
|
市場調査レポート
商品コード
1556132
サイバーセキュリティの世界市場 (2024~2034年)Global Cybersecurity Market 2024-2034 |
||||||
|
|||||||
| サイバーセキュリティの世界市場 (2024~2034年) |
|
出版日: 2024年09月16日
発行: Aviation & Defense Market Reports (A&D)
ページ情報: 英文 150+ Pages
納期: 3営業日
|
全表示
- 概要
- 図表
- 目次
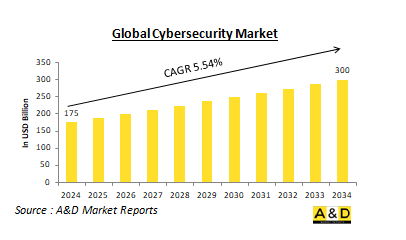
世界のサイバーセキュリティ市場は、2024年に1,750億米ドルに達し、予測期間中 (2024~2034年) のCAGRは5.54%と推定され、3,000億米ドルに成長すると予測されています。
世界のサイバーセキュリティ市場の概要
世界のサイバーセキュリティ防衛とは、デジタル資産や重要インフラ、機密情報をサイバー脅威から守るための国家・組織・個人の総合的な取り組みを指します。相互接続が進む世界では、サイバーセキュリティは政府や企業にとって最優先事項となっています。サイバーセキュリティは、機密情報へのアクセス、変更、破壊、金銭の恐喝、通常業務の妨害などを目的とするハッカー・スパマー・サイバー犯罪者による悪質な攻撃から身を守るために不可欠です。このような脅威は、サイバー犯罪とともにより巧妙になり、広範囲に広がっています。その結果、政府や組織はデジタル資産を保護し、利害関係者の信頼を維持するために、高度なサイバーセキュリティ技術と戦略に多額の投資を行っています。
世界のサイバーセキュリティ市場における技術の影響
技術進歩は、脅威と防御の両面において、世界のサイバーセキュリティの状況に大きな影響を与えています。生成AIやその他の新技術の急速な普及は、サイバー攻撃者に容易に利用され、企業や公共生活に深刻な脅威をもたらしています。ディープフェイクや洗練されたフィッシングキャンペーンは、民主主義のプロセスを混乱させる武器となる可能性を秘めています。同時に、サイバーセキュリティの防御を強化するために、新たなテクノロジーが活用されつつあります。人工知能 (AI) と機械学習 (ML) は、膨大な量のデータを分析し、パターンから学習し、潜在的な脅威について予測を行うことで、業界に革命をもたらしています。行動バイオメトリクスは、MLアルゴリズムを使用してユーザーの行動を分析し、アカウントに不正アクセスしたハッカーなどの潜在的脅威を検出します。いくつかの重要な技術が、世界のサイバーセキュリティ防衛に大きな影響を与えています。ゼロトラスト・アーキテクチャはその最前線にあり、ネットワークやリソースにアクセスしようとするすべての人やデバイスに対して厳格な本人確認を要求し、デフォルトでは誰も信用できないという原則に基づいて運用されています。ブロックチェーン技術もまた、機密情報を安全に保管するための分散型データベースを提供することで、サイバーセキュリティを変革しています。量子コンピューティングはまだ初期段階ですが、より安全な暗号化方法を可能にすることで、サイバーセキュリティに革命を起こす可能性を秘めています。さらに、多要素認証・暗号化・アクセス制御などのクラウドセキュリティ技術は、クラウド環境におけるデータの保護に不可欠です。これらの技術が進歩するにつれて、世界のサイバーセキュリティ防衛の状況はますます形作られていくと思われます。
世界のサイバーセキュリティ市場の主な促進要因
いくつかの重要な要因が、世界のサイバーセキュリティ防衛市場の成長を促進しています。サイバー脅威の増加は主要な促進要因であり、サイバー攻撃の頻度と複雑性は近年世界的に上昇しています。こうしたインシデントは、多額の金銭的損失、風評被害、法的責任につながる可能性があります。政府や業界団体は、欧州連合 (EU) の一般データ保護規則 (GDPR) など、データのプライバシーとセキュリティに関する規制を強化しています。組織は、厳しい罰金や法的結果を避けるために、これらの規制を遵守しなければなりません。また、モノのインターネット (IoT) の急速なデジタル化と普及は、サイバー犯罪者の攻撃対象領域を拡大し、脆弱性とデータ侵害のリスクを高めています。地政学的な緊張はサイバーセキュリティの状況にさらに影響を与えます。紛争や不安定な状況はリスク力学を急速に変化させ、サイバー攻撃はしばしば戦争の道具として重要インフラやサプライチェーンを標的にすることがあるからです。さらに、個人・組織・政府の間でサイバーセキュリティの重要性に対する認識が高まっており、デジタル資産を保護し、デジタルエコシステムの信頼を維持するための取り組みが強化されています。このような市場促進要因は、今後数年間も世界のサイバーセキュリティ防衛市場の成長を推進すると予想されます。
世界のサイバーセキュリティ市場の地域別動向
世界のサイバーセキュリティ防衛市場は、さまざまな脅威情勢、規制環境、投資の優先順位によって形成された、明確な地域別動向を示しています。北米は、技術の進歩、高度な接続ソリューションに対する高い需要、防衛・航空宇宙分野への多額の投資によって市場をリードしています。米国とカナダは、確立された規制フレームワークと宇宙・衛星イニシアティブへの支援から恩恵を受け、同地域の市場優位性を高めています。欧州では、一般データ保護規則 (GDPR) などの厳格なデータプライバシー規制が、高度なサイバーセキュリティ技術と戦略の採用に拍車をかけています。欧州連合 (EU) はまた、新たな脅威に先んじるため、研究開発に多額の投資を行っています。アジア太平洋地域では、デジタル技術の導入が進み、サイバー脅威に対する意識が高まっていることが背景にあり、サイバーセキュリティ防衛市場が急成長しています。中国やインドのような国々は、重要な資産を保護し、経済の安定を維持するために、サイバーセキュリティインフラに多額の投資を行っています。中東・アフリカ地域では、リソースや専門知識が限られているため、サイバーセキュリティ防衛において顕著な課題に直面しています。しかし、国益を守り、海外からの投資を呼び込むためのサイバーセキュリティの重要性に対する認識は高まっています。このような世界の動向は、複雑で進化するサイバーセキュリティの脅威の状況に対処するための、世界で協調的なアプローチの必要性を浮き彫りにしています。
サイバーセキュリティの主要プログラム
Accenture Federal Servicesは、米国海軍の海上部隊がSHARKCAGE環境内で統合サイバーセキュリティ作戦を実施するのを支援するため、10年間で7億8,900万米ドルの契約を獲得しました。この契約でAccenture Federal Servicesは、陸上・艦載のSHARKCAGEシステムを提供することで、海軍の指揮・制御・通信・コンピューター・情報プログラム・マネージャー、戦争サイバーセキュリティ担当プログラム・エグゼクティブ・オフィスを支援します。これらのシステムは、市販および既製のハードウェアとソフトウェアで構成され、InformationTechnology-21、ONENet、海軍/海兵隊イントラネットなどの海軍ネットワークに防御的なサイバー空間操作分析を提供するように設計されています。同社の責任には、これらのシステムのシステム設計、アーキテクチャ、テスト、生産、納入、設置サポート、統合ロジスティクス・サポートが含まれます。
CACI International Inc.は、米国陸軍戦闘能力開発司令部 (CCDC) のC5ISR (指揮、制御、コンピュータ、通信、サイバー、諜報・監視・偵察) センターから5年間の単発タスクオーダーを獲得したと発表しました。このタスクオーダーは、上限額4億6,500万米ドル以上で、暗号の近代化、情報セキュリティ、戦術的ネットワーク保護の研究開発に重点を置いています。GSA Alliant II契約の下、陸軍のサイバーセキュリティ・情報部門 (CSIA) から授与されたCACIは、C5ISRシステムのサイバー防衛能力を強化するための専門知識を提供します。
