3.1 Deals
- 13.2.25 DARKTRACE
- 13.2.25.1 Business overview
- 13.2.25.2 Products/Solutions/Services offered
- 13.2.25.3 Recent developments
- 13.2.25.3.1 Product launches/enhancements
- 13.2.25.3.2 Deals
- 13.2.26 NOZOMI NETWORKS
- 13.2.26.1 Business overview
- 13.2.26.2 Products/Solutions/Services offered
- 13.2.26.3 Recent developments
- 13.2.26.3.1 Product launches/enhancements
- 13.2.26.3.2 Deals
- 13.2.27 HONEYWELL
- 13.2.27.1 Business overview
- 13.2.27.2 Products/Solutions/Services offered
- 13.2.27.3 Recent developments
- 13.2.27.3.1 Product launches/enhancements
- 13.2.27.3.2 Deals
- 13.2.28 SCHNEIDER ELECTRIC
- 13.2.28.1 Business overview
- 13.2.28.2 Products/Solutions/Services offered
- 13.2.28.3 Recent developments
- 13.2.28.3.1 Product launches/enhancements
- 13.2.28.3.2 Deals
- 13.2.29 SIEMENS
- 13.2.29.1 Business overview
- 13.2.29.2 Products/Solutions/Services offered
- 13.2.29.3 Recent developments
- 13.2.29.3.1 Deals
- 13.2.30 ABB
- 13.2.30.1 Business overview
- 13.2.30.2 Products/Solutions/Services offered
- 13.2.30.3 Recent developments
- 13.2.30.3.1 Deals
- 13.2.31 TOSIBOX
- 13.2.31.1 Business overview
- 13.2.31.2 Products/Solutions/Services offered
- 13.2.31.3 Recent developments
- 13.2.31.3.1 Product launches/enhancements
- 13.2.31.3.2 Deals
- 13.2.31.3.3 Expansions
- 13.2.1 CISCO
- 13.3 OTHER PLAYERS
- 13.3.1 RHEBO
- 13.3.2 SHIELD-IOT
- 13.3.3 CLAROTY
- 13.3.4 DRAGOS
- 13.3.5 CYDOME
- 13.3.6 MISSION SECURE
- 13.3.7 ORDR
- 13.3.8 RUNZERO
- 13.3.9 SIGA OT SOLUTIONS
- 13.3.10 SECTRIO
- 13.3.11 WATERFALL SECURITY
- 13.3.12 OPSWAT
14 ADJACENT MARKETS
- 14.1 INTRODUCTION TO ADJACENT MARKETS
- 14.2 LIMITATIONS
- 14.3 ICS SECURITY MARKET
- 14.4 CRITICAL INFRASTRUCTURE PROTECTION MARKET
15 APPENDIX
- 15.1 DISCUSSION GUIDE
- 15.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 15.3 CUSTOMIZATION OPTIONS
- 15.4 RELATED REPORTS
- 15.5 AUTHOR DETAILS