目次
市場の定義
市場の内訳
- コンポーネント別
- 地域別
- セキュリティの種類別
市場の展望 (今後10年間分)
マーケットテクノロジー
世界市場の予測
地域別の動向と予測
- 北米
- 促進・抑制要因、課題
- PEST分析
- 市場予測とシナリオ分析
- 主要企業
- サプライヤー階層の情勢
- 企業のベンチマーク
- 欧州
- 中東
- アジア太平洋
- 南米
国別分析
- 米国
- 防衛計画
- 最新動向
- 特許
- この市場における現在の技術成熟レベル
- 市場予測とシナリオ分析
- カナダ
- イタリア
- フランス
- ドイツ
- オランダ
- ベルギー
- スペイン
- スウェーデン
- ギリシャ
- オーストラリア
- 南アフリカ
- インド
- 中国
- ロシア
- 韓国
- 日本
- マレーシア
- シンガポール
- ブラジル
市場機会マトリックス
専門家の見解
結論
Aviation and Defense Market Reportsについて
List of Tables
- Table 1: 10 Year Market Outlook, 2022-2032
- Table 2: Drivers, Impact Analysis, North America
- Table 3: Restraints, Impact Analysis, North America
- Table 4: Challenges, Impact Analysis, North America
- Table 5: Drivers, Impact Analysis, Europe
- Table 6: Restraints, Impact Analysis, Europe
- Table 7: Challenges, Impact Analysis, Europe
- Table 8: Drivers, Impact Analysis, Middle East
- Table 9: Restraints, Impact Analysis, Middle East
- Table 10: Challenges, Impact Analysis, Middle East
- Table 11: Drivers, Impact Analysis, APAC
- Table 12: Restraints, Impact Analysis, APAC
- Table 13: Challenges, Impact Analysis, APAC
- Table 14: Drivers, Impact Analysis, South America
- Table 15: Restraints, Impact Analysis, South America
- Table 16: Challenges, Impact Analysis, South America
- Table 17: Scenario Analysis, Scenario 1, By Region, 2022-2032
- Table 18: Scenario Analysis, Scenario 1, By Component, 2022-2032
- Table 19: Scenario Analysis, Scenario 1, By Security Type, 2022-2032
- Table 20: Scenario Analysis, Scenario 2, By Region, 2022-2032
- Table 21: Scenario Analysis, Scenario 2, By Component, 2022-2032
- Table 22: Scenario Analysis, Scenario 2, By Security Type, 2022-2032
List of Figures
- Figure 1: Global Cybersecurity Market Forecast, 2022-2032
- Figure 2: Global Cybersecurity Market Forecast, By Region, 2022-2032
- Figure 3: Global Cybersecurity Market Forecast, By Component, 2022-2032
- Figure 4: Global Cybersecurity Market Forecast, By Security Type, 2022-2032
- Figure 5: North America, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 6: Europe, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 7: Middle East, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 8: APAC, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 9: South America, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 10: United States, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 11: United States, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 12: Canada, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 13: Canada, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 14: Italy, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 15: Italy, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 16: France, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 17: France, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 18: Germany, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 19: Germany, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 20: Netherlands, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 21: Netherlands, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 22: Belgium, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 23: Belgium, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 24: Spain, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 25: Spain, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 26: Sweden, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 27: Sweden, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 28: Brazil, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 29: Brazil, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 30: Australia, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 31: Australia, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 32: India, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 33: India, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 34: China, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 35: China, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 36: Saudi Arabia, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 37: Saudi Arabia, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 38: South Korea, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 39: South Korea, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 40: Japan, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 41: Japan, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 42: Malaysia, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 43: Malaysia, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 44: Singapore, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 45: Singapore, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 46: United Kingdom, Cybersecurity Market, Technology Maturation, 2022-2032
- Figure 47: United Kingdom, Cybersecurity Market, Market Forecast, 2022-2032
- Figure 48: Opportunity Analysis, Cybersecurity Market, By Region (Cumulative Market), 2022-2032
- Figure 49: Opportunity Analysis, Cybersecurity Market, By Region (CAGR), 2022-2032
- Figure 50: Opportunity Analysis, Cybersecurity Market, By Component (Cumulative Market), 2022-2032
- Figure 51: Opportunity Analysis, Cybersecurity Market, By Component (CAGR), 2022-2032
- Figure 52: Opportunity Analysis, Cybersecurity Market, By Security Type (Cumulative Market), 2022-2032
- Figure 53: Opportunity Analysis, Cybersecurity Market, By Security Type (CAGR), 2022-2032
- Figure 54: Scenario Analysis, Cybersecurity Market, Cumulative Market, 2022-2032
- Figure 55: Scenario Analysis, Cybersecurity Market, Global Market, 2022-2032
- Figure 56: Scenario 1, Cybersecurity Market, Total Market, 2022-2032
- Figure 57: Scenario 1, Cybersecurity Market, By Region, 2022-2032
- Figure 58: Scenario 1, Cybersecurity Market, By Component, 2022-2032
- Figure 59: Scenario 1, Cybersecurity Market, By Security Type, 2022-2032
- Figure 60: Scenario 2, Cybersecurity Market, Total Market, 2022-2032
- Figure 61: Scenario 2, Cybersecurity Market, By Region, 2022-2032
- Figure 62: Scenario 2, Cybersecurity Market, By Component, 2022-2032
- Figure 63: Scenario 2, Cybersecurity Market, By Security Type, 2022-2032
- Figure 64: Company Benchmark, Cybersecurity Market, 2022-2032
The Global Cybersecurity Market is estimated at USD 175 billion in 2024, projected to grow to USD 300 billion by 2034 at a Compound Annual Growth Rate (CAGR) of 5.54% over the forecast period 2024-2034

Introduction to Global Cybersecurity Market:
Global Cybersecurity Defense refers to the collective efforts of nations, organizations, and individuals to protect digital assets, critical infrastructure, and sensitive information from cyber threats. In an increasingly interconnected world, cybersecurity has become a top priority for governments and businesses alike. Cybersecurity is essential for safeguarding against malicious attacks by hackers, spammers, and cybercriminals who aim to access, change, or destroy sensitive information; extort money; or disrupt normal operations. These threats have become more sophisticated and widespread, with cybercrime. As a result, governments and organizations are investing heavily in advanced cybersecurity technologies and strategies to protect their digital assets and maintain the trust of their stakeholders.
Technology Impact in Global Cybersecurity Market:
Technological advancements have had a significant impact on the global cybersecurity landscape, both in terms of the threats and the defenses. The rapid spread of generative AI and other new technologies can easily be used by cyberattackers, posing a serious threat to businesses and public life[3]. Deepfakes and sophisticated phishing campaigns have the potential to become weaponized to disrupt democratic processes. At the same time, emerging technologies are being leveraged to enhance cybersecurity defenses. Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing the industry by analyzing vast amounts of data, learning from patterns, and making predictions about potential threats[5]. Behavioral biometrics uses ML algorithms to analyze user behavior and detect potential threats, such as hackers who have gained unauthorized access to an account. Several key technologies are significantly impacting global cybersecurity defense. Zero Trust Architecture is at the forefront, requiring rigorous identity verification for every person or device attempting to access a network or resource, operating on the principle that no one is trusted by default. Blockchain technology is also transforming cybersecurity by offering a decentralized database for securely storing sensitive information, which greatly complicates unauthorized access for hackers. Quantum Computing, though still in its early stages, holds the potential to revolutionize cybersecurity by enabling more secure encryption methods. Additionally, Cloud Security technologies, such as multi-factor authentication, encryption, and access controls, are crucial for safeguarding data in cloud environments. As these technologies advance, they will increasingly shape the global cybersecurity defense landscape.
Key Drivers in Global Cybersecurity Market:
Several key factors are driving the growth of the global cybersecurity defense market. Increasing cyber threats are a primary driver, with the frequency and complexity of cyberattacks rising globally in recent years. These incidents can lead to significant financial losses, reputational damage, and legal liabilities. Another crucial factor is regulatory compliance; governments and industry bodies are enforcing stricter regulations on data privacy and security, such as the General Data Protection Regulation (GDPR) in the European Union. Organizations must adhere to these regulations to avoid severe fines and legal consequences. The rapid digitalization and proliferation of the Internet of Things (IoT) are also expanding the attack surface for cybercriminals, increasing the risk of vulnerabilities and data breaches. Geopolitical tensions further impact the cybersecurity landscape, as conflicts and instability can shift risk dynamics quickly, with cyberattacks often targeting critical infrastructure and supply chains as tools of warfare. Additionally, growing awareness among individuals, organizations, and governments about the importance of cybersecurity is enhancing efforts to protect digital assets and maintain trust in the digital ecosystem. These drivers are expected to continue propelling the growth of the global cybersecurity defense market in the coming years.
Regional Trends in Global Cybersecurity Market:
The global cybersecurity defense market displays distinct regional trends, shaped by varying threat landscapes, regulatory environments, and investment priorities. North America leads the market, driven by technological advancements, a high demand for advanced connectivity solutions, and substantial investments in defense and aerospace sectors. The U.S. and Canada benefit from well-established regulatory frameworks and support for space and satellite initiatives, bolstering the region's market dominance. In Europe, strict data privacy regulations, such as the General Data Protection Regulation (GDPR), are fueling the adoption of advanced cybersecurity technologies and strategies. The European Union is also investing heavily in research and development to stay ahead of emerging threats. The Asia-Pacific region is experiencing rapid growth in the cybersecurity defense market, driven by the increasing adoption of digital technologies and a heightened awareness of cyber threats. Countries like China and India are significantly investing in cybersecurity infrastructure to protect their critical assets and maintain economic stability. In the Middle East and Africa, the region faces notable challenges in cybersecurity defense due to limited resources and expertise. However, there is growing recognition of the importance of cybersecurity for protecting national interests and attracting foreign investment. These regional trends underscore the need for a global, coordinated approach to address the complex and evolving cybersecurity threat landscape.
Key Cybersecurity market programs:
Accenture Federal Services has secured a ten-year, $789 million contract to assist U.S. Navy maritime forces in executing unified cybersecurity operations within the SHARKCAGE environment, the Navy's integrated system designed to safeguard a continuous, unified security perimeter. Under this contract, Accenture Federal Services will support the Navy's Program Executive Office for Command, Control, Communications, Computers and Intelligence Program Manager, Warfare Cybersecurity, by providing both shore-based and shipborne SHARKCAGE systems. These systems, comprising commercial and off-the-shelf hardware and software, are designed to deliver defensive cyberspace operations analytics across Navy networks such as InformationTechnology-21, ONENet, and the Navy/Marine Corps Intranet. The company's responsibilities will include system design, architecture, testing, production, delivery, installation support, and integrated logistics support for these systems.
CACI International Inc. announced that it has secured a five-year, single-award task order from the U.S. Army Combat Capabilities Development Command's (CCDC) Command, Control, Computers, Communications, Cyber, Intelligence, Surveillance, and Reconnaissance (C5ISR) center. The task order, with a ceiling value of over $465 million, focuses on research and development in cryptographic modernization, information security, and tactical network protection. Awarded by the Army's Cyber Security and Information Division (CSIA) under the GSA Alliant II contract vehicle, CACI will provide specialized expertise to enhance cyber defense capabilities for C5ISR systems.
Table of Contents
Market Definition
Market Segmentation
By Component
By Region
By Security Type
10 Year Market Outlook
The 10-year market outlook would give a detailed overview of changing dynamics, technology adoption overviews and the overall market attractiveness is covered in this chapter.
Market Technologies
This segment covers the top 10 technologies that is expected to impact this market and the possible implications these technologies would have on the overall market.
Global Market Forecast
The 10-year market forecast of this market is covered in detailed across the segments which are mentioned above.
Regional Market Trends & Forecast
The regional market trends, drivers, restraints and Challenges of this market, the Political, Economic, Social and Technology aspects are covered in this segment. The market forecast and scenario analysis across regions are also covered in detailed in this segment. The last part of the regional analysis includes profiling of the key companies, supplier landscape and company benchmarking.
North America
Drivers, Restraints and Challenges
PEST
Market Forecast & Scenario Analysis
Key Companies
Supplier Tier Landscape
Company Benchmarking
Europe
Middle East
APAC
South America
Country Analysis
This chapter deals with the key defense programs in this market, it also covers the latest news and patents which have been filed in this market. Country level 10 year market forecast and scenario analysis are also covered in this chapter.
US
Defense Programs
Latest News
Patents
Current levels of technology maturation in this market
Market Forecast & Scenario Analysis
Canada
Italy
France
Germany
Netherlands
Belgium
Spain
Sweden
Greece
Australia
South Africa
India
China
Russia
South Korea
Japan
Malaysia
Singapore
Brazil
Opportunity Matrix
The opportunity matrix helps the readers understand the high opportunity segments in this market.
Expert Opinions
Hear from our experts their opinion of the possible outlook for this market.
Conclusions
About Aviation and Defense Market Reports